For computer MFA logon, the type of logon procedure is called Windows. It is named as such due to historical reasons.
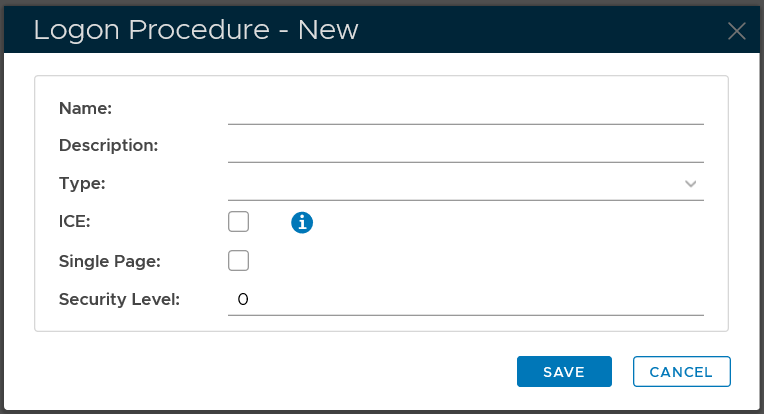
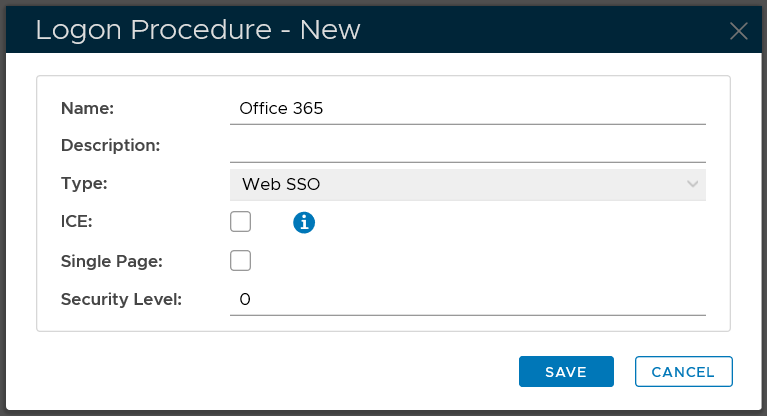
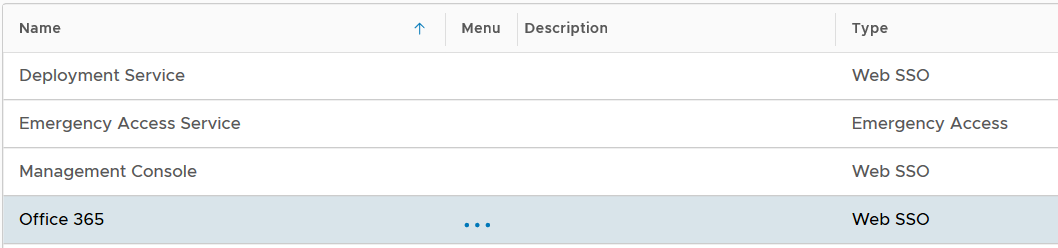
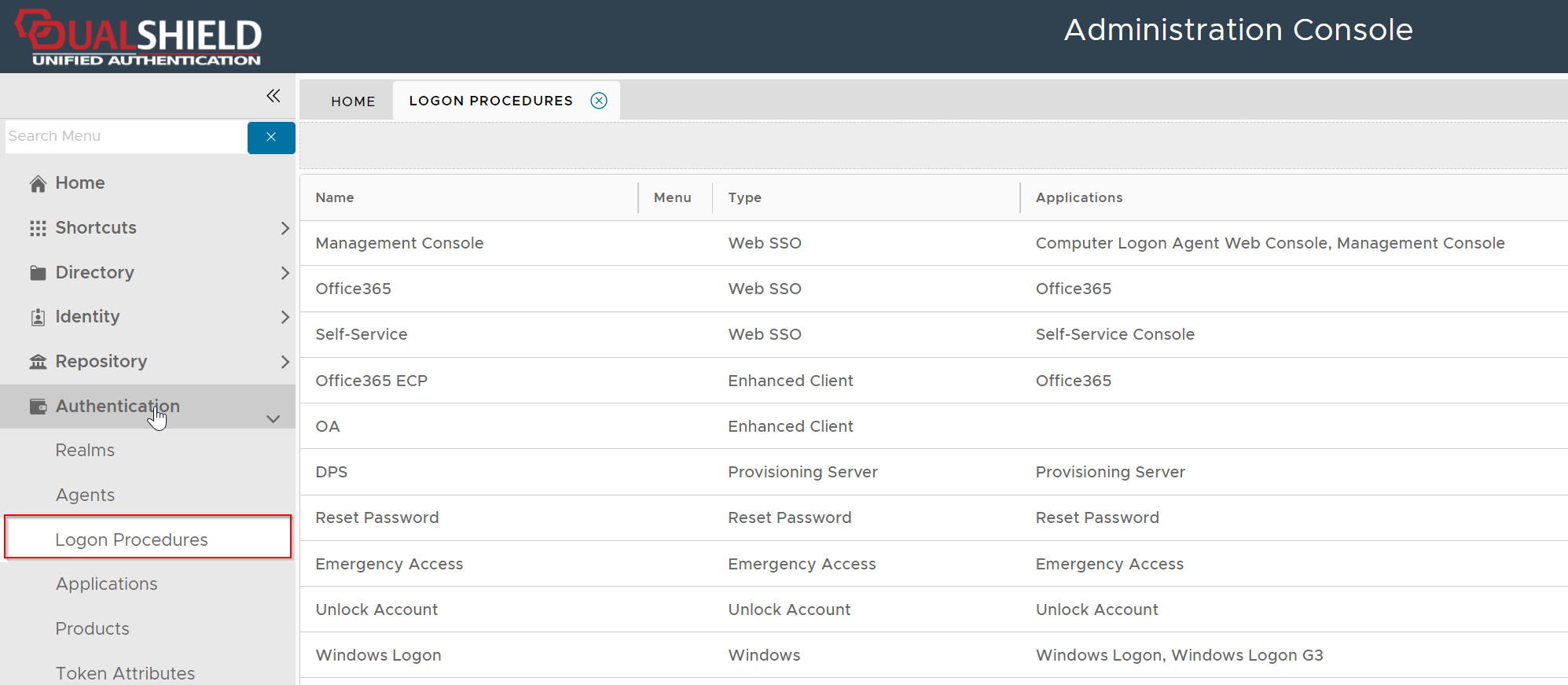
Below is the general guide for creating a logon procedure in DualShield
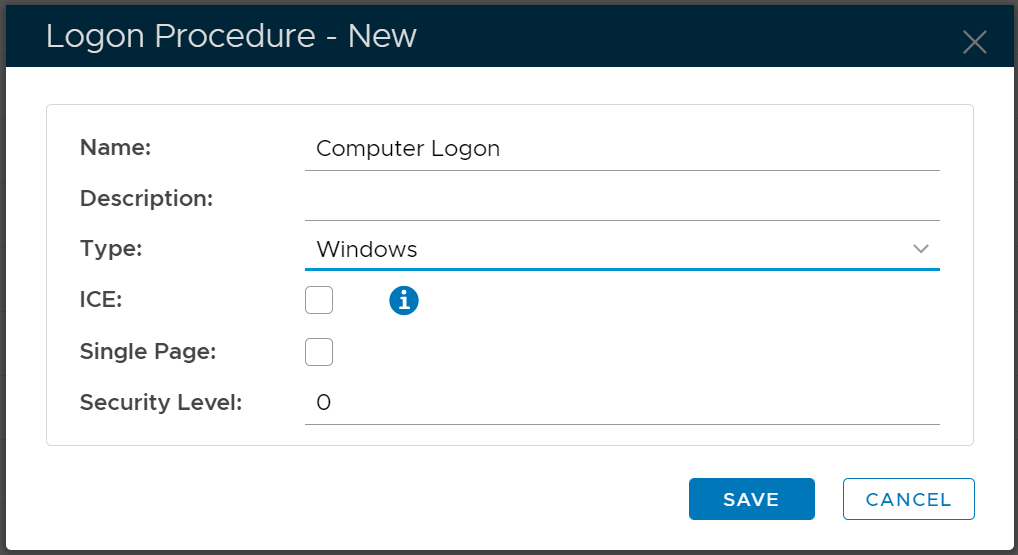
Make sure that the type of the Logon Procedure you have created is Windows
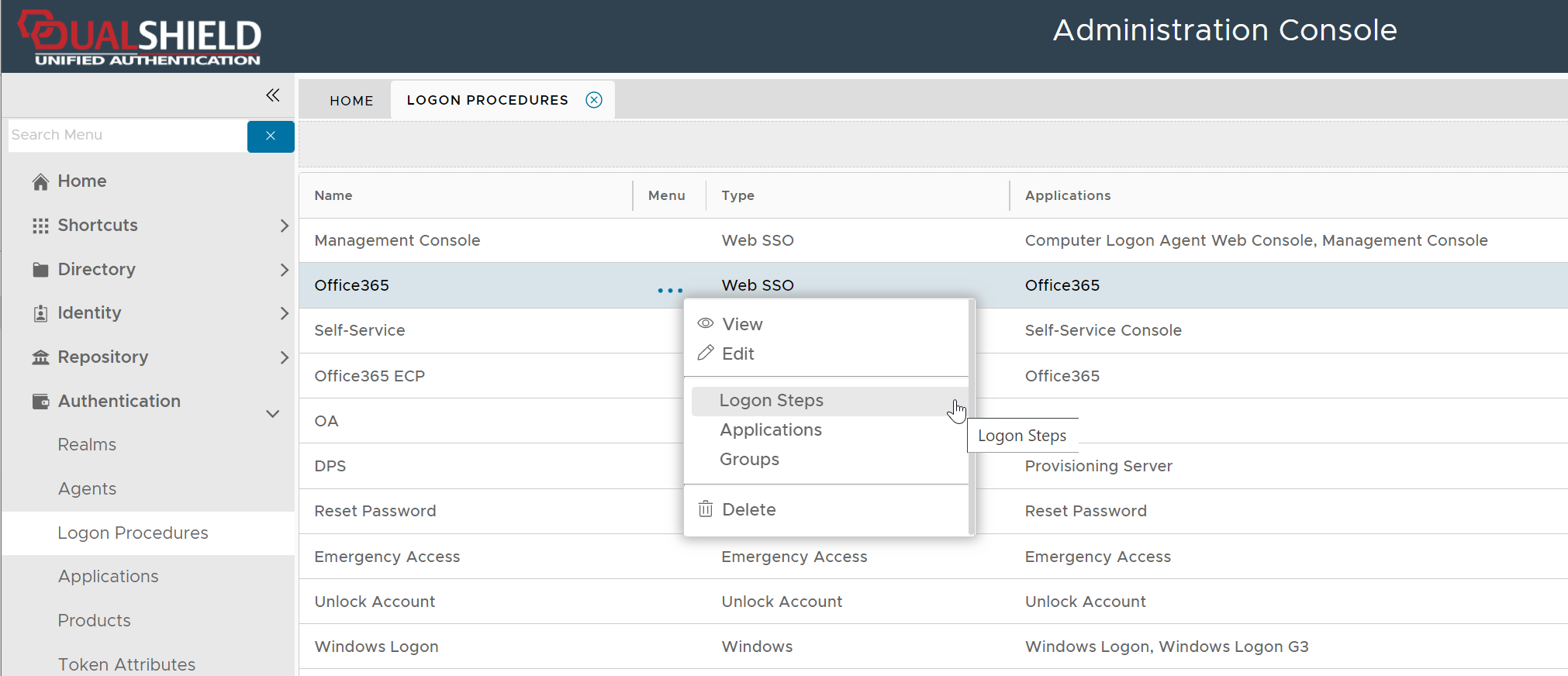
Once a logon procedure has been created, you need to add logon steps into the newly created logon procedure.
Logon Step for Computer MFA Logon
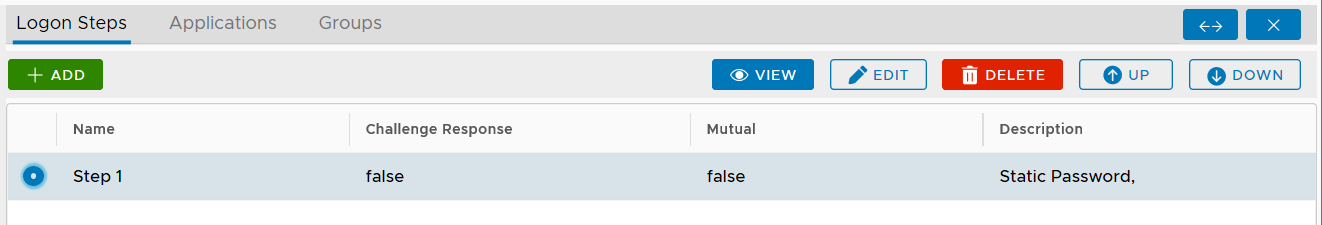
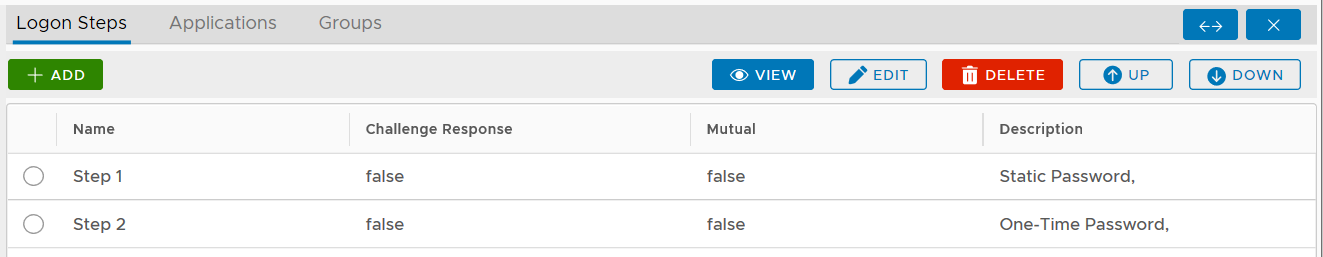
The computer 2FA or MFA logon process is a 2-step or multi-step verification procedure. The first step is the AD credential (i.e. AD password) verification, and the second step is the second factor such as one-time passcode etc. The first factor, i.e. AD password, is always required and actually verified by the AD itself, and the second factor, such as an OTP token or FIDO key, is verified by the DualShield MFA server. Therefore, for 2FA, you only need to add one logon step into the logon procedure and you only need to add a second factor into the logon step.
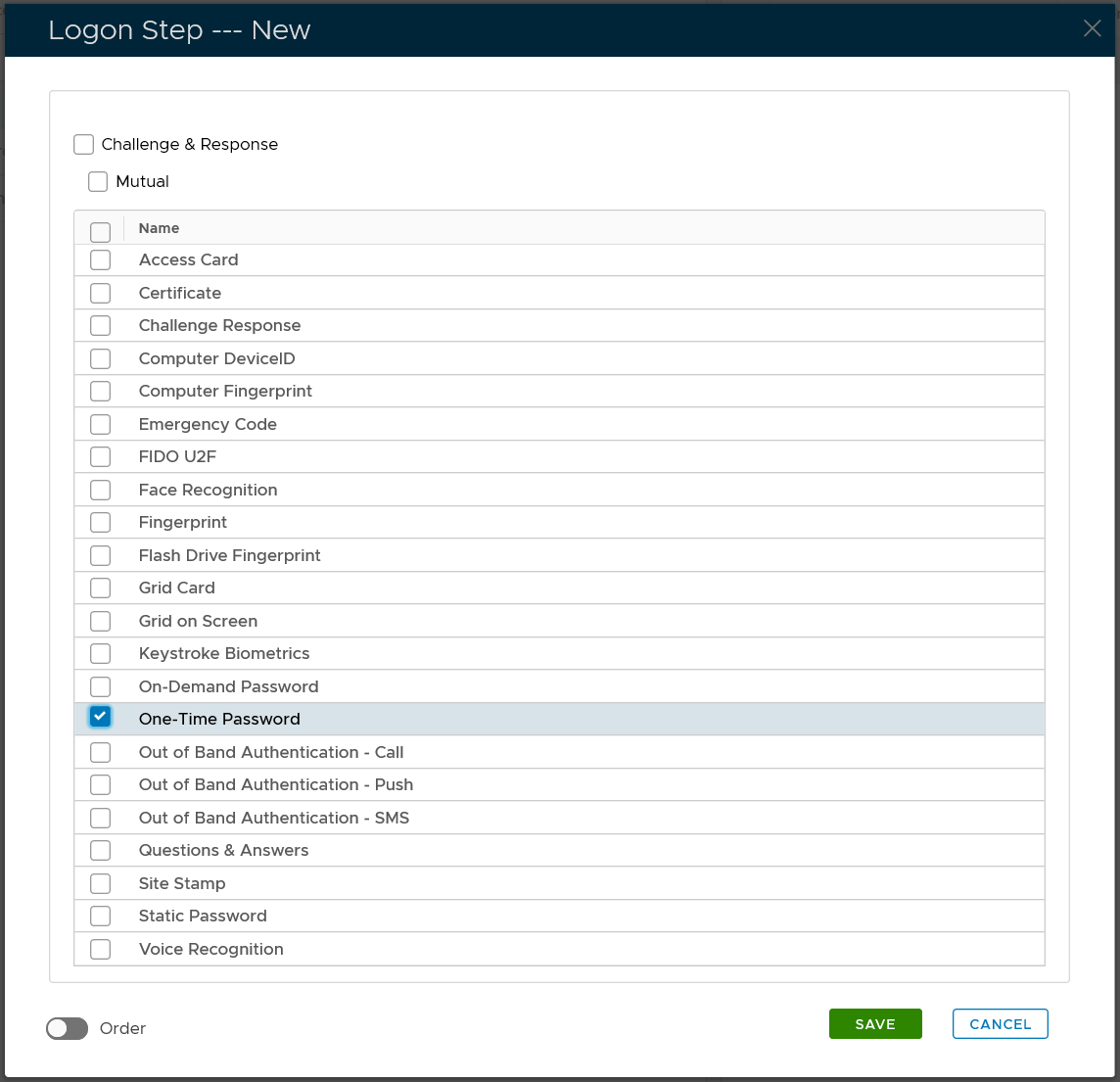
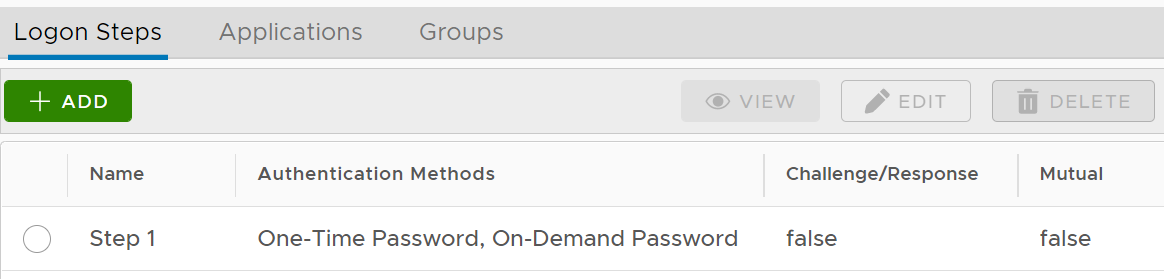
The example below is a logon step that includes 2 authentication options, one-time password and on-demand password, which means that the users will be allowed to authenticate themselves using either of the credentials.