Security Assertion Markup Language (SAML) is an open standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP).
SAML transactions use Extensible Markup Language (XML) for standardized communications between the identity provider and service providers. SAML is the link between the authentication of a user’s identity and the authorization to use a service.
SAML enables Single-Sign On (SSO), a term that means users can log in once, and those same credentials can be reused to log into other service providers.
What is a SAML Provider?
A SAML provider is a system that helps a user access a service they need. There are two primary types of SAML providers, service provider, and identity provider.
A service provider needs the authentication from the identity provider to grant authorization to the user.
An identity provider performs the authentication that the end user is who they say they are and sends that data to the service provider along with the user’s access rights for the service.
DualShield SSO is an identity providers, and Salesforce and other CRM solutions are usually service providers, in that they depend on an identity provider for user authentication.
How Does SAML Work?
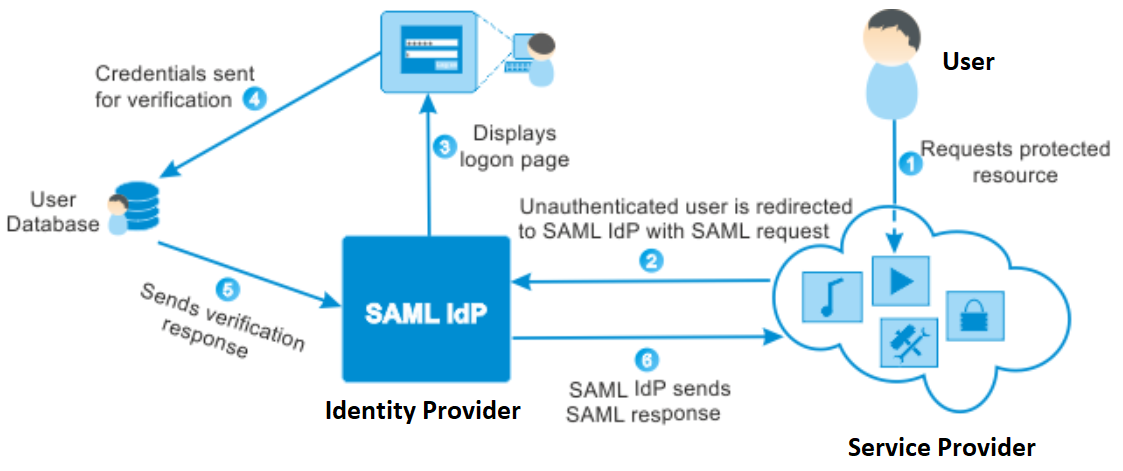
SAML works by passing information about users, logins, and attributes between the identity provider and service providers. Each user logs in once to Single Sign On with the identify provider, and then the identify provider can pass SAML attributes to the service provider when the user attempts to access those services. The service provider requests the authorization and authentication from the identify provider. Since both of those systems speak the same language – SAML – the user only needs to log in once.
In a SAML verification process, three parties are involved, User, Service Provider and Identity Provider. The diagrams below illustrate the relationship between them and the data flow.
What is a SAML Metadata
A SAML Metadata is a XML document that includes the information about a SAML provider, such as its Entity ID, Logon URL, Logout URL, Assertion URL, and Certificate of the provider etc.
In order for a SAML IdP and SP wo trust each other and to work together, each identity provider and service provider need to agree upon the configuration for SAML. Both ends need to have the exact configuration for the SAML authentication to work. This is typically achieved by exchanging the matadata between the IdP and the SP.
What is a SAML Assertion?
A SAML Assertion is the XML document that the identity provider sends to the service provider that contains the user authorization. There are three different types of SAML Assertions – authentication, attribute, and authorization decision.
- Authentication assertions prove identification of the user and provide the time the user logged in and what method of authentication they used (I.e., Kerberos, 2 factor, etc.)
- The attribution assertion passes the SAML attributes to the service provider – SAML attributes are specific pieces of data that provide information about the user.
- An authorization decision assertion says if the user is authorized to use the service or if the identify provider denied their request due to a password failure or lack of rights to the service.