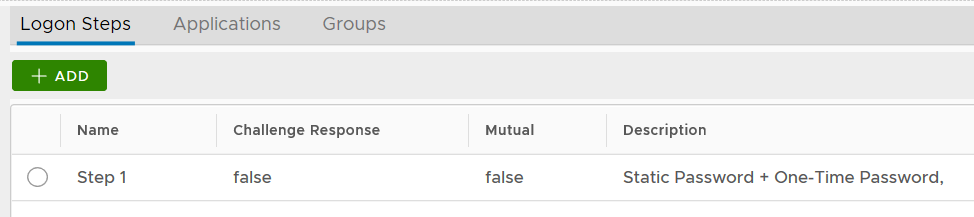
Traditional VPN clients do not support two-factor authentication. In order to provide two-factor authentication without changing the VPN client, the common practise is to concatenate passwords from both factors, i.e. Account Password (Static Password) and One-Time Password (OTP), to form a type of new password called “passcode”. DualShield provides and supports the following types of passcodes:
- Static Password
- One-Time Password
- One-Time Password + Static Password
- Static Password + One-Time Password
For instances, if the user’s Static Password is “mypass” and the One-Time Password is “123456” then the passcode entered into the VPN client can be one of the following:
- mypass
- 123456
- 123456mypass
- mypass123456
To provide One-Step Logon you will create a logon procedure with only one logon step.
If you are planning to use on-demand password, e.g. Deepnet T-Pass, then you should consider deploying a Two-Step logon procedure. However, if you must use the on-demand password in a One-Step logon procedure because your VPN system does not support Challenge/Response then please refers to Appendix A.
NOTES
CHAP and MS-CHAP.v2 is not supported when the passcode consists of the AD password (Static Password). In other words, if the User Directory or Identity Source of a VPN application is an external AD or LDAP server, and the passcode is “Static Password”, “One-Time Password + Static Password” or “Static Password + One-Time Password”, then CHAP and MS-CHAP.v2 cannot be supported.
If you have to use CHAP or MS-CHAP v2, then the passcode should not include AD password, or the User Directory or Identity Source of the VPN application is created in the internal SQL server.