You may find that your DualShield IIS agent stops working after applying an Exchange server CU update or upgrade. This is because the Exchange CU update or upgrade has reset all web application settings, i.e. the "web.config" file, hence causing the settings for the DualShield IIS agent to be lost.
You will have to restore the settings of the DualShield IIS Agent first, then re-apply the settings.
Step 1: Restore Settings
You can restore the DualShield IIS Agent settings in 2 ways, restore by GUI or by PowerShell script.
Restore by GUI
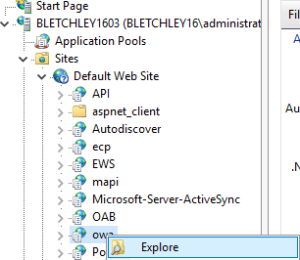
This has to be done on every IIS node that is enabled with DualShield 2FA. Let's use OWA as an example. In the IIS Manager, navigate to the OWA node:
Right click it, then choose "Explore"
It will take you to the physical folder, C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa.
Now, open web.config in a text editor, find the <modules> tag and insert <add name="DasIIS7Native"/> into the tag, e.g:
<modules> <add name="DasIIS7Native"/> </modules>
Below is a complete sample:
<?xml version="1.0" encoding="UTF-8"?> <configuration <!-- .... --> <configSections> <section name="microsoft.identityModel" type="Microsoft.IdentityModel.Configuration.MicrosoftIdentityModelSection, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35"/> </configSections> <location inheritInChildApplications="false"> <system.webServer> <serverRuntime appConcurrentRequestLimit="65535" uploadReadAheadSize="0"/> <modules> <add name="DasIIS7Native"/> <!-- .... --> </modules> </system.webServer> </location> <!-- .... --> </configuration>
Repeat the above work on every node that's been affected.
Restore by PowerShell Script
Step 2: Re-Apply Settings
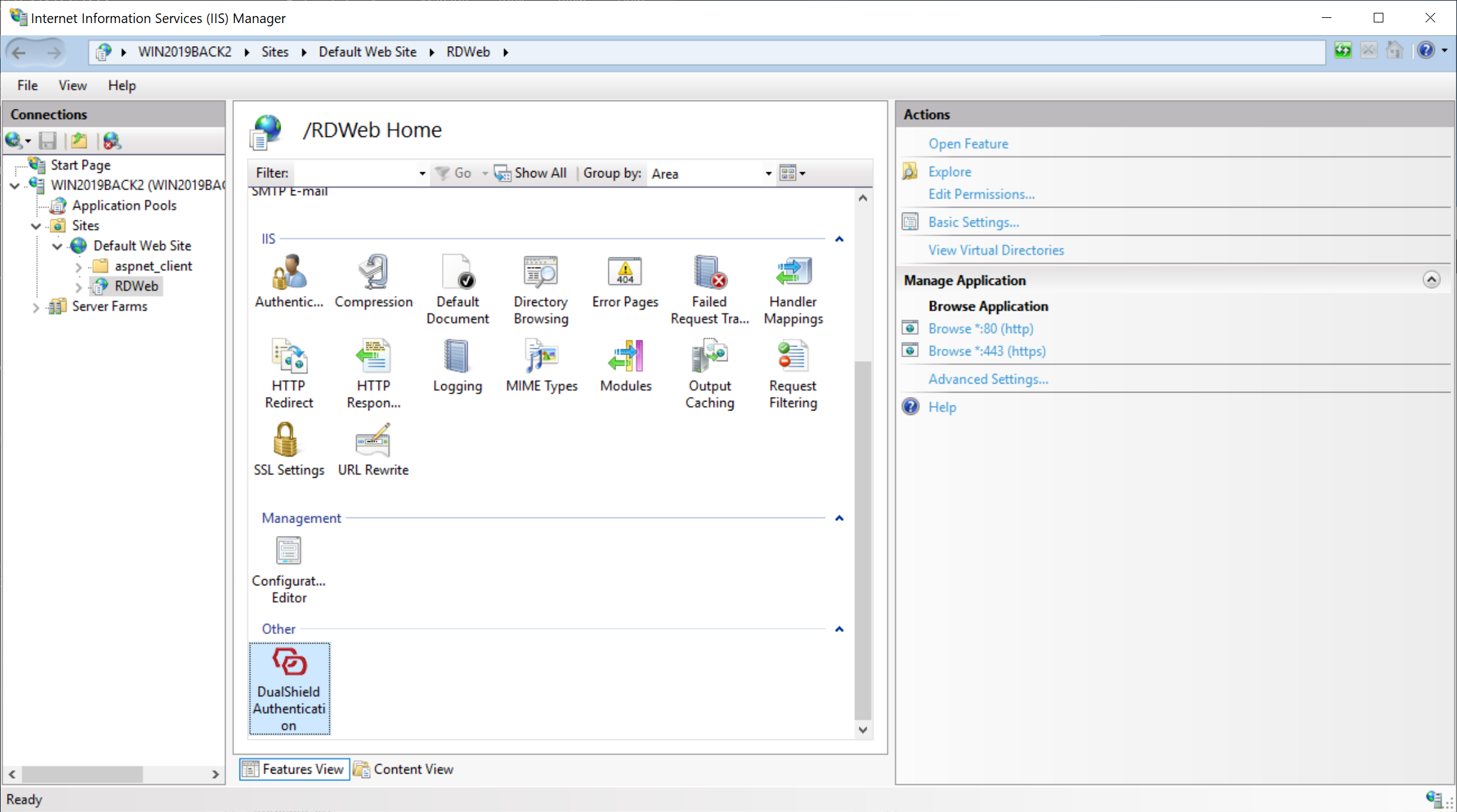
In the IIS Manager, select to a node that's enabled with DualShield 2FA, e.g. RDWeb.
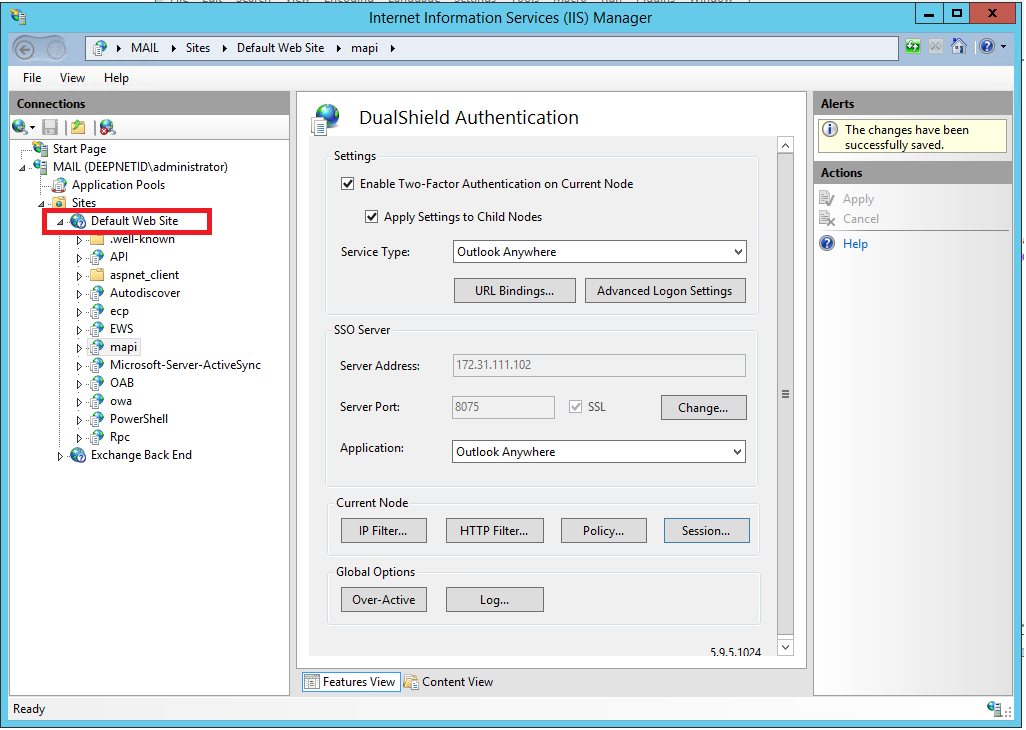
On the right pane, double click the DualShield icon to open its settings
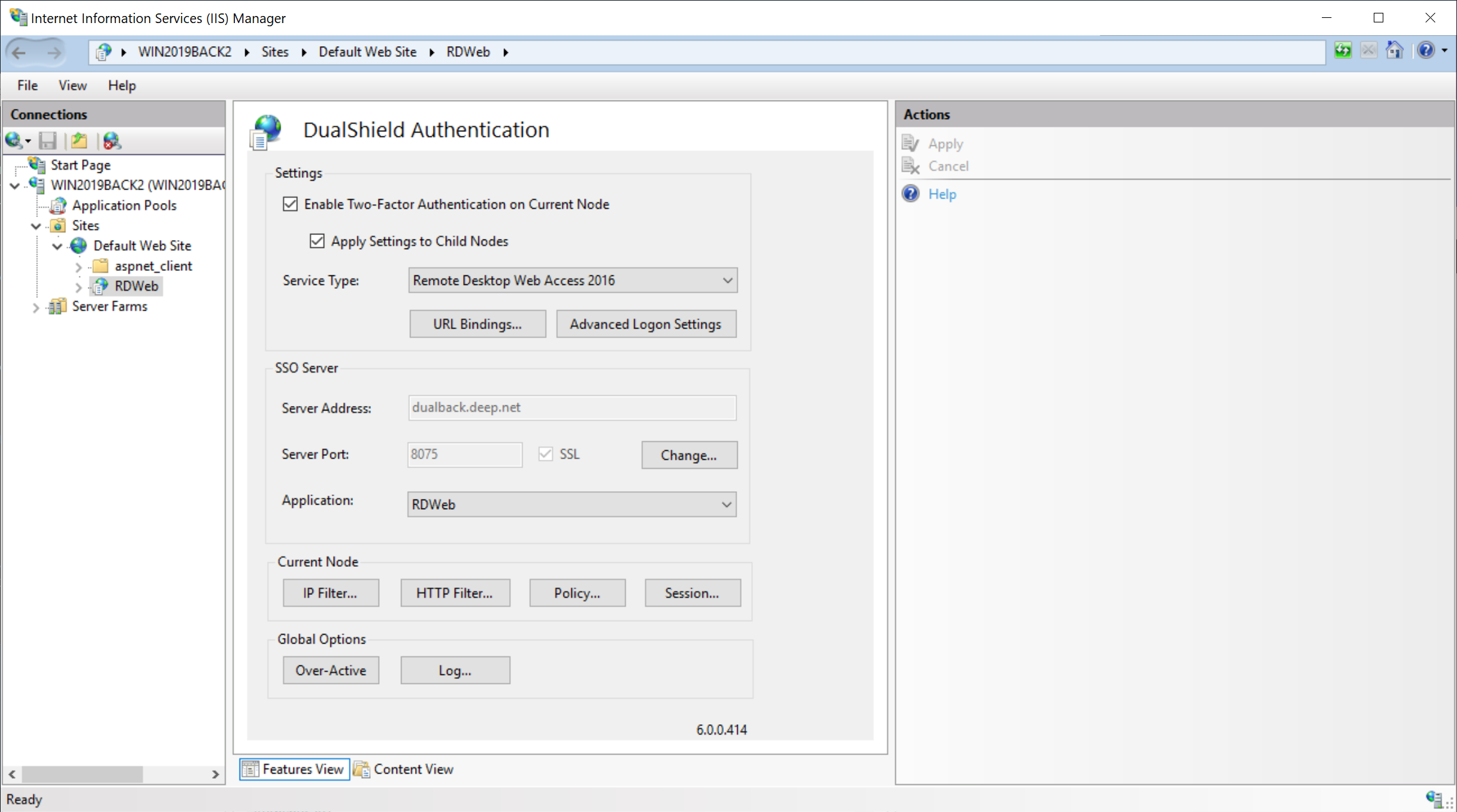
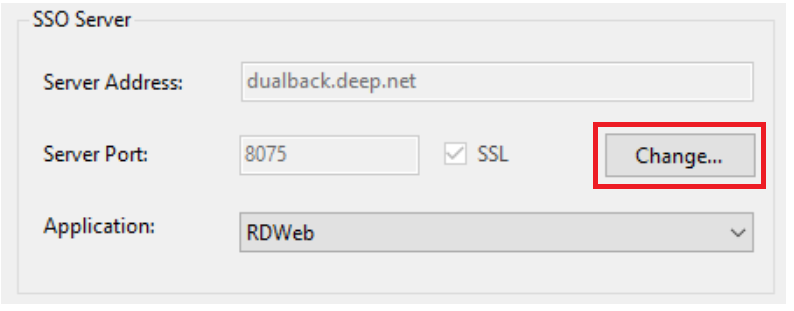
Click the "Change” button in the “SSO Server” section:
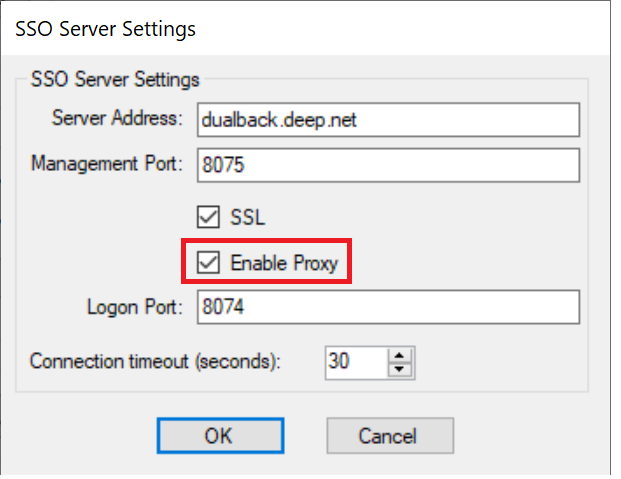
In the SSO Server Settings windows, untick the “Enable Proxy” option:
Click “OK”
Then, click “Apply” to save the changes
Now, go back to the “SSO Server Settings” and tick the “Enable Proxy” option:
Click “OK”
Then, click “Apply” to save the changes.