Active Directory Infrastructure - Real Domain.
Most people in the IT world will be familiar with the term domain on an IT network. The most common type of domain would be created in Microsoft Active Directory and is defined as a logical group of network objects (computers, users, devices) that share the same Active Directory database. The DualSheid Authentication server can connect to this domain via an identity source using the LightWeight Directory Access Protocol or LDAP for short.
Please refer to this wiki guide on connecting to AD for further information: Connect to an Active Directory
Once connected it is possible to assign authentication tokens, such MobileID, T-Pass tokens to a user accounts in the domain.
Please refer to: Token Management
you can even create Group held policies, eg Users in one security group have to log on using 2fa, whereas the users in another group can bypass 2fa.
See: Logon policy implementation strategy
For Windows Logon to work on an AD bound workstation, the first stage of authentication is usually the user account name (or logon name) plus the password. Dualshield can check these credentials against the Active Directory Database. Once these have been verified DualShield will then check the second factor, whether it be a one-time password, On-demand password or Push notification against it's own internal database to make are these are correct or Push is authorised, before successfully logging the end-user on to their work station.
Stand alone Infrastructure - Virtual Domain
There are some IT networks that do not require AD domain joined machines. It could be a small company with a hand full of PCs that only access a NAS, or with the worldwide changing landscape of how people work today, more and more people are working from home, so there will be no need to join the laptop to an AD domain, because once the user gets the machine home, there is no domain, on the home network to authentication.
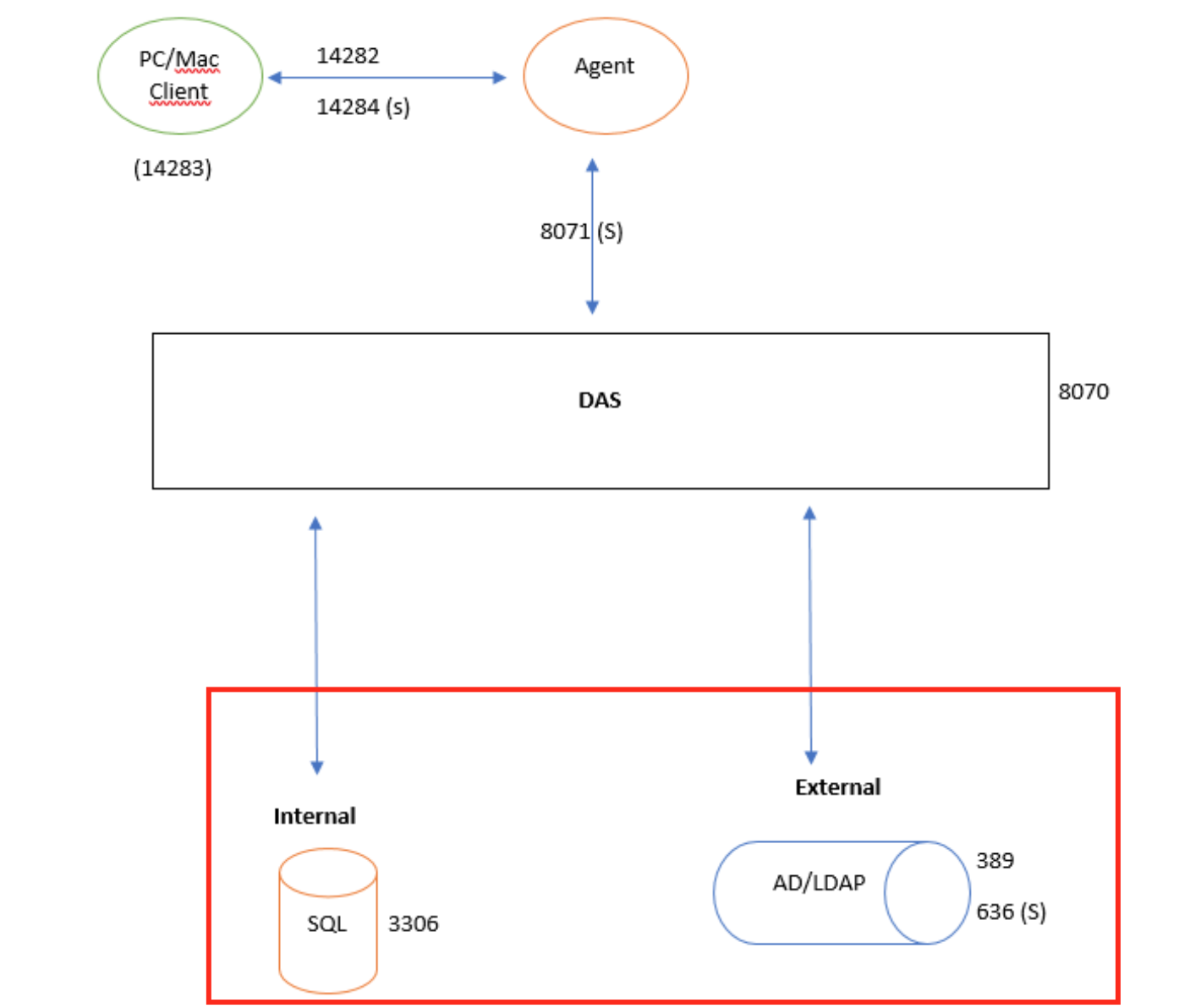
However, DualShield still requires a domain structure collection of accounts that tokens can be assigned to, and Groups for policies to be applied. This is possible by creating a virtual domain. The difference between the real domain and a virtual domain is, the real domain uses an external LDAP database as the Identity source, whereas the Virtual domain uses an internal SQL database as its identity source.
The diagram below shows how Logon Client communicates to the DualShield Authentications Server (DAS) via Logon agent, and how the Authentication server connects to either the internal SQL Identity Source or External LDAP Identity source and uses them as an authentication domain.