When a DeviceID token is being deleted or disabled in the authentication server, by the administrator using the admin console, the authentication server will inform the DualShield IIS Agent running on the Exchange servers immediately so that the token will be also removed from the session cache in the IIS Agent. Otherwise, access from the device will still be allowed until the session has expired.
Test Connection from DualShield to Exchange
For this alert to work, the DualShield server must be able to access the IIS service of the Exchange server
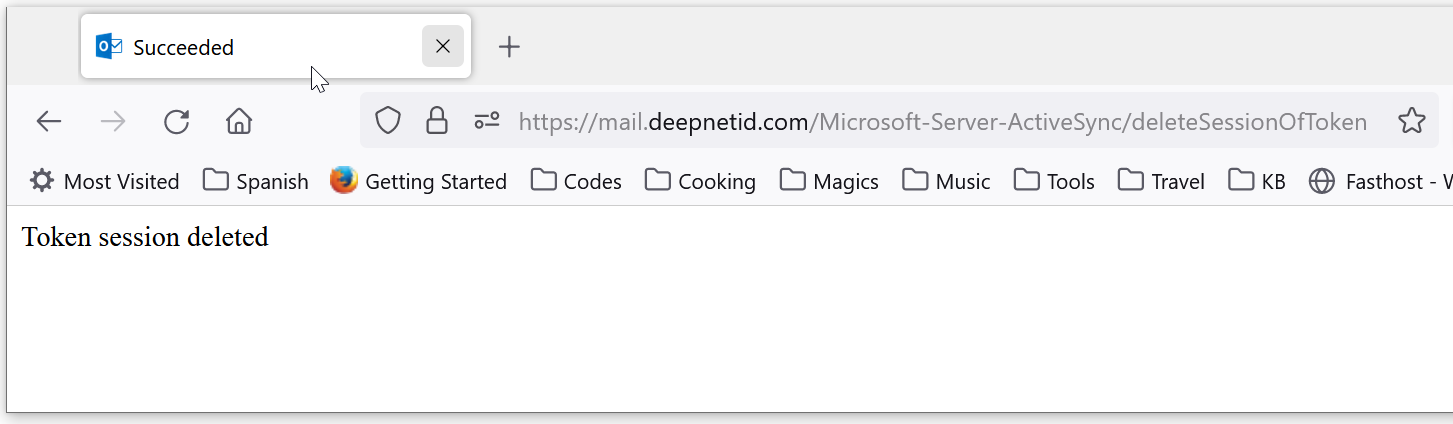
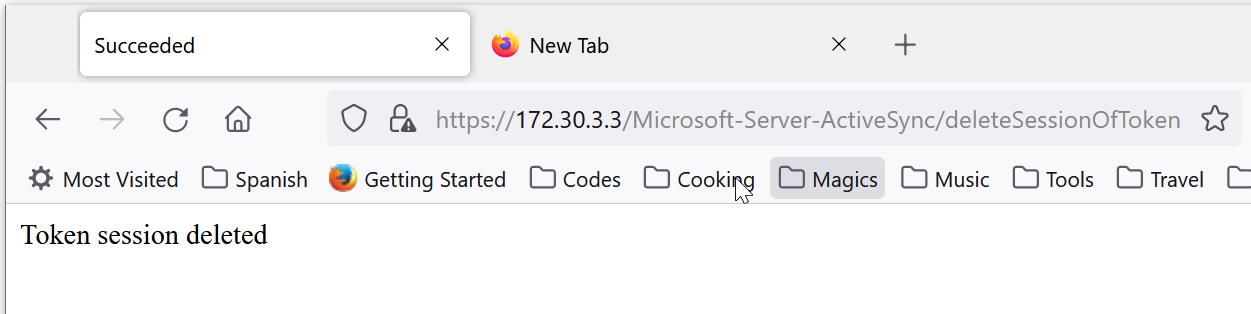
To test the connection, on the DualShield server, visit the following URL:
https://exchange-server-internal-address/Microsoft-Server-ActiveSync/deleteSessionOfToken
The "exchange-server-internal-address" can be either the internal hostname or IP address of the Exchange server, e.g. mail.deepnetid.com or 172.30.3.3
Configure the IIS Trigger Task
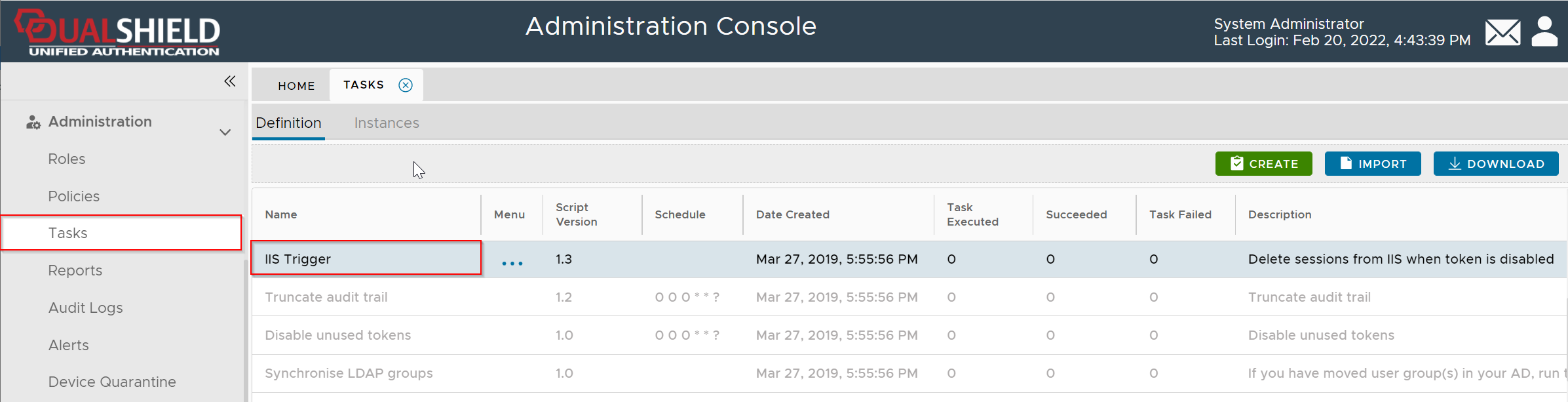
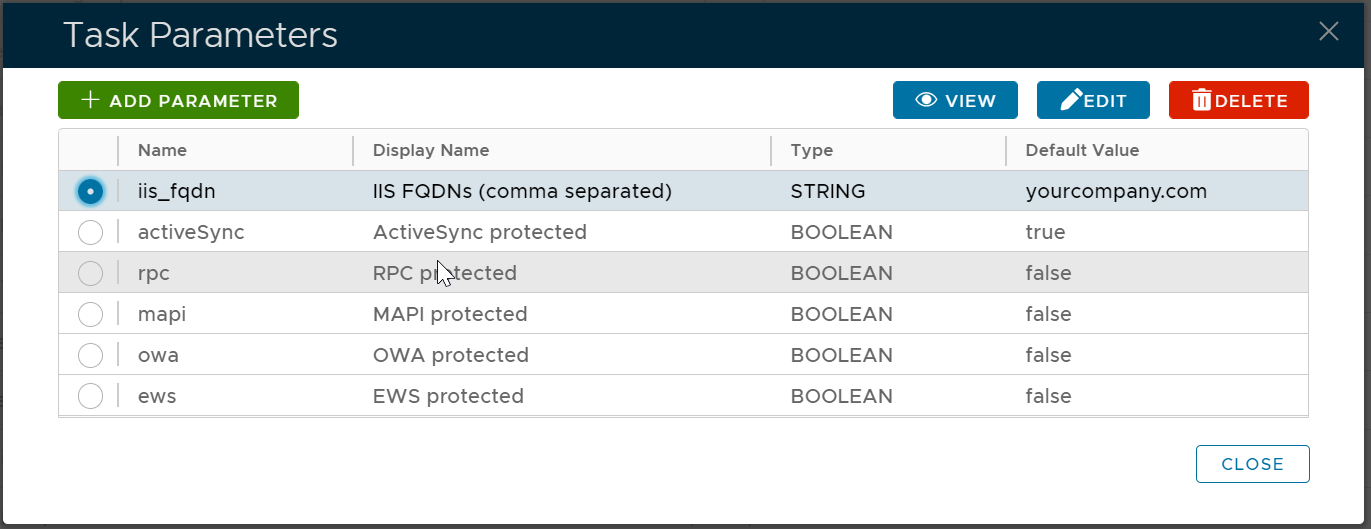
Navigate to Administration | Tasks
Find the IIS Trigger task
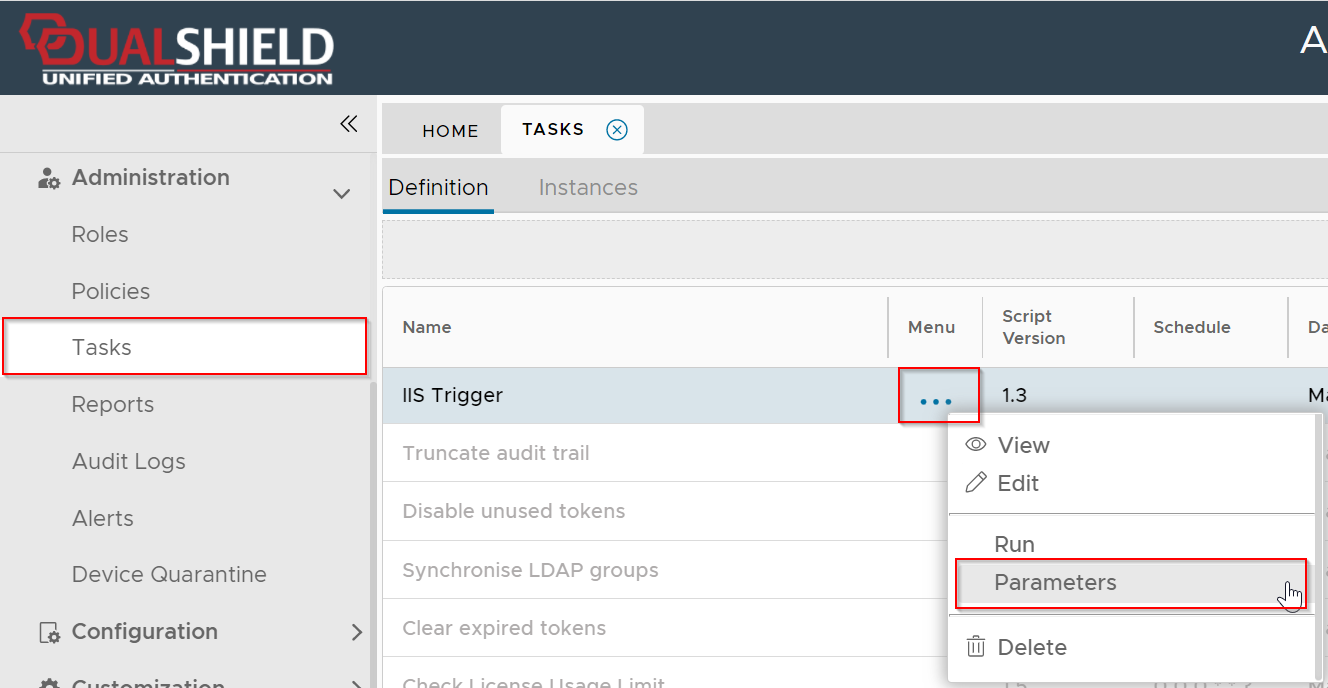
Click the context menu of IIS Trigger task
Select Parameters
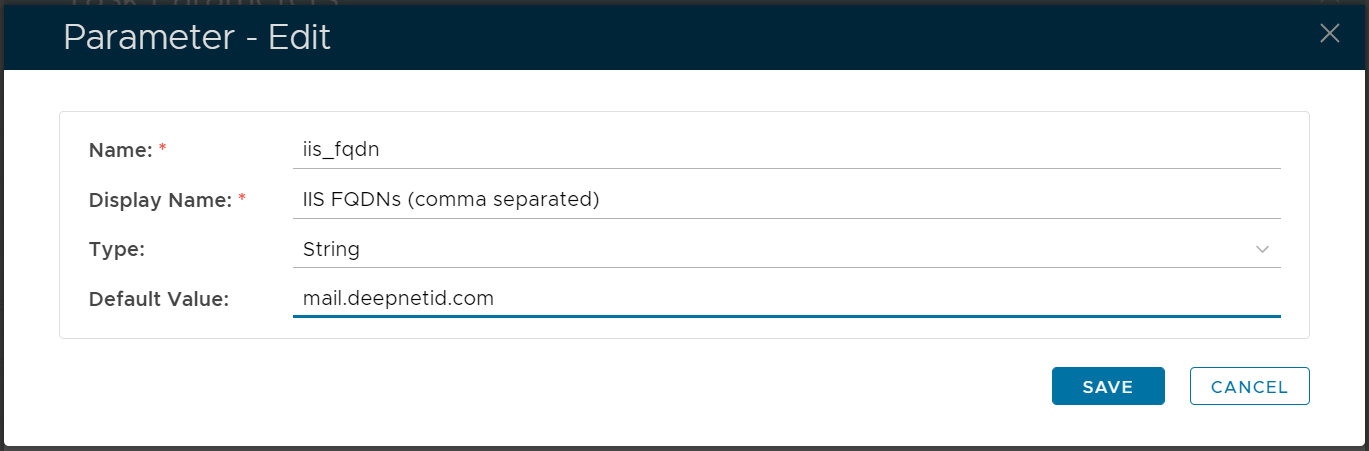
Select iis_fqdn, then click the "EDIT" button
Change the default value to the internal address (FQDN or IP address) of your Exchange server, e.g. mail.deepnetid.com
(If you have multiple Exchange servers, you should enter all addresses in a comma separated list)
Click SAVE to save the change
Change the default value of the following options as below
| Option | Default Value |
|---|---|
| activeSync | true |
| rpc | false |
| mapi | false |
| owa | false |
| ews | false |
Create a Device Deletion Alert
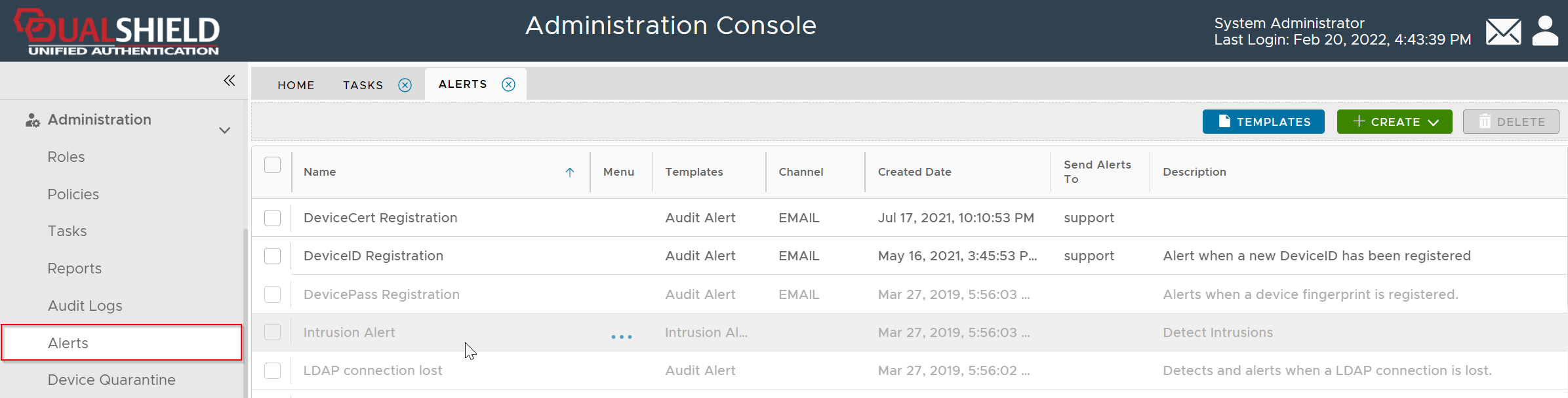
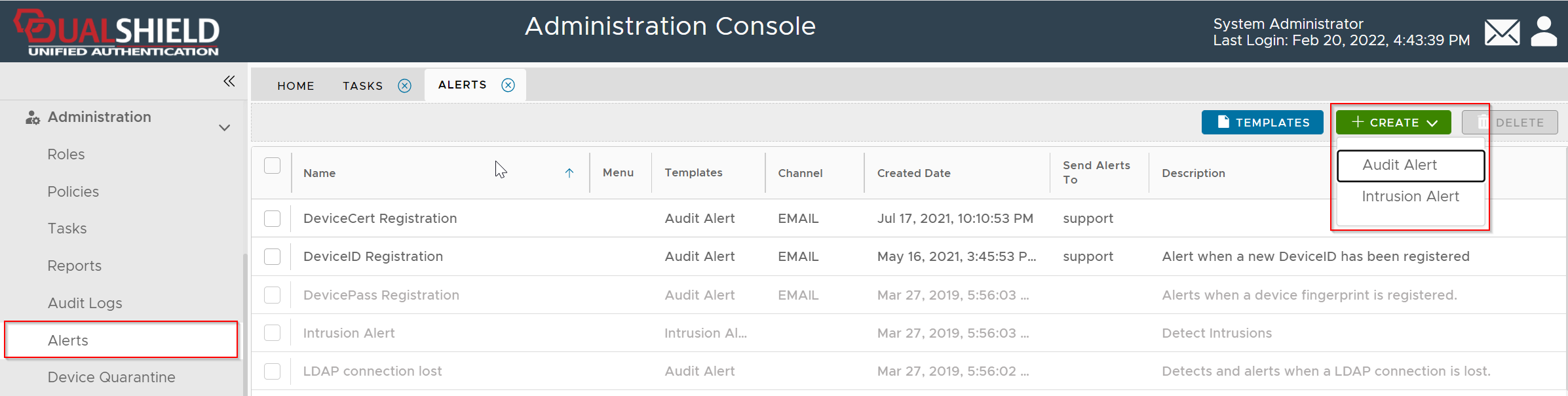
Navigate to Administration | Alerts
Click the CREATE button
Select Audit Alert
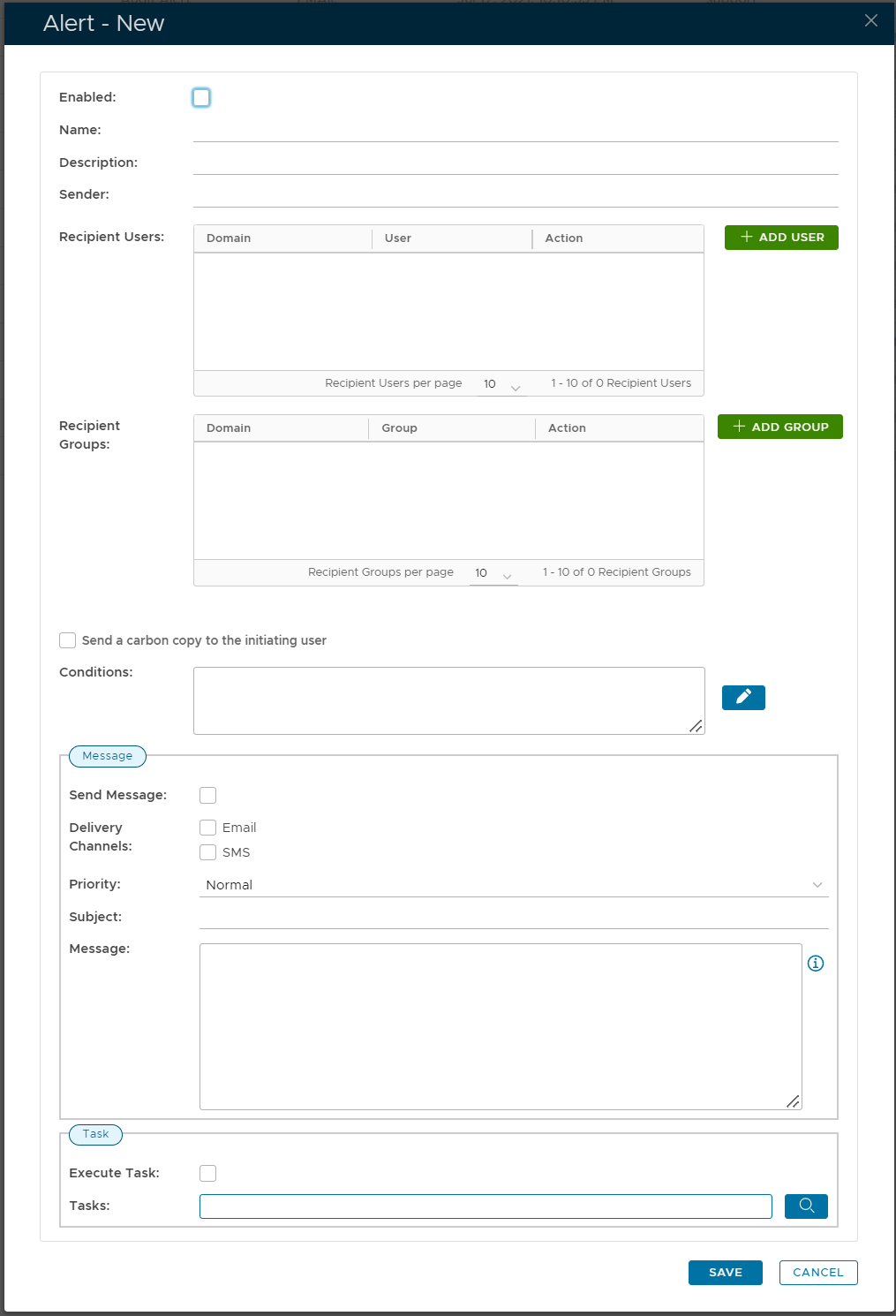
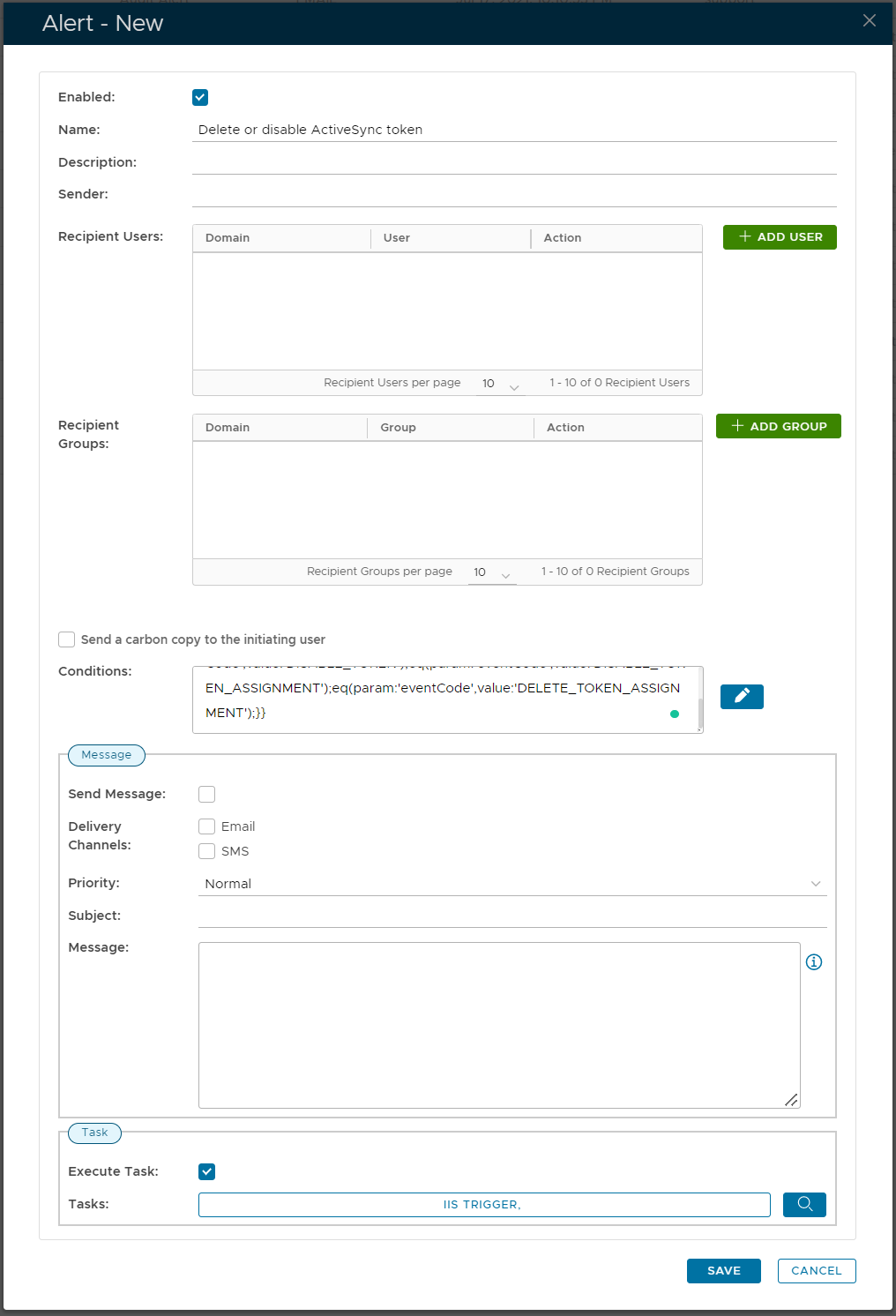
Turn on the Enabled option
In the Conditions box, enter the code below
and{
eq(param:'tokenCode',value:'DN-ASDID');
or{
eq(param:'eventCode',value:'DELETE_TOKEN');
eq(param:'eventCode',value:'DISABLE_TOKEN');
eq(param:'eventCode',value:'DISABLE_TOKEN_ASSIGNMENT');
eq(param:'eventCode',value:'DELETE_TOKEN_ASSIGNMENT');
}
}
Turn on the Execute Task option
In the Tasks box, select the IIS TRIGGER task
Click SAVE to save thealert