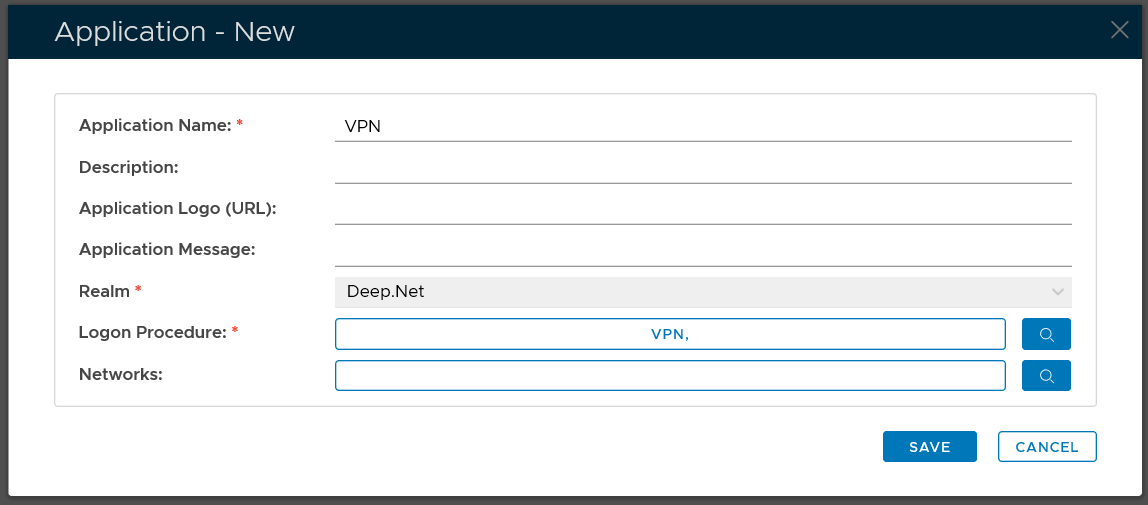
The majority of main stream VPN products, such as Cisco and Checkpoint etc, support RADIUS Challenge/Response authentication mode. We can utilize this feature to implement a two-step verification process for VPN logins.
The 2-step logon process will be as below:
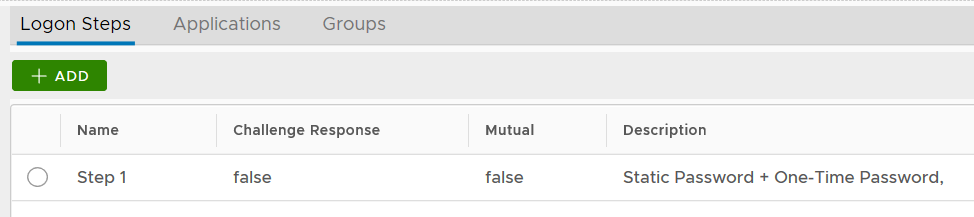
- Step 1: The VPN client will ask the user to enter their 1st credential, e.g. static password
- Step 1: The users enters their 1st credential.
- The server checks the validity of the user’s 1st credential.
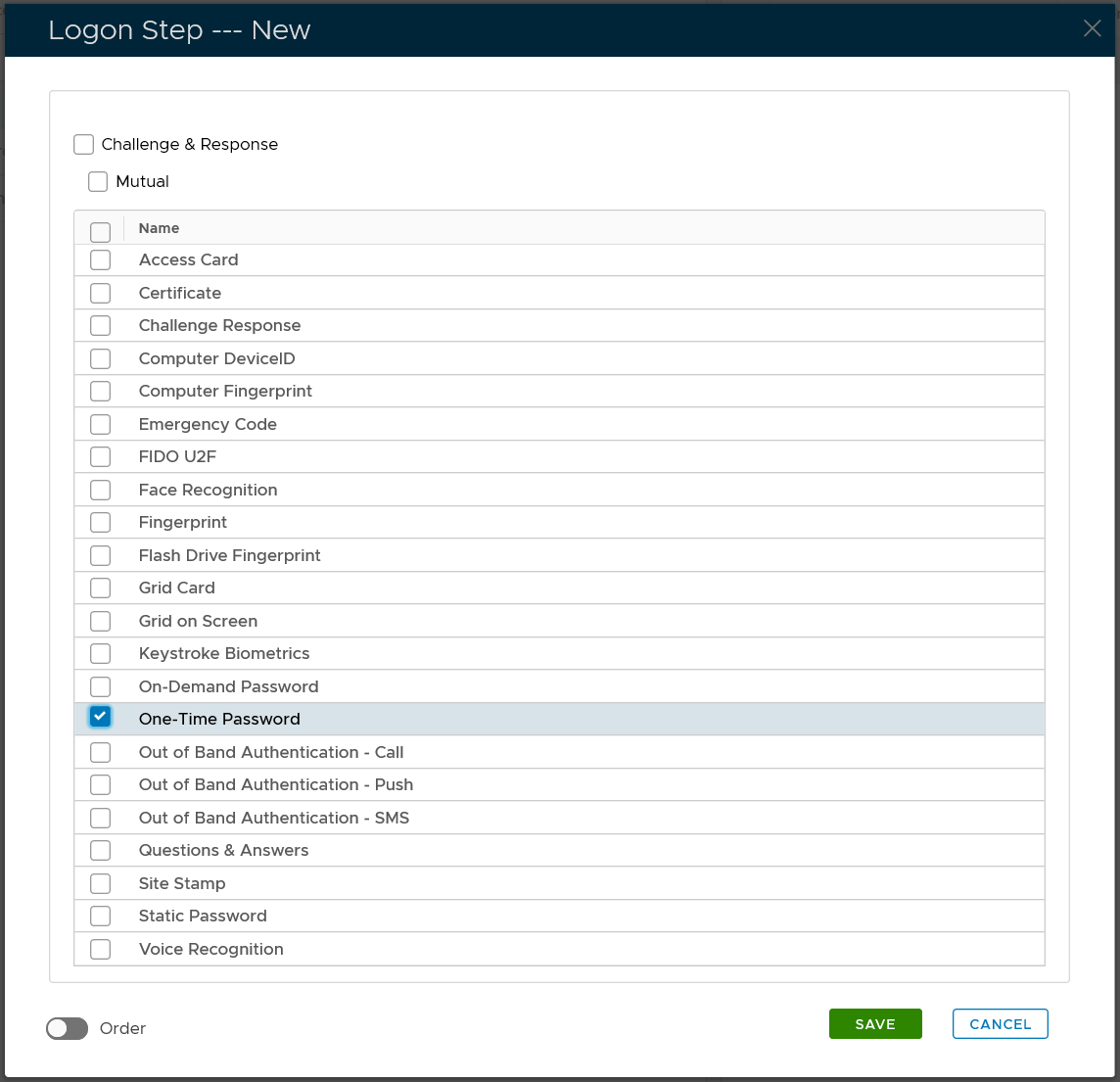
- Step 2: If the server successfully verified the user's static password, then it will prompt the user to enter the 2nd credential, e.g. one-time password.
- Step 2: The user enters their 2nd credential.
- The server checks the validity of the user’s 2nd credential.
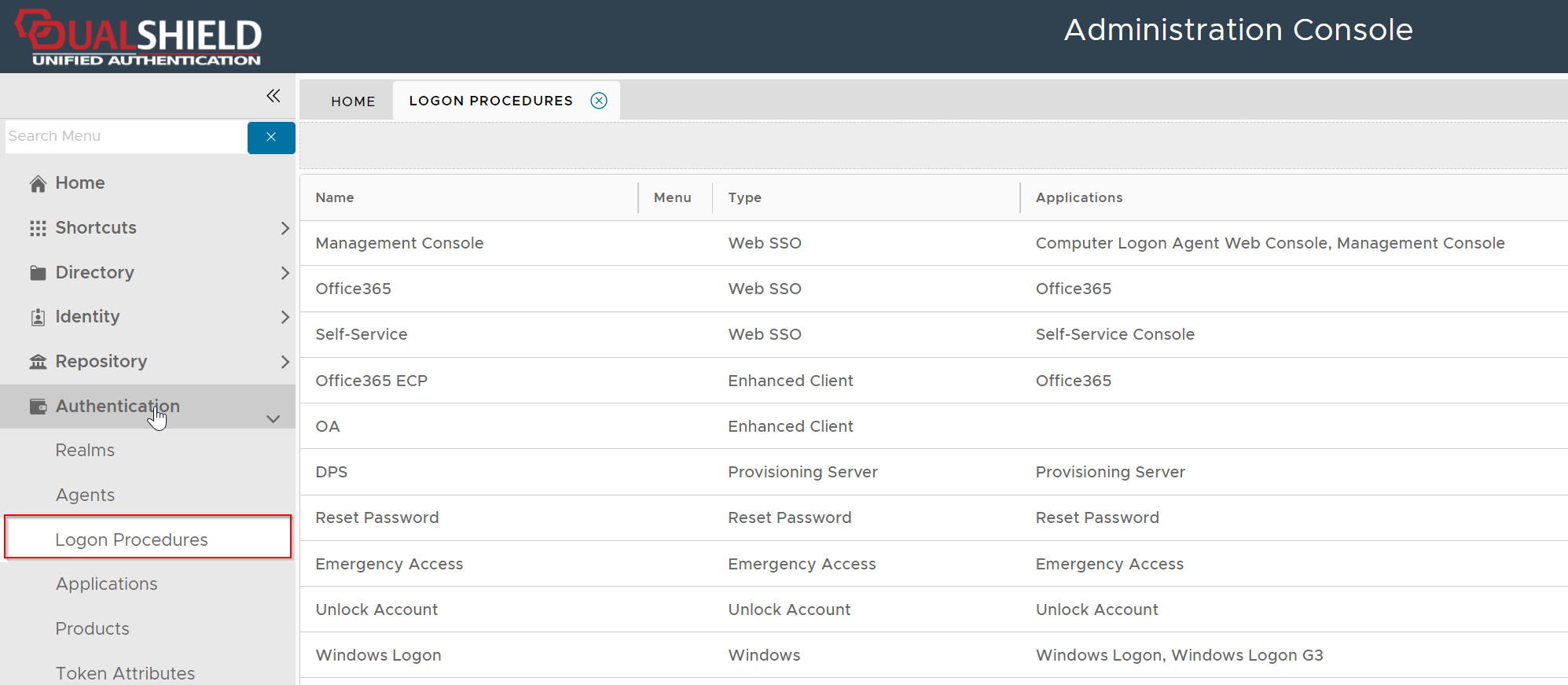
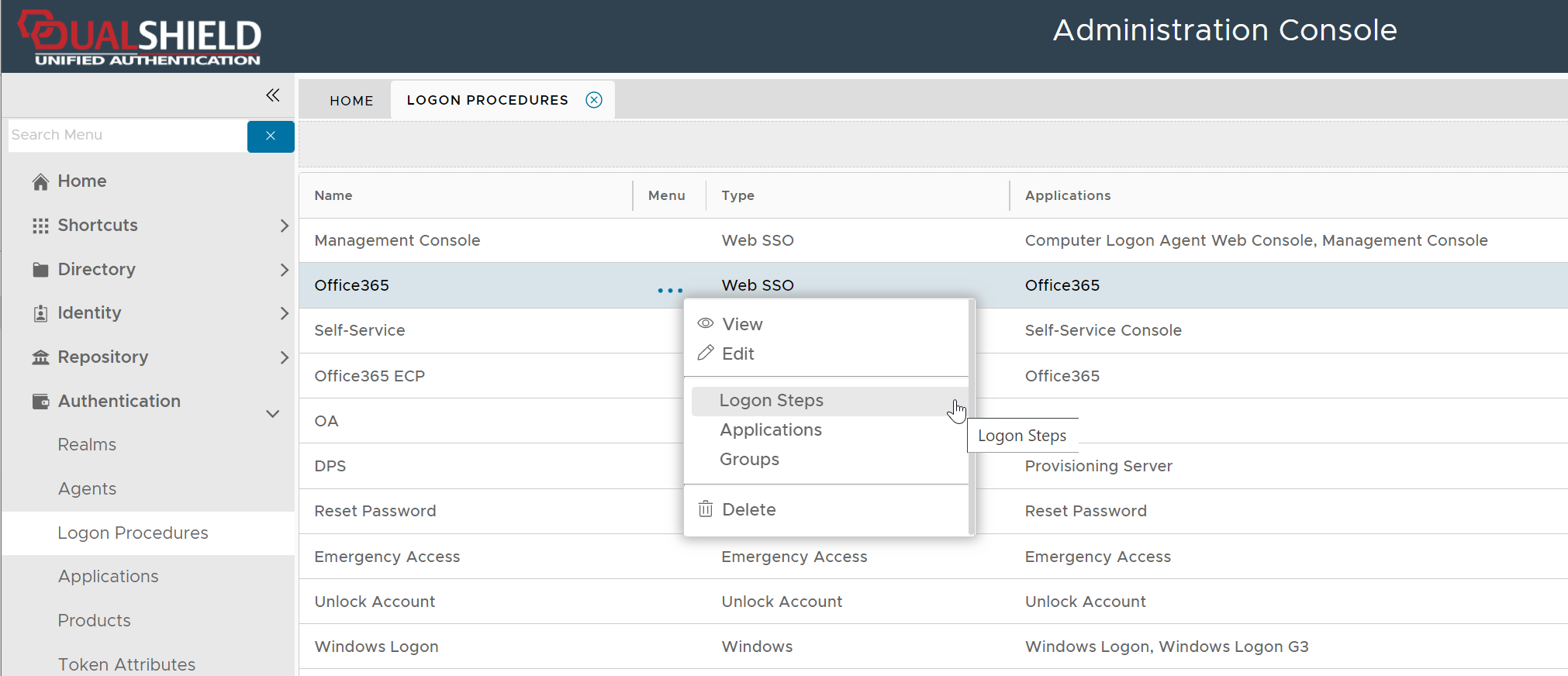
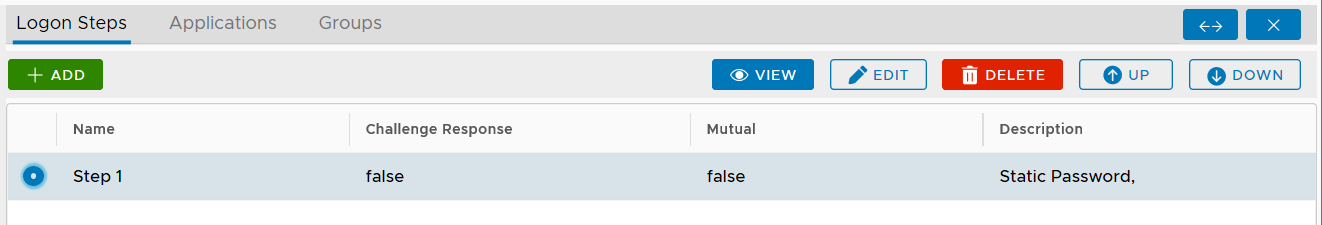
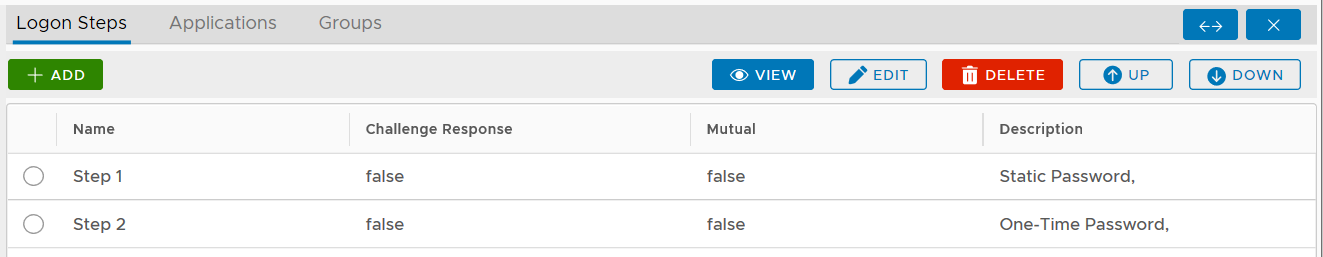
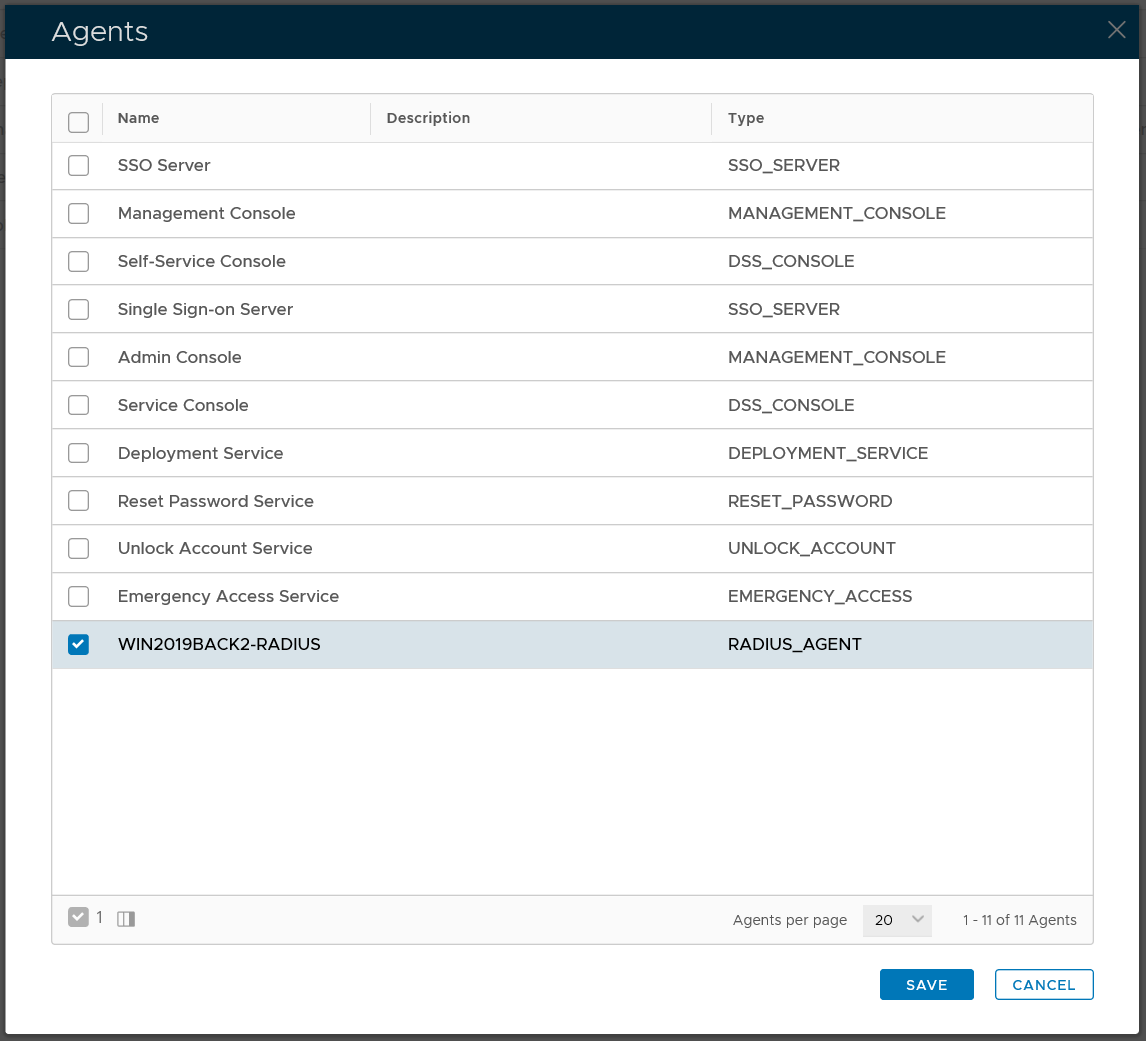
To provide Two-Step Logon, you will need to create a logon procedure with two logon steps.

NOTES
If you have a logon procedure with two or more logon steps, and you place more than one authenticator (including an on-demand password in a logon step), then the order of the authenticators is significant.
As soon as the server has successfully completed one step (the user has passed the step), the server will go through the authenticator list to the next step, one by one according to their order in the list. On each authenticator, it will check if the user has a token for this type of authenticator. If the user does not have a token of this type, then the authenticator is removed from the list.
If the first authenticator is an on-demand password, then the server will generate a password and send it out. If the first authenticator is an out of band anthentication, then the server will push out a logon request to the user's mobile phone.
Example:
A logon step has the following authenticators:
- One-Time Password
- On-Demand Password
User "A" has the following tokens
User "B" has the following tokens:
User "C" has the following tokens:
For User "A", the server will NOT send on-demand password, as the user has a MobileID which is listed to be preferred over T-Pass.
For User "B", the server will NOT send on-demand password, as there is no such token at all.
For User "C", the server WILL send on-demand password, as the user does not have MobileID but has the T-Pass.