Scope
You may have 3rd party contractors who need access to certain resources on your network. The aim is to limit the devices or networks these contractors have access to.
For example you may have various outside contractors , e.g Sales, Engineering, Construction, Electricians. who will need access to your network as well as their own, and therefore when remoting in they will only have the access they need, and only be redirected to the appropriate resource. This is achievable if DualShield is configured to return the relevant group name attribute.
Prerequisite Setup
You will begin by setting up the relevant security groups on AD and configuring ACL, Group policies and DAP settings on Cisco ASA. Please note that our knowledge on Cisco ASA is limited. We therefore expect you to already know how to set this up.
Setup DualShield Authentication Server to return RADIUS attributes
(This part of the document assumes you have already set up your DualShield RADIUS and Client configuration as specified in our Cisco ASA RADIUS Authentication Wiki guides: RADIUS Authentication for Cisco ASA )
In order to apply a group policy to the user login into VPN, a RADIUS attribute has to be returned from the DualShield RADIUS Server.
This can be achieved by logging on to the Management Console Selecting RADIUS→Radius Attributes from the menu at the top....
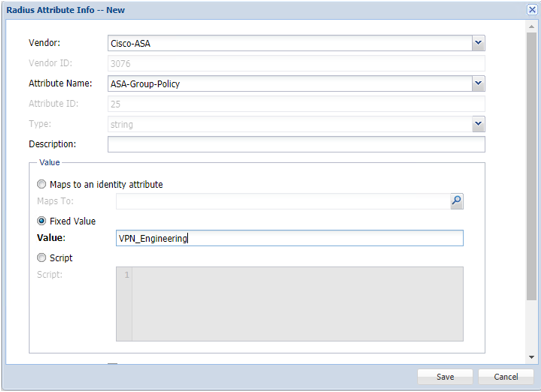
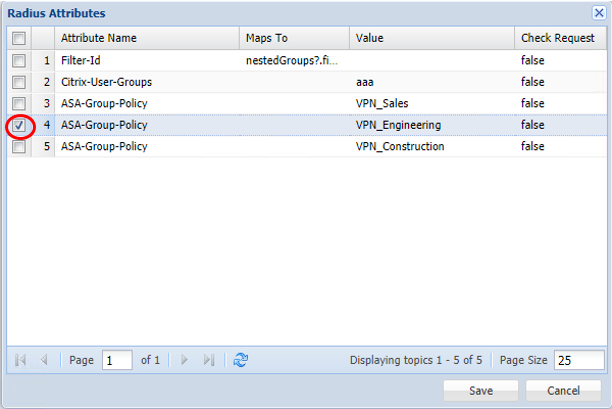
....and creating a new attribute profile that uses the ASA-Group-Policy to return the name of the Group which is specified as a fixed value:
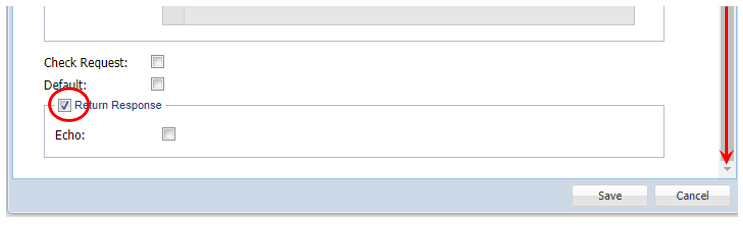
(Remember to scroll down to the bottom of this window and tick 'Return Response')
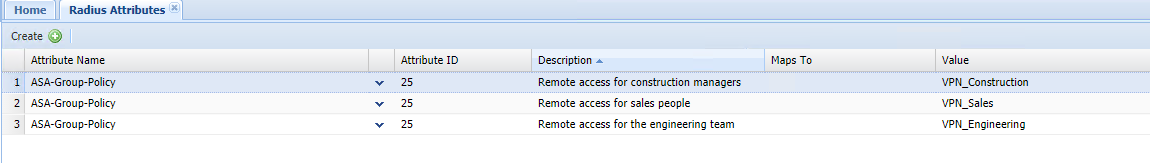
You can create an attribute profile to cater for each group policy you have set up on ASA.
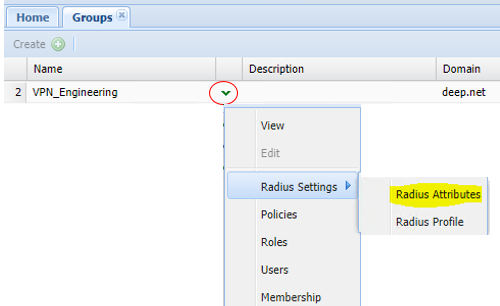
You will then need to assign each attribute to the relevant AD security group that the end user account will be a member of.
Assign each attribute profile to the relevant security group.
Troubleshooting
If you are encountering issues and you believe that DualShield is not returning the attributes as intended, there are some trouble shooting steps you need to take...
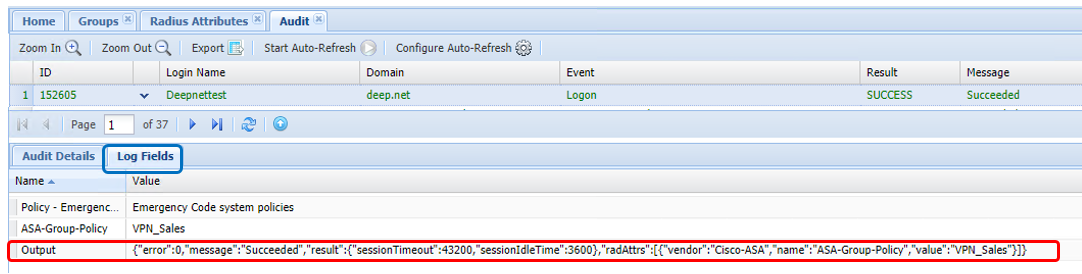
Step - 1 Check if the correct attribute is being returned:
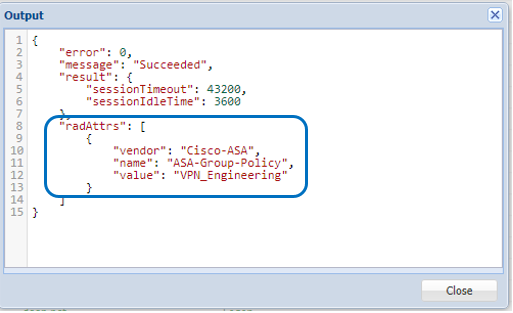
Check the Output log field for "radAttrs" in the DualShield Authentication Server Audit Logs
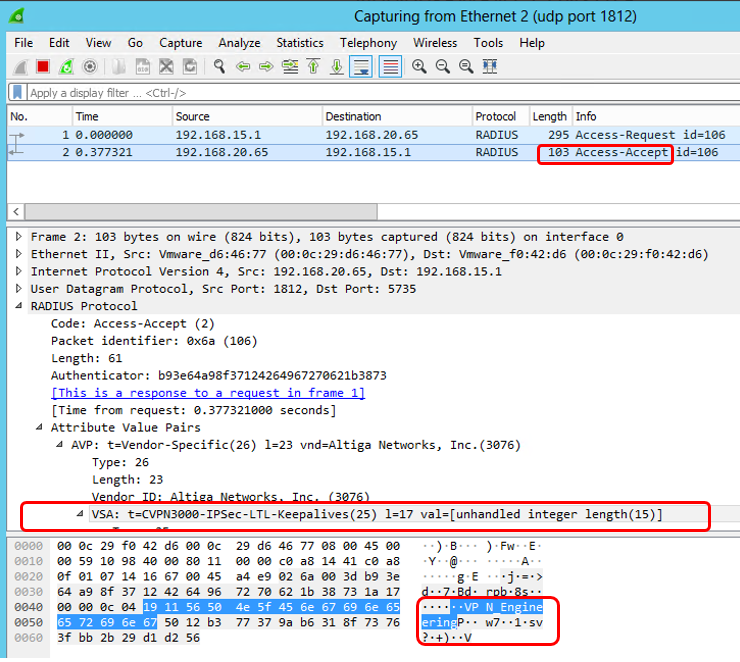
And you can also check using Wireshark. Set the capture filter to 'udp.port == 1812'
If the Attribute is not displaying then...
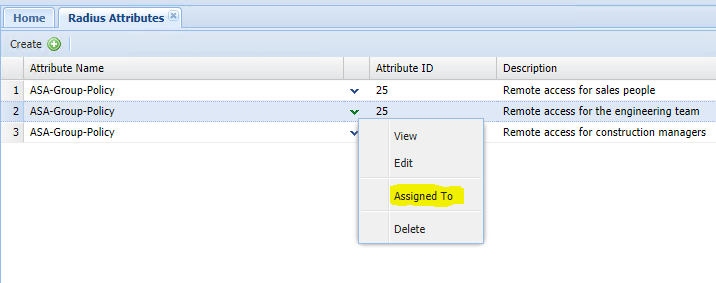
Step 2 - Recheck the 'Return Response' option under Radius Attributes is enabled.
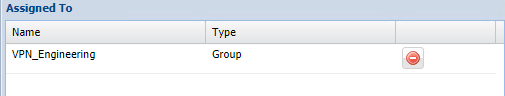
Step 3 - Make sure the Radius Attribute profile, is assigned to the correct group on DualShield:
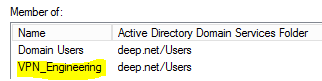
Step 4 - Double check to see if the end user's AD account is a member of the correct security group, on the domain controller.