This article explains how to capture RADIUS traffic using Wireshark.
If using PAP authentication protocol, then this article will explain how to decrypt the traffic to be able to see the username and passcode in plain text.
Start by installing Wireshark on the same server as DualShield.
Capture RADIUS packets
- Launch the Wireshark app
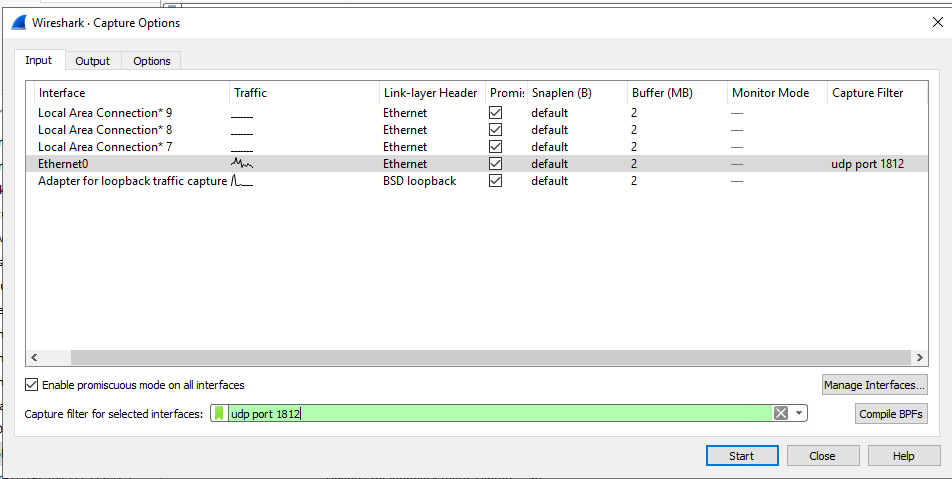
- Select "Capture | Options"
- Enter "udp port 1812" in the Capture filter to capture UDP packet only
- Click the "Start" button to start capture
- Click "Capture | Stop" to end capture
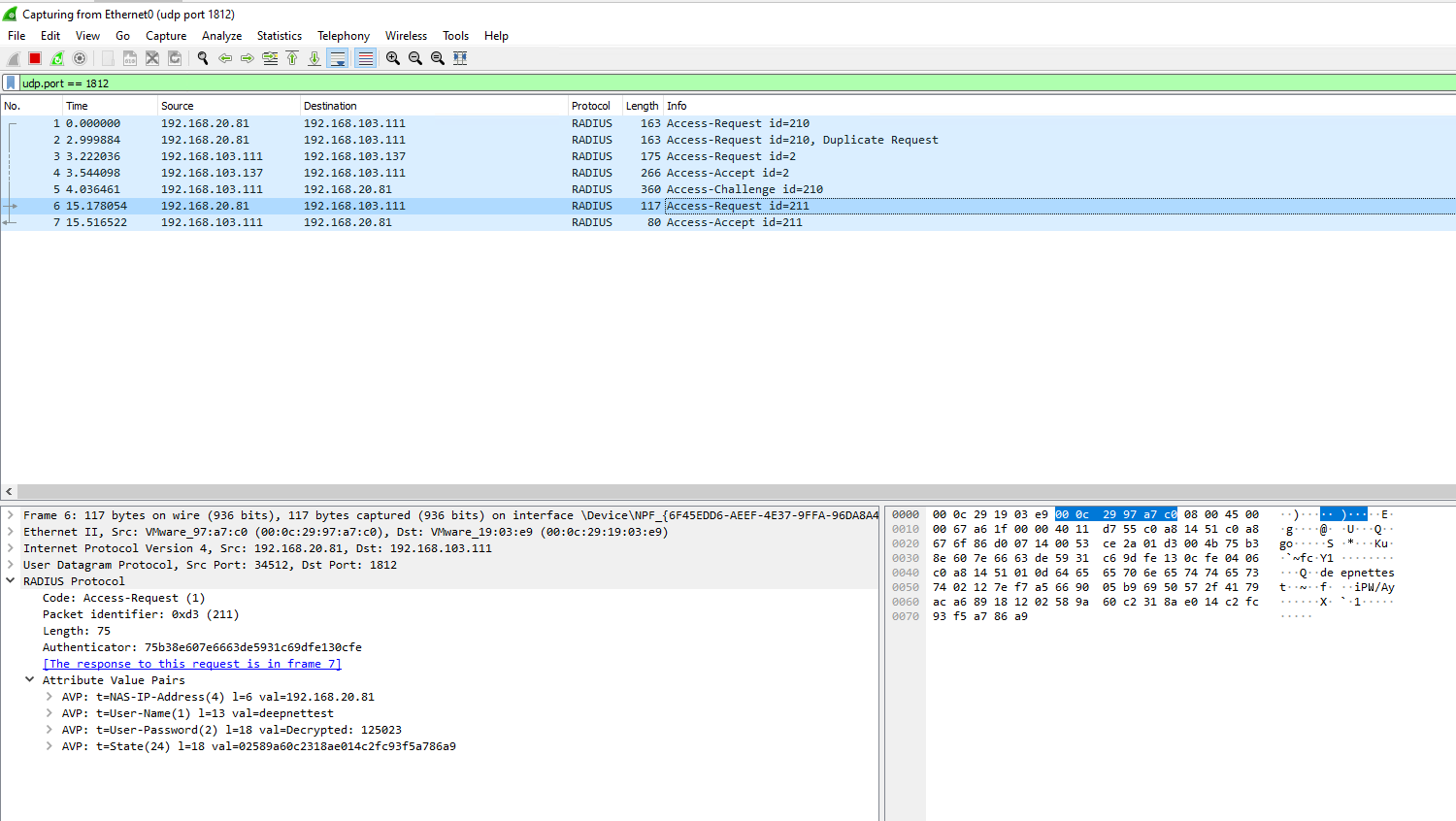
- You will now be able to view the Access-Request and Challenge packets
Decrypt RADIUS packets (PAP authentication only)
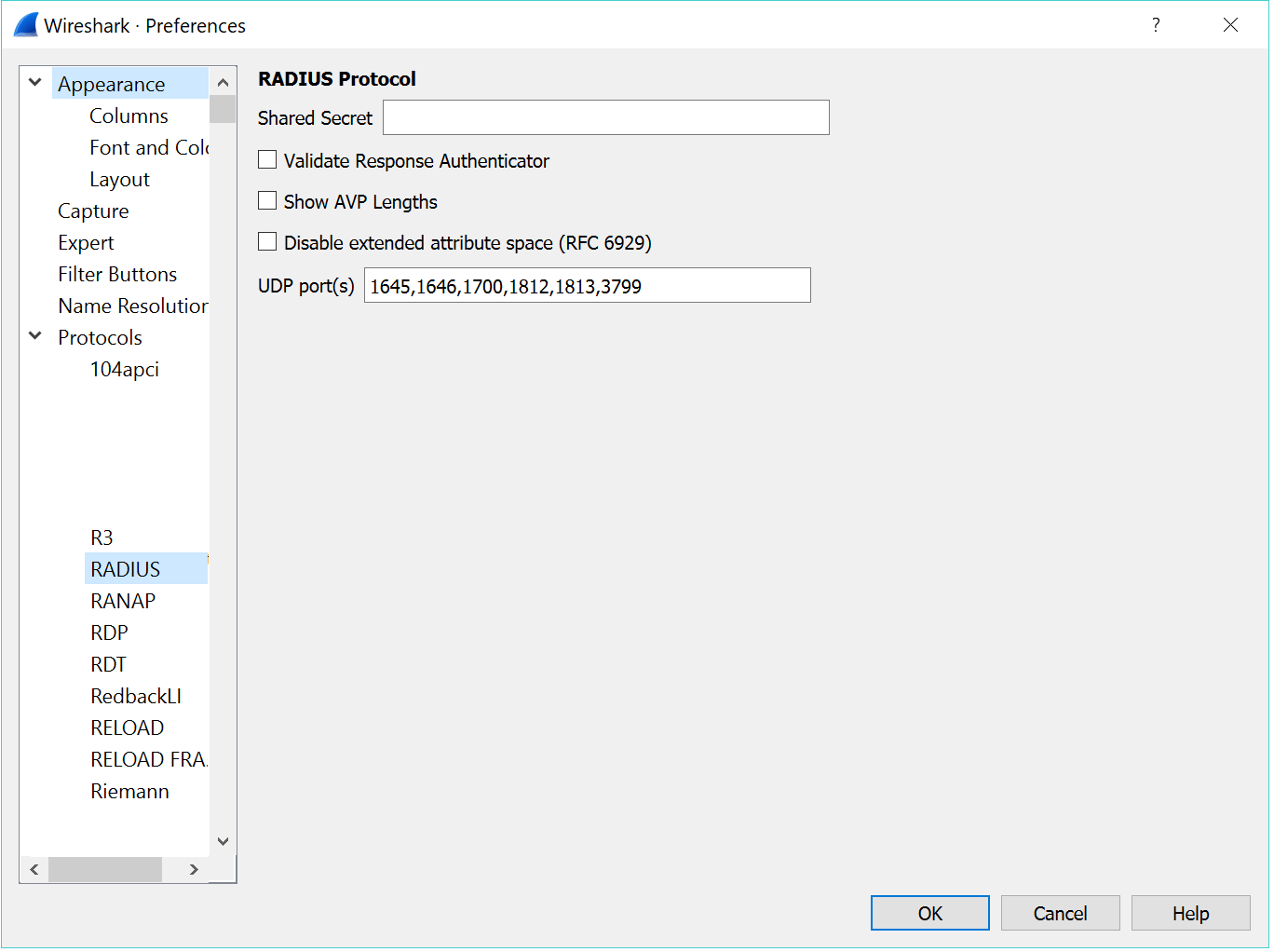
- Go to Edit > Preferences
- Click to expand the Protocols tree
- Scroll down and select RADIUS
- Enter the RADIUS shared secret and click OK to save