his This guide describes how to add the Dualshield SSO as a SAML WS-Federation Claims Provider in the ADFS server.
| Table of Contents |
|---|
Add Claims Provider
Launch the ADFS Management console
...
Enter the Display Name for your DualShield SSOL server, e.g. "DualShield SSO"
Click Next
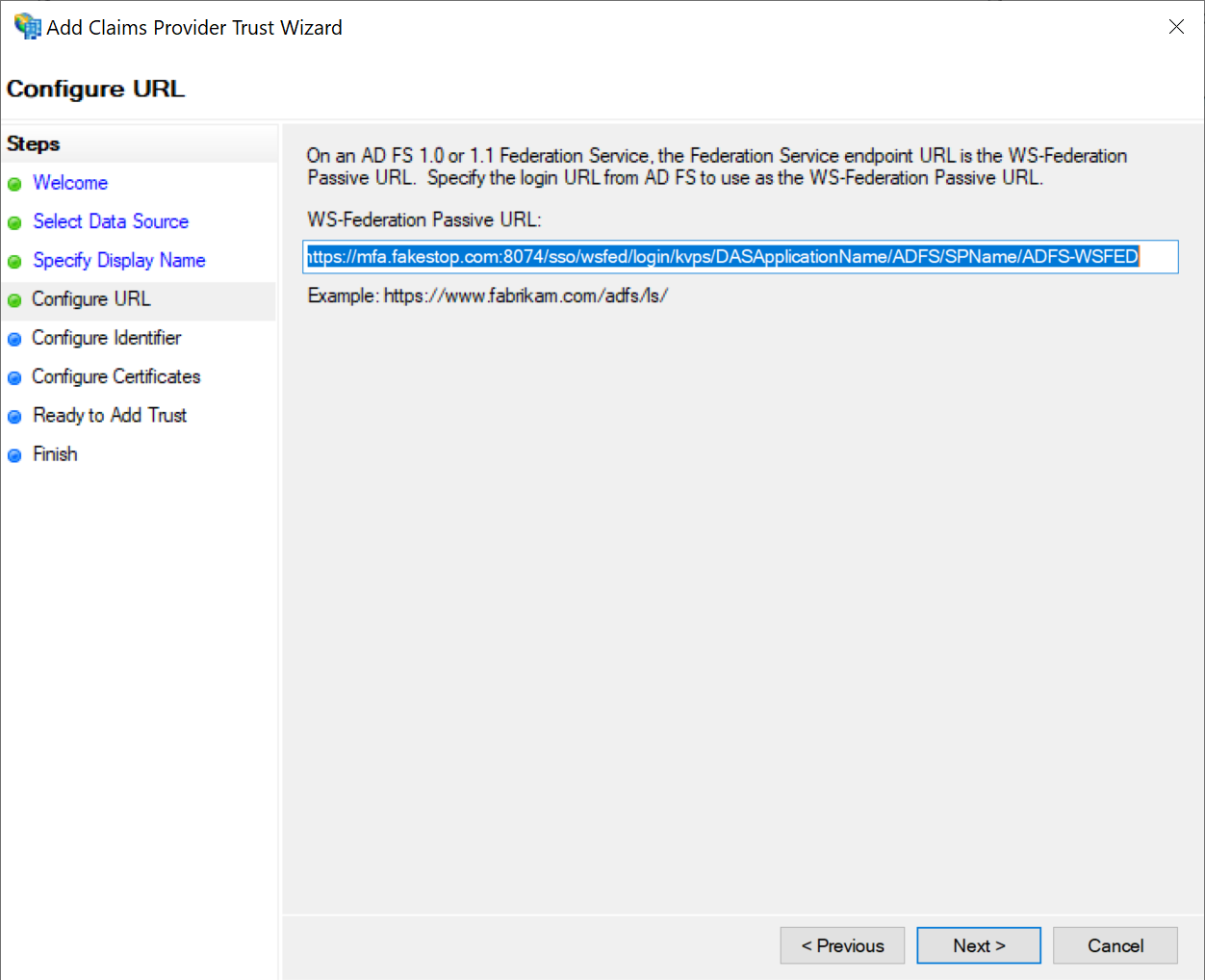
In the WS-Federation Passive URL box, enter the URL below:
https://{dualshield-sso-fqdn}:8074/sso/wsfed/login/kvps/DASApplicationName/{application-name}/SPName/{service-provide-name}
...
| Item | Meaning | Example |
|---|---|---|
| {dualshield-sso-fqdn} | the FQDN of your DualShield SSO server | mfa.fakestop.com |
| {application-name} | the name of the application that you will create in your DualShield for ADFS | ADFS |
{service-provider-name} | the name of the service provider that you will create in your DualShield for ADFS | ADFS-WSFED |
Example:
...
https://mfa.fakestop.com:8074/sso/wsfed/login/kvps/DASApplicationName/ADFS/SPName/ADFS-WSFED
Click Next to continue
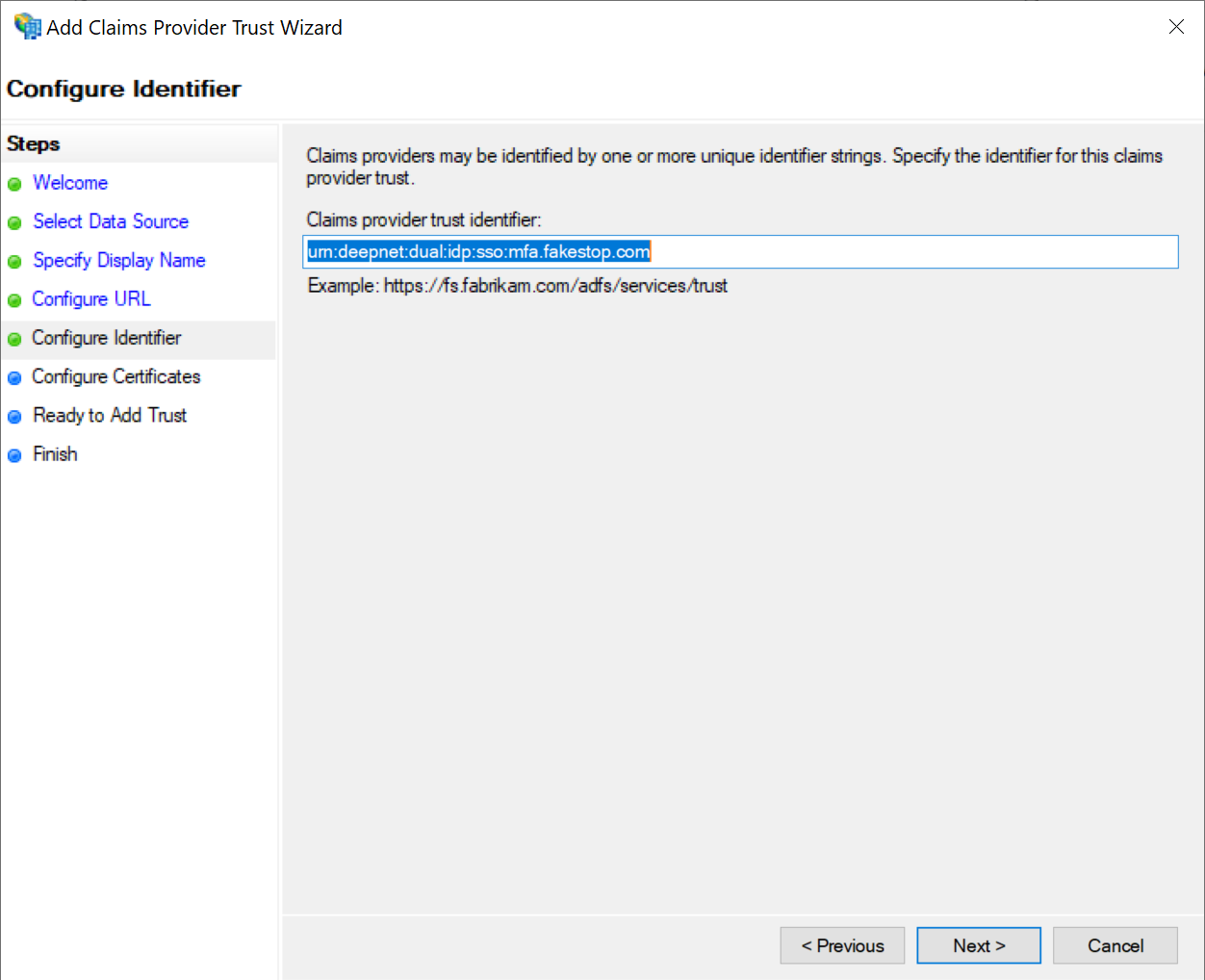
In the Claims provider trust identifier box, enter the Entity ID of your DualShield SSO server, e.g. urn:deepnet:dual:idp:sso:mfa.fakestop.com
| Expand | ||||||
|---|---|---|---|---|---|---|
| ||||||
|
Click Next
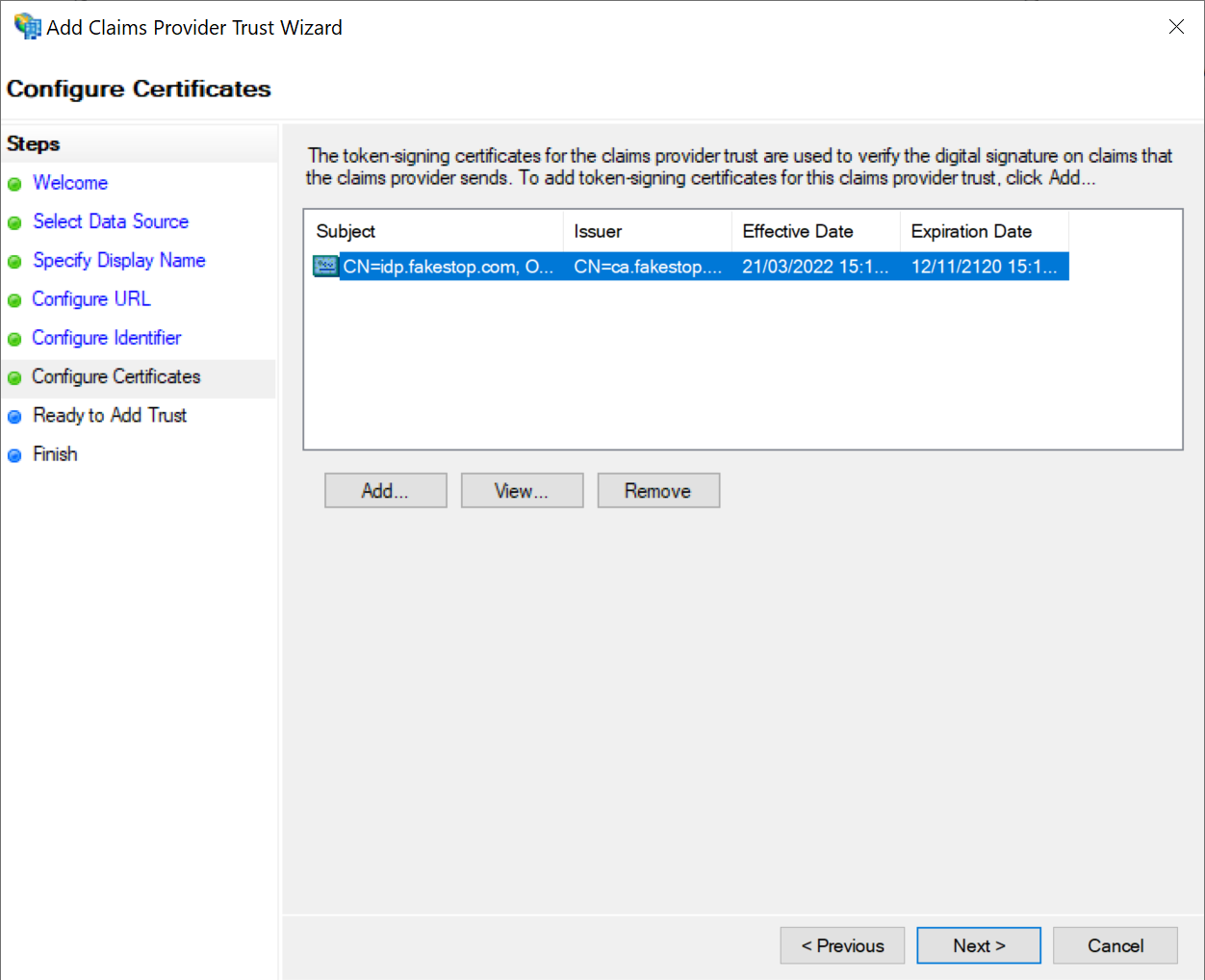
Click the Add button to import the IdP certificate of your DualShield SSO
| Expand | ||||||
|---|---|---|---|---|---|---|
| ||||||
|
Click Next
Click Next
Click Close
Configure Claims Provider
After the DualShield claims provider has been added, it needs to be configured
| Include Page | ||||
|---|---|---|---|---|
|