Physical hardware TOTP tokens (such as the SafeID Classic token) are fully self-contained authentication devices with built in batteries that power both the LCD display, and the token's internal clock.
When the tokens are used they produce a 6 digit OTP code based upon the seed data that the token was programmed with, and the current time (as reported by the token's internal clock).
Token seed files are sent separate to the tokens themselves, and can be requested online (see How to request token seed or secret file for details on how to request this file).
Once you have both the physical token and the seed file you can test that the OTP codes generated by the device are correct using the following procedure;
Testing the generated OTP codes
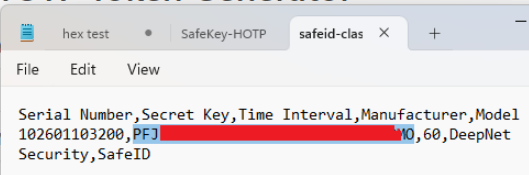
In order to test the token we first need to extract the secret data for the token by searching the seed file for the record with a matching serial number;
The seed may have been requested in a number of formats, but for the purposes of this test we need the seed base32 encoded (digits "2" to "7 "and any letters of the alphabet).
If you received the seed data in Hex format (letters "A" to "F" and any digit) then you can convert the seed to base32 using the following online tool:
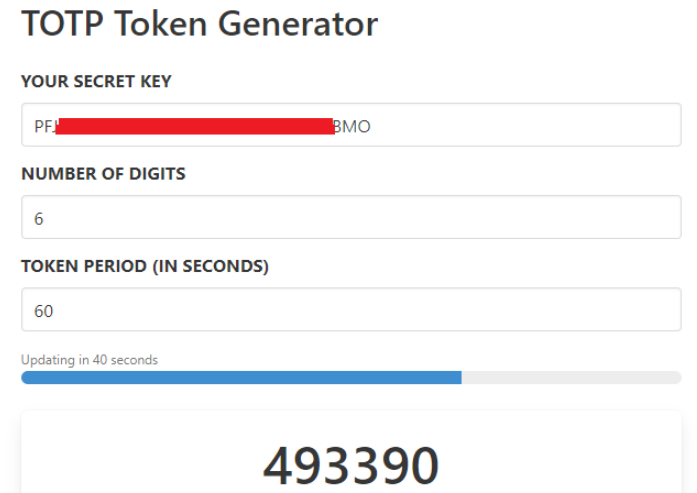
Once you have the base32 encoded secret navigate to the following online TOTP and replace the displayed secret key with the base32 encoded secret key for the token you are testing;
It is probable that your token uses 60 second windows (Time Interval in the above example), ensure that the Token Period in the online generator is updated to match the time period for your token.
The online generator will now be displaying 6 digit OTP codes that update with the same frequency your hardware token does. Turn on the token and check that the two codes match.
Determining the extent of any time drift
If the previous test produced codes that do not match then a few possible causes
- The token is not time based (TOTP) but event based (HOTP)
- The seed supplied is from a different token from your seed file (double check the serial number on the back of the token matches the extracted seed)
- The supplied token period is wrong (try the test again using both 30 and 60 second time periods)
- The token is functional, but there is some time drift
If time drift is involved we perform a different test to check the extent of time drift.
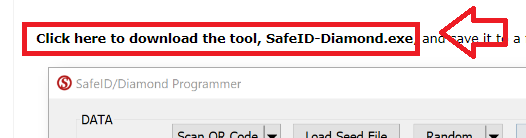
First download and run the SafeID Diamond Programming Tool;
This tool was primarily designed to program SafeID/Diamond tokens, but can also be used to test pre-programmed tokens for time drift.
The app will need to be run on a windows system and should only be run on a system that has had its clock accurately set (we suggest you synchronise you clock with internet time but if you can manually correct the clock within a few seconds this will be fine).
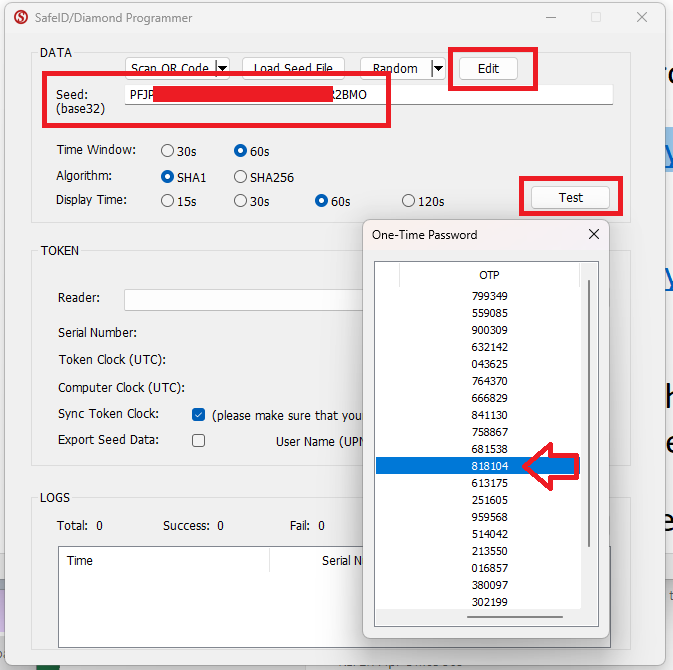
Click on the button, and at the prompt "Seed: (base32)" copy and paste the base32 encoded seed data for your token, and set the "Time Window" and "Display Time" to match the window size of your token (normally 60 secpmds);
After entering the seed data click on the button and a new window titled "One-Time Password" should open;
Using the horizontal scroll bar if necessary, view the list of OTP codes that are generated and compare them with the code shown on your hardware token, you will be able to determine the extent of time drift on the token.
If there is a small amount of time drift you should find that the code displayed on the token is also listed in the list of OTP codes shown on this window.