...
11. If configured correctly all the tests should pass, as below.
Create a SAML 2.0 Service Provider Configuration for Citrix Workspace.
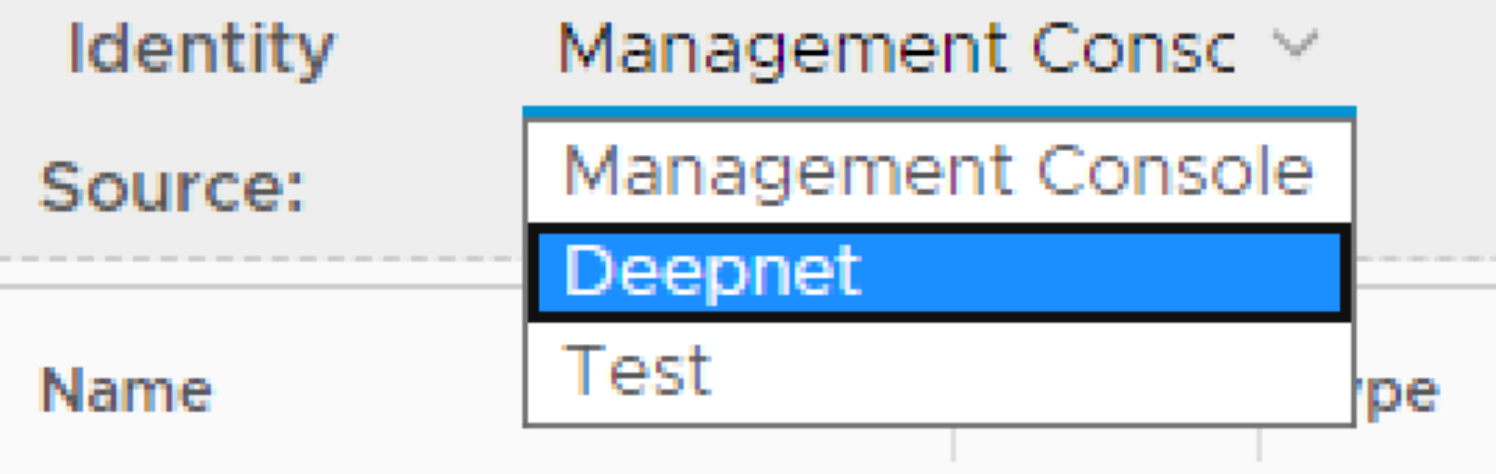
1. In the main menu, select Identity > Identity Attributes
2. Select the Identity Source that the domain you wish to use for authentication is bound to
3. Click on Create on the top right.
4. Create a new identity attribute called objectSid matching the settings as per screen shot below. Make sure the data type is set to Binary:
5. Click Save. You will now see the objectSid attribute listed under Identity Attributes…
6. Log into Citrix Cloud
7. Click on the menu icon on the top left.
8. Select Identity and Access Management from the drop-down menu, that appears:
9. Click on the Ellipsis (…) next to SAML and click Connect from the drop -down option.
10. On the Configure Saml page click next to SAML Metadata
11. On the DualShield Administration Console, select SSO > Service Providers.
12. Click Create
13. In the SSO Server field, select your DualShield SSO server from the list
14. In the Name field, enter the name for the Service Provider to be created
15. In the Type field, select SAML 2.0
- Click on
- Open the SAML metadata file you downloaded from the Citrix Cloud, in a text editor..
- Select all and copy and past into the Service Provider Metadata box on DualShield.
- Click Save
- Enable Sign on SAML Assertion under SAML Options
- Click on Attributes tab at the top
We are now going to add the following attribute names which are required by the Service Provider.
cip_email
cip_upn
cip_oid
cip_sid
With the exception of cip_sid the above attributes will be mapped to their counterpart DualShield Identity Attributes which in turn are mapped to the Active Directory account attributes.
For example:
Citrix SAML Attribute | DualShield Identity Attribute | AD Account Attribute |
cip_email | ||
cip_upn | userPrincipalName | userPricipalName |
cip_oid | uuid | ObjectGUID |
In steps 1-5 you created a new Identity Attribute called objectSID. This will be specified in a script which will be applied to the cip_sid Citrix Attribute
- Click Create
- On the Attributes builder specify Location as HTTP Body and enter cip_upn as the name for this attribute.
- Click on the search symbol to the right of the Maps To field.
- Select the identity source that will be used and select User Principal Name from the Maps to drop down list:
- Click Save
- Click Save again
- Repeat steps 21 - 23 but this time name the attribute cip_oid
- Repeat steps 24 & 25 but this time map to Unique Identifier
- Click Save
- Click Save again
- Repeat the process above, one more time. Name the attribute cip_email and map to email.
- For cip_sid, create a new attribute and name it cip_sid
- Under the Value group box, select Script
- Copy and paste the following script into the text box.
| Wiki Markup |
|---|
if (!objectSid) return null;
\\
byte\[\] sid = objectSid.decodeHex();
\\
if (sid.length<8 || sid.length % 4 != 0) return "";
\\
StringBuilder sb = new StringBuilder();
sb.append("S-").append(sid\[0\]);
int c = sid\[1\]; // Init with Subauthority Count.
\\
// Default order is BIG_ENDIAN
java.nio.ByteBuffer bb = java.nio.ByteBuffer.wrap(sid);
sb.append("-").append((long)bb.getLong() & 0XFFFFFFFFFFFFL);
bb.order(java.nio.ByteOrder.LITTLE_ENDIAN); // Now switch.
\\
for (int i=0; i<c; i++) \{ // Create Subauthorities.
sb.append("-").append((long)bb.getInt() & 0xFFFFFFFFL);
\}
return sb.toString(); |
- Click Save. The Service Provider Attributes window should now look like this..
- Click on General Settings at the top
- Set the default attribute to cip_upn (You can click anywhere in this field to change it.)
- Click Save at the bottom.