In some rare environments, the DualShield MFA cannot be connected to the native AD server. The MFA service provider has to use an non-native AD or even SQL server as the user directory server. Furthermore, the service provider might have to provide different usernames to the AD users. To make the computer MFA logon work in this type of environment, you will need to reformat the username. Follow the steps below:
- Create a special registry key
On the Windows client PC, create the registry key below:
HKEY_LOCAL_MACHINE\SOFTWARE\Deepnet Security\Computer Logon
Then, add a string value named “logon_format”. The value can be anything you like, but you need to have a fixed pattern.
For instance, the value starts with “winlogon-“ followed by the Netbios name and the username, i.e. “winlogon-%netbios%-%username%
There are 3 wildcards below you can use:
- %netbios%
- %dns%
- %username%
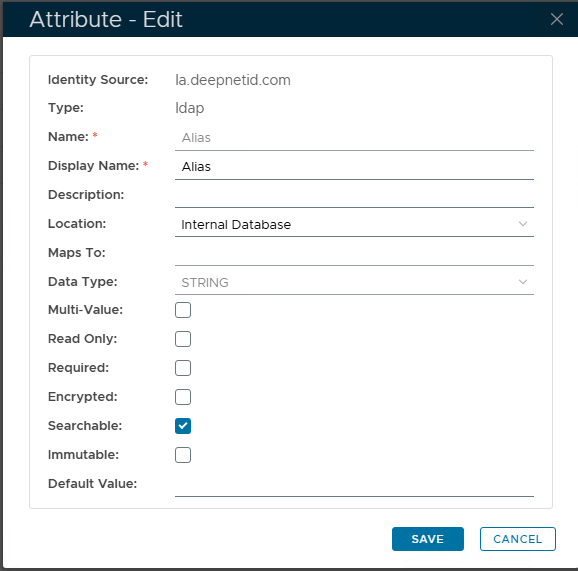
- Create an Identity Attribute for Alias
In the DualShield MFA server, create a new Identity Attribute and name it whatever you like, such as “Alias”. You can make it an internal Identity Attribute or an External Attribute; however, if you choose to make it external, it will need to be mapped to an AD account attribute.
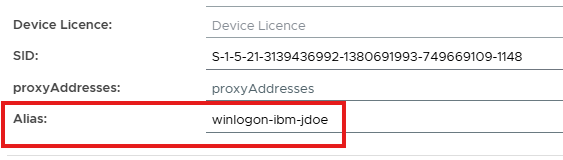
- Set Alias for each user
For each user, you need to set the value of the Alias Identity Attribute. The value must follow the same format/pattern as the “logon_format”. For example: “winlogon-ibm-jdoe” for the user “jdoe” in the “ibm” organization.
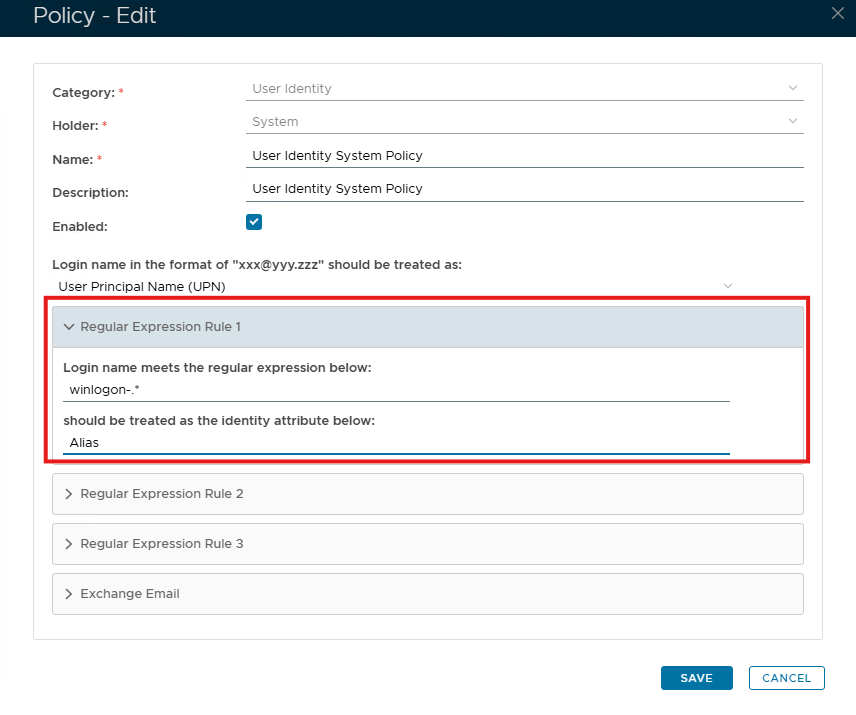
- Setup the User Identity policy
Edit the User Identity policy, set the Regular Expression Rule 1 according to the “logon_format”, e.g. “winlogon-.*