To test the RADIUS authentication, we will use F5 BIG-IP Portal Access as a example.
Configure a remote access connection to one or more internal web applications. Create an access policy and local traffic virtual server so that end users can access internal web applications through a single external virtual server. Use this if you need to provide secure extranet access to internal web applications without creating a full VPN connection.
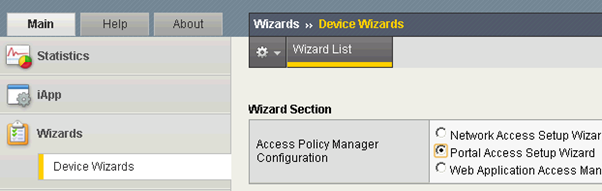
Select “Device Wizards” in the Main tab:
then select “Portal Access Setup Wizard”:
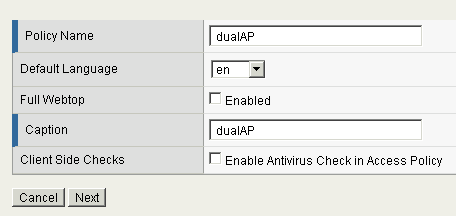
Enter the Policy Name. Click “Next”
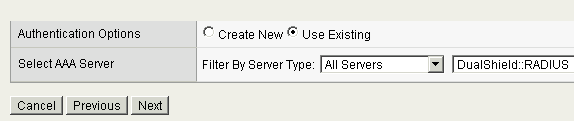
Select the “Use Existing” in the Authentication Option.
Select the DualShield RADIUS server registered in the previous step.
Click “Next”
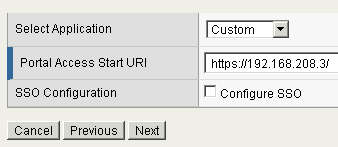
On this page you need to enter the details of your web application and its URI.
Click “Next”
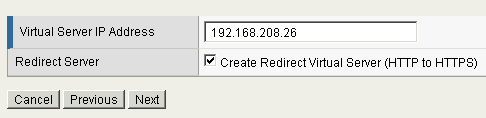
Enter the IP of a virtual server
Click “Next”
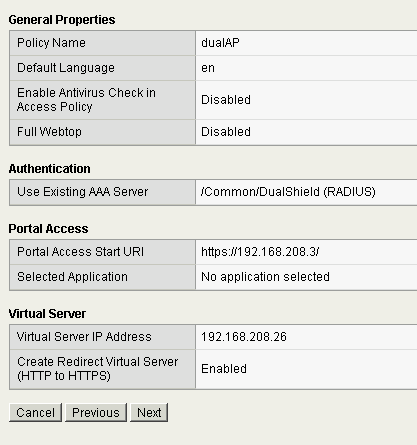
This is the final review page. Make sure all details are correct and click “Next” to finish the wizard.
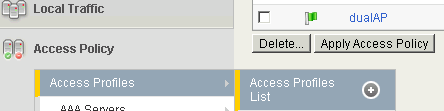
You can now view the Access Profile we just created in Access Profiles List:
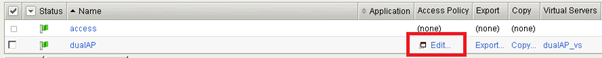
To edit the Access Policy, click ”Edit”
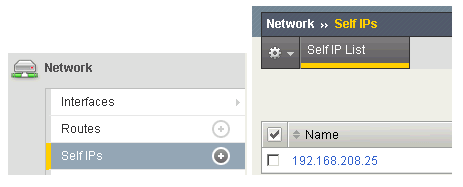
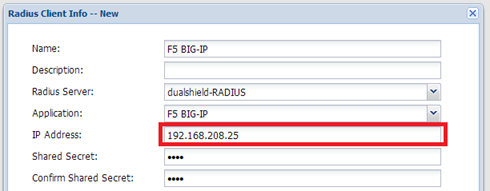
Finally, it is worthwhile pointing out that the IP of the Radius Client registered in DualShield must be the BIG-IP’s Self IP, not the virtual server IP.
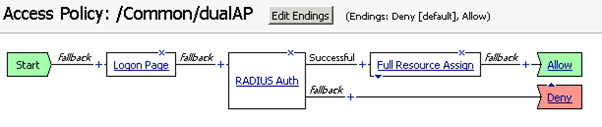
Now, we are ready to carry out the test.
Navigate to your BIG-IP’s virtual server address, e.g.
https://bigip-sp.deepnetsecurity.local/
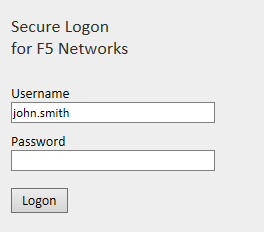
The Logon Page is presented:
In the Password field, enter the user’s AD password followed by a OTP passcode, if the logon procedure defined in the DualShield is “Static Passwprd + One-Time-Password":