If you plan to deploy only the one-time password based authentication in your user base using OTP tokens such as Deepnet SafeID, MobileID, then you will configure your Juniper VPN in such way that it will use your AD as the primary authentication server and your DualShield as the secondary authentication server. Your AD will be responsible for verifying users’ AD passwords and your DualShield will be responsible for verifying users’ one-time passwords only.
Edit Logon Procedure
In the DualShield Management Console, edit the logon procedure for your Juniper VPN application. You will only need one logon step and typically the logon step will have “One-Time Password” as the authentication method:
Configure Juniper VPN
- Under Authentication Servers set up an LDAP authentication server.
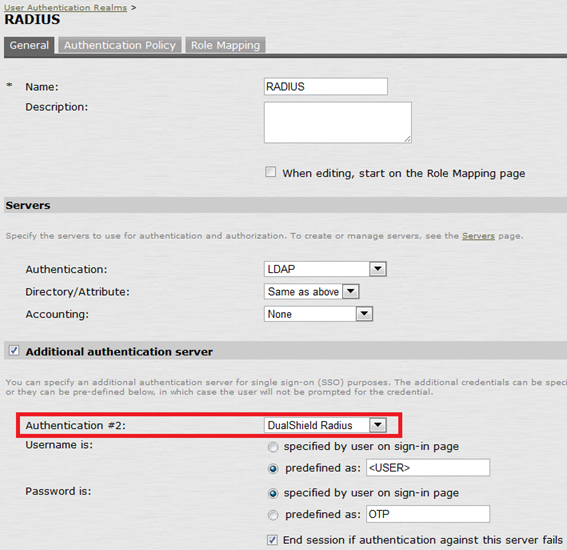
2. Edit User Authentication Realm
Set LDAP as the first authentication server and DualShield Radius as the second authentication server.
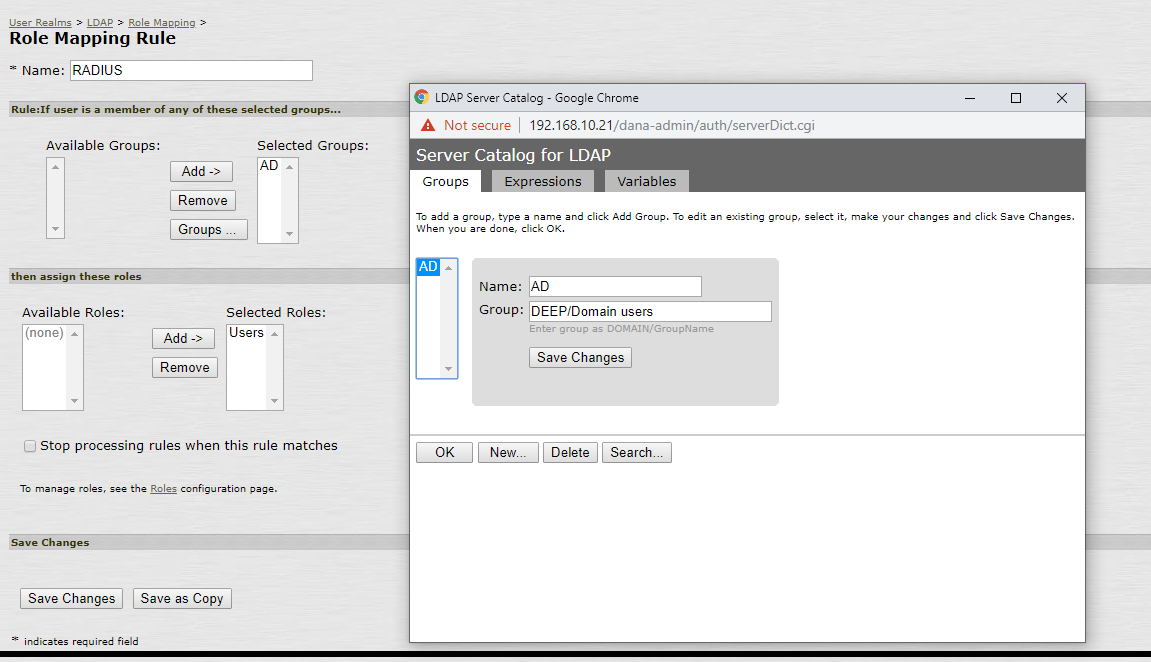
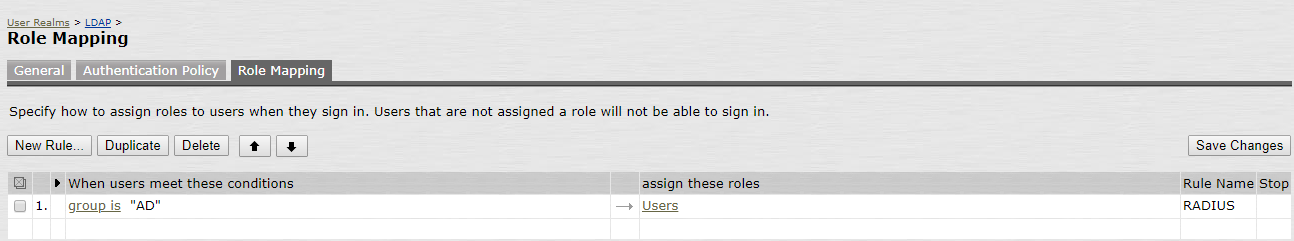
3. Define the Role Mapping, e.g.
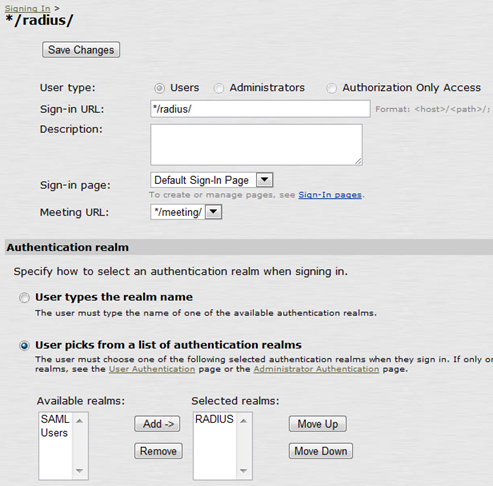
3. Under Signing In → Sign-in Policies create a new Signing URL:
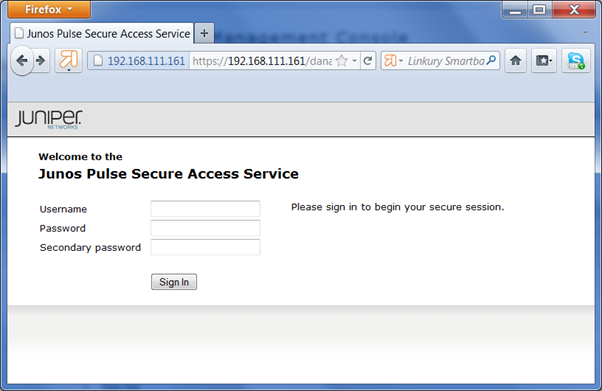
Test Logon
At logon, Juniper SA will present a logon form with the user name, password and the secondary password:
Enter your AD password in the "Password" field and an OTP in the "Secondary password" field.