This guide explains how to create a custom installer package for manual installation.
Step 1: Download the off-the-shelf installer package
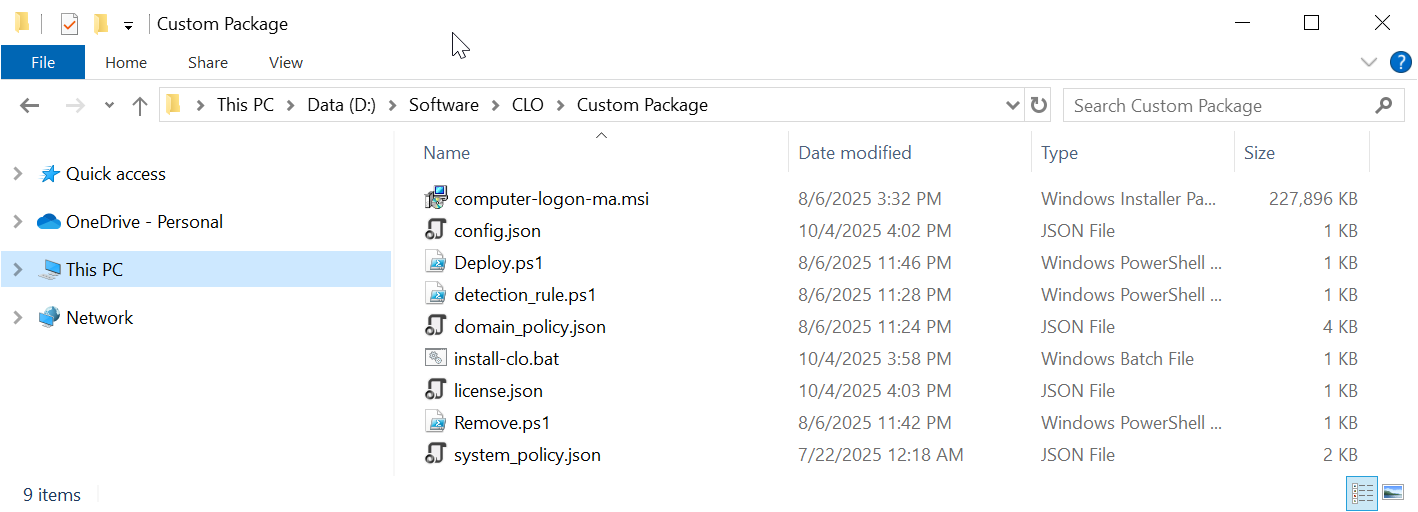
The package contains the following files:
File | Description |
|---|---|
| computer-logon-ma.msi | Computer Logon Agent installer |
config.json | Configuration file |
| license.json | License file |
| domain_policy.json | Domain policy file |
| system_policy.json | System policy file |
| install-clo.bat | Batch commands for custom installation |
| deploy.ps1 | PowerShell commands for Intune deployment |
| remove.ps1 | PowerShell commands for Intune deployment |
| detection_rule.ps1 | PowerShell commands for Intune deployment |
Step 2: Customise the configuration file
Open the config.json in a text editor, such as Notepad
The Computer Logon Modern Authentication supports both Azure AD (Entra ID) joined PCs and On-Prem AD joined PCs. For Entra ID (Azure AD) joined PCs, you must configure the following settings
- MFA server settings in the "AzureAD" data block
- domain_dns_name_list
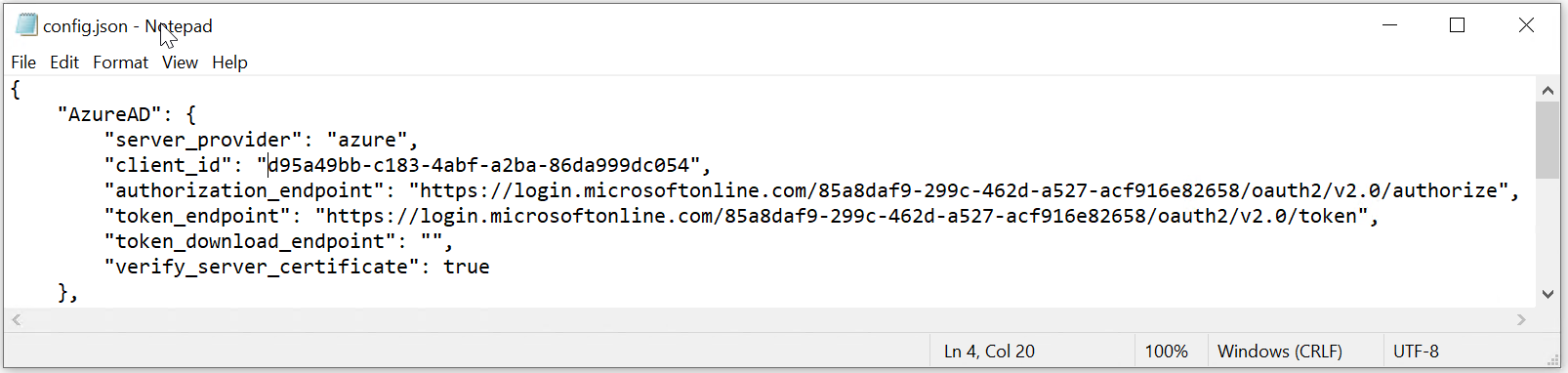
MFA Server Settings
As we are configuring the Computer Logon MA for Entra ID joined PCs, we need to change the settings in the "AzureAD" data block.
Also, as we are using Entra ID MFA as the authentication server, we need to copy some settings from your Entra ID tenant.
authorisation_endpoint
token_endpoint
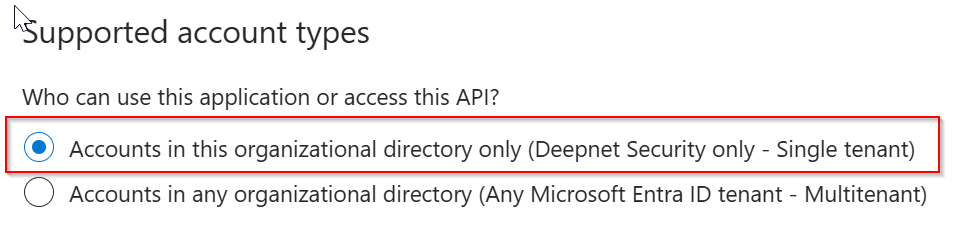
If the application that you have set up in your Entra ID tenant for Computer Logon with MFA supports a single tenant only
Then, in the "AzureAD" block, replace "YOUR-TENANT-ID" in the "authorisation_endpoint" and "token_endpoint" options with your Tenant ID in the Entra ID.
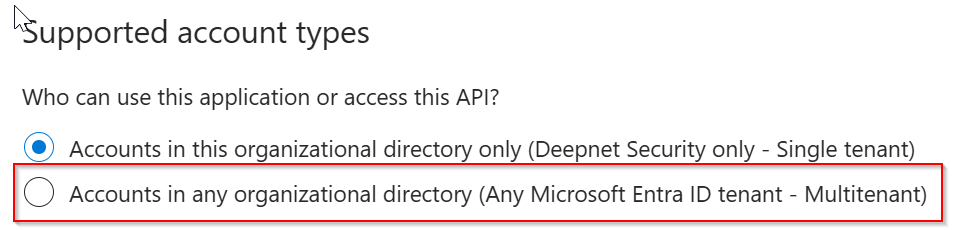
However, if the application you set up for Computer Logon with MFA supports multitenant
Then, in the "AzureAD" block, replace "YOUR-TENANT-ID" in the configuration file with the word "common"
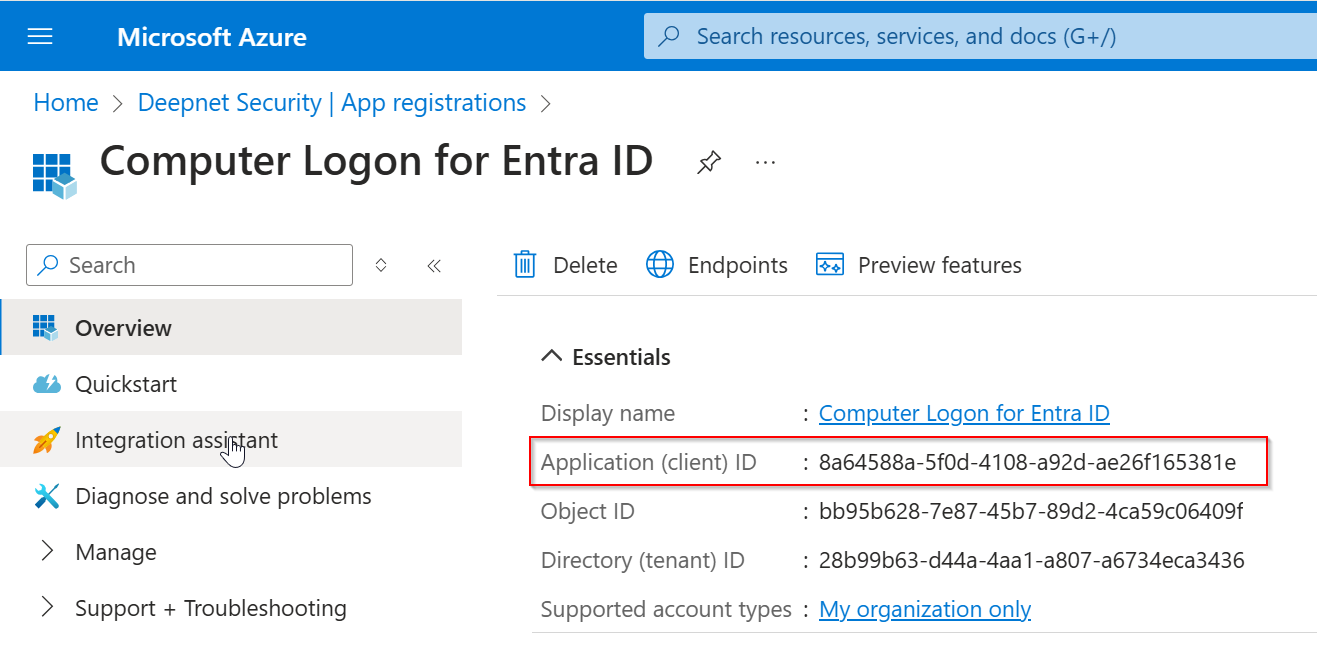
client_id
Next, replace "YOUR-CLIENT-ID" in the "client_id" option with the "Application (client) ID" of the application that you have set up for Computer Logon.
token_download_endpoint
The "token_download_endpoint" is used by the Computer Logon MA agent to download tokens from the MFA server for offline login. Unfortunately, Entra ID MFA does not have this function.
Below is an example:
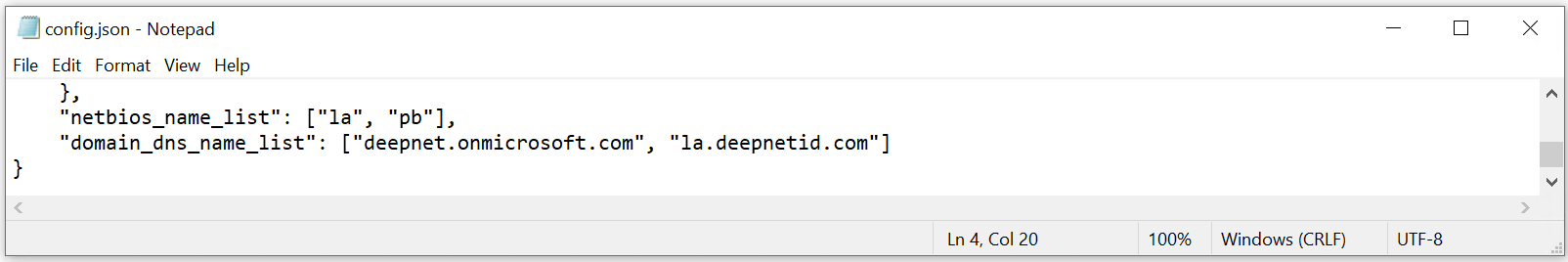
Domain & NetBios Names
Next, you need to add the list of NetBIOS names and domain DNS names used in your organisation. The Computer Logon solution utilizes NetBIOS names and domain DNS names to differentiate between personal and business accounts.
For Entra ID joined PCs, you do not need to add NetBIOS names. But you must enter the list of your domains in the "domain_dns_name_list" variable, such as "deepnet.onmicrosoft.com" and "la.deepnetid.com"
Step 3: Customise the domain policy
- MFA for both Entra ID (Azure AD) domain users and local users.
- MFA at bootup login, screen unlock, and elevated access
- MFA when PC is online & offline
For each scenario, it provides a separate set of options that allow you to control whether or not MFA is required, and the frequency of MFA requirement etc.
Those options are in the "domain_policy.json" file.
Options for Local Users
| online | offline | |
|---|---|---|
| bootup login | local\offline\MfaPolicy\loginMfa | |
| screen unlock | local\offline\MfaPolicy\unlockMfa | |
| elevated access | local\offline\MfaPolicy\uacMfa |
Options for Domain Users
| online | offline | |
|---|---|---|
| bootup login | azuread\online\MfaPolicy\loginMfa | azuread\offline\MfaPolicy\loginMfa |
| screen unlock | azuread\online\MfaPolicy\unlockMfa | azuread\offline\MfaPolicy\unlockMfa |
| elevated access | azuread\online\MfaPolicy\uacMfa | azuread\offline\MfaPolicy\uacMfa |
If you wish to customise some of those options, then you need to edit the "domain_policy.json" file in a text editor and change the corresponding options.
For instances
- if you want to enforce MFA for Azure AD domain users when PC is online on screen unlock, then you need to set the option "azuread\online\MfaPolicy\unlockMfa" to "true"
- if you want to enforce MFA for local users when PC is online on screen unlock, then you need to set the option "local\online\MfaPolicy\unlockMfa" to "true"
Step 4: Customise the license key file
Replace "[YOUR-LICENSE-KEY]" with your license key
Save the file.
Step 4: Create a custom installer package using iExpress
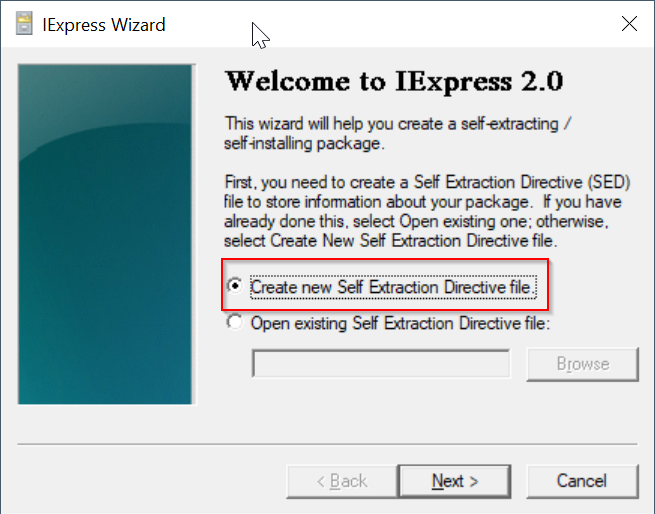
Select the option "Create new Self Extraction Directive file"
Click "Next
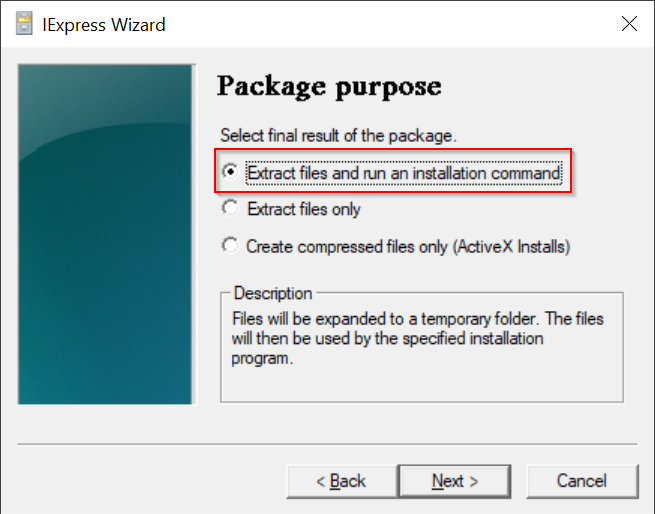
Select the option "Extract files and run an installation command"
Click "Next"
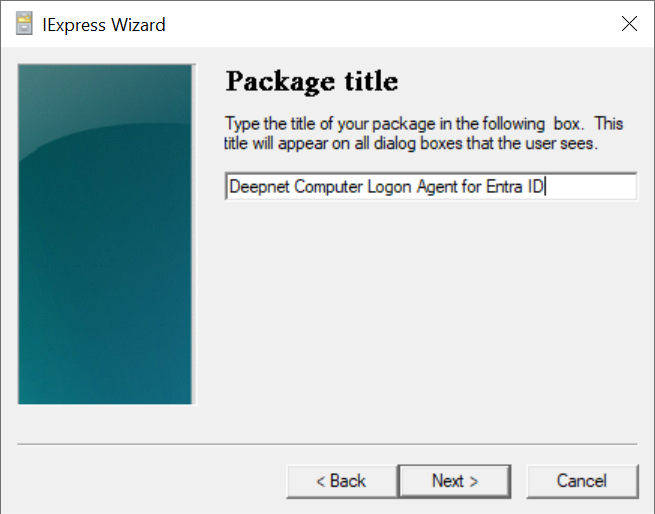
Enter "Deepnet Computer Logon Agent for Entra ID"
Click "Next"
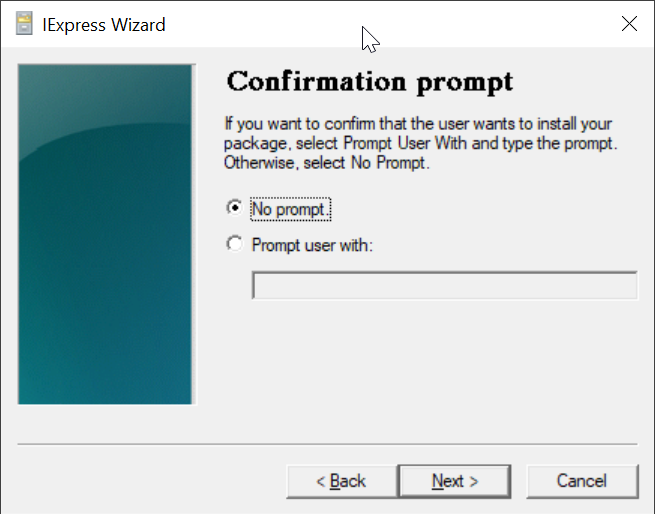
Select "No prompt"
Click "Next"
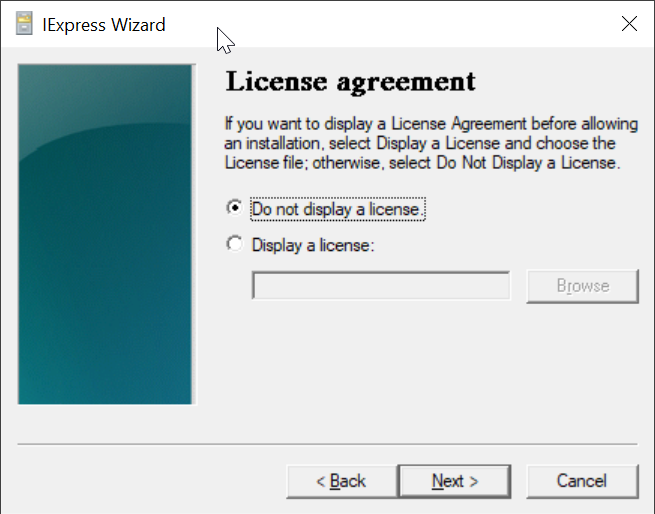
Select "Do not display a license"
Click "Next"
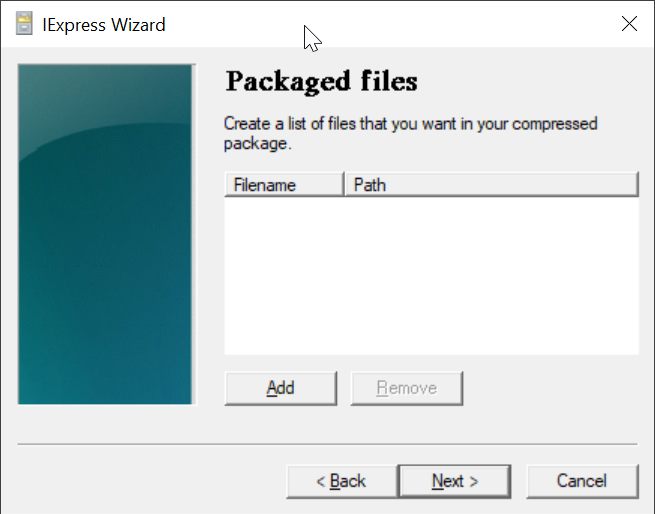
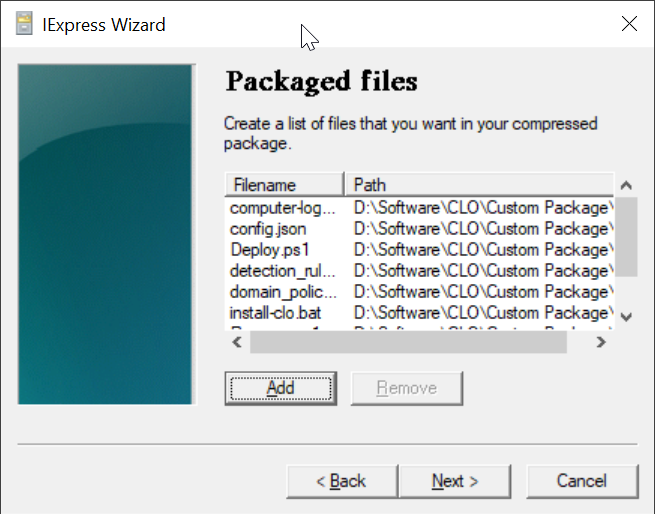
Click "Add"
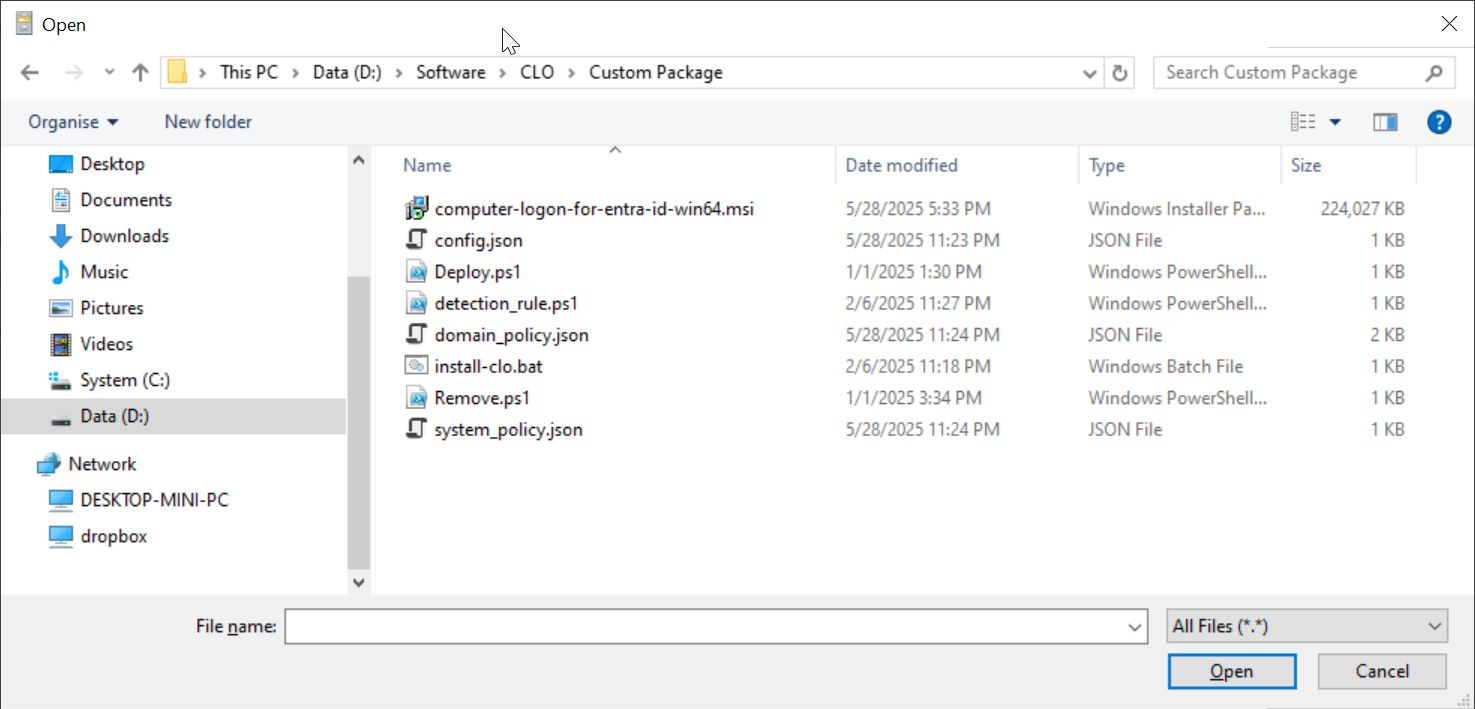
Navigate to the folder where the files are kept, e.g. "D:\Software\CLO\Custom Package"
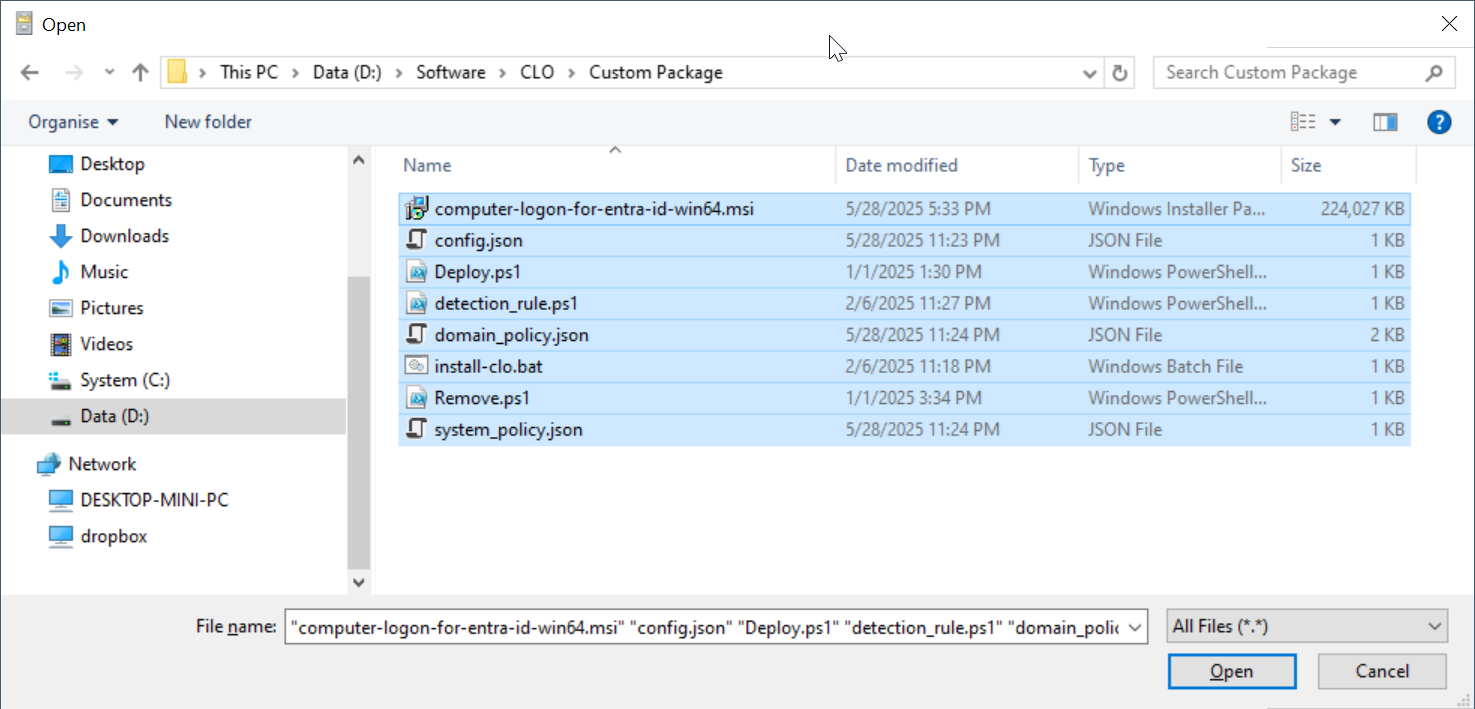
Select all files in the folder
click "Open"
All files are added
Click "Next"
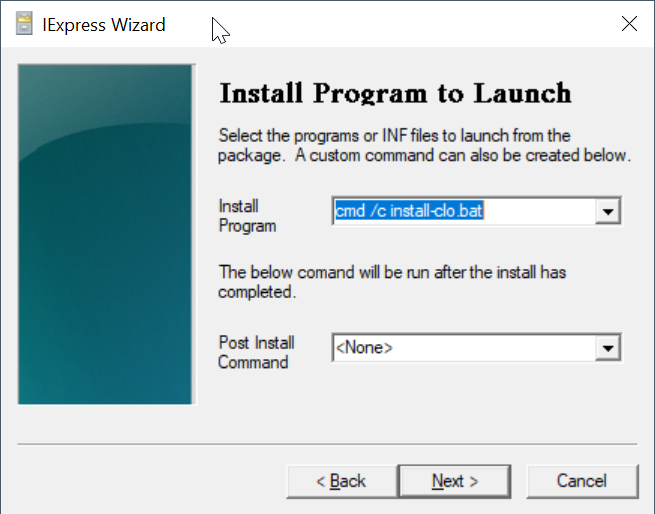
In the "Install Program" box, enter "cmd /c install-clo.bat"
Click "Next"
Click "Next"
Click "Next"
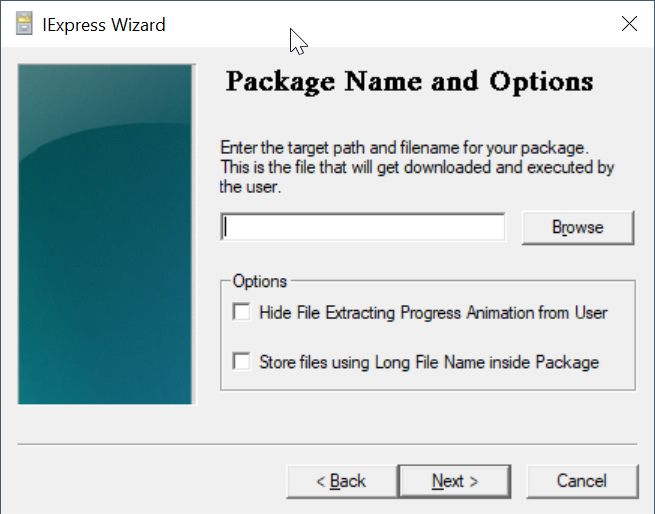
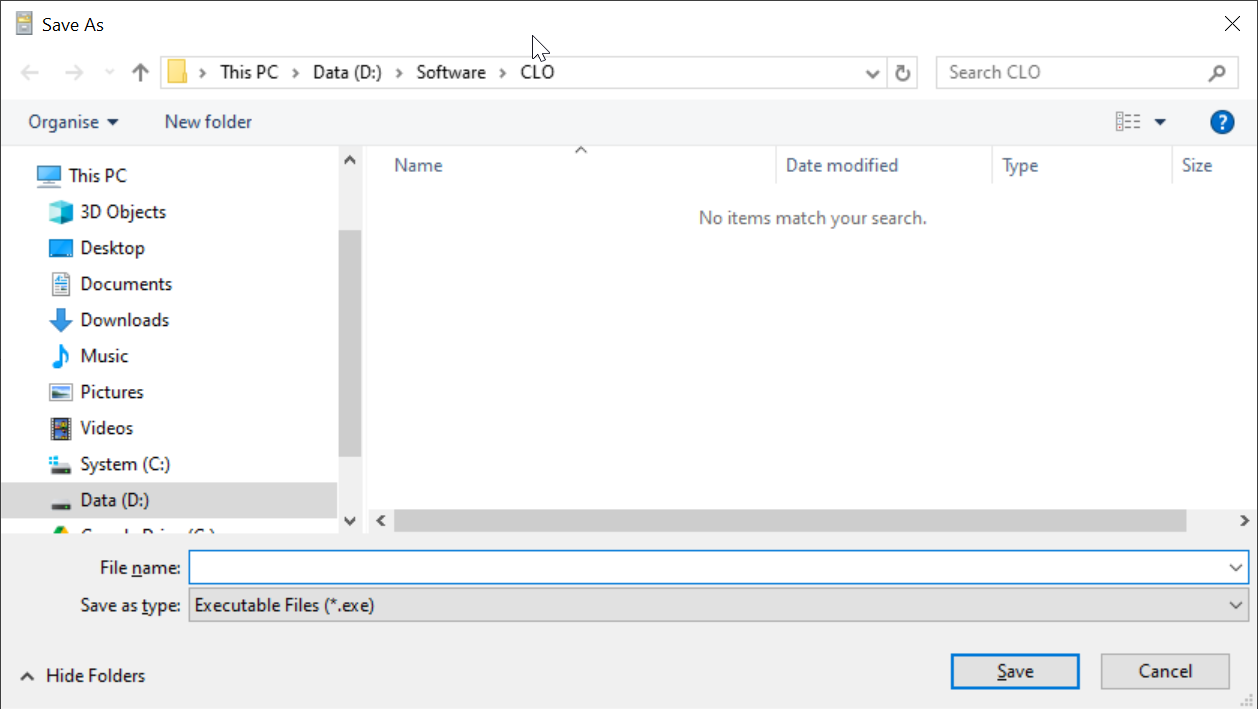
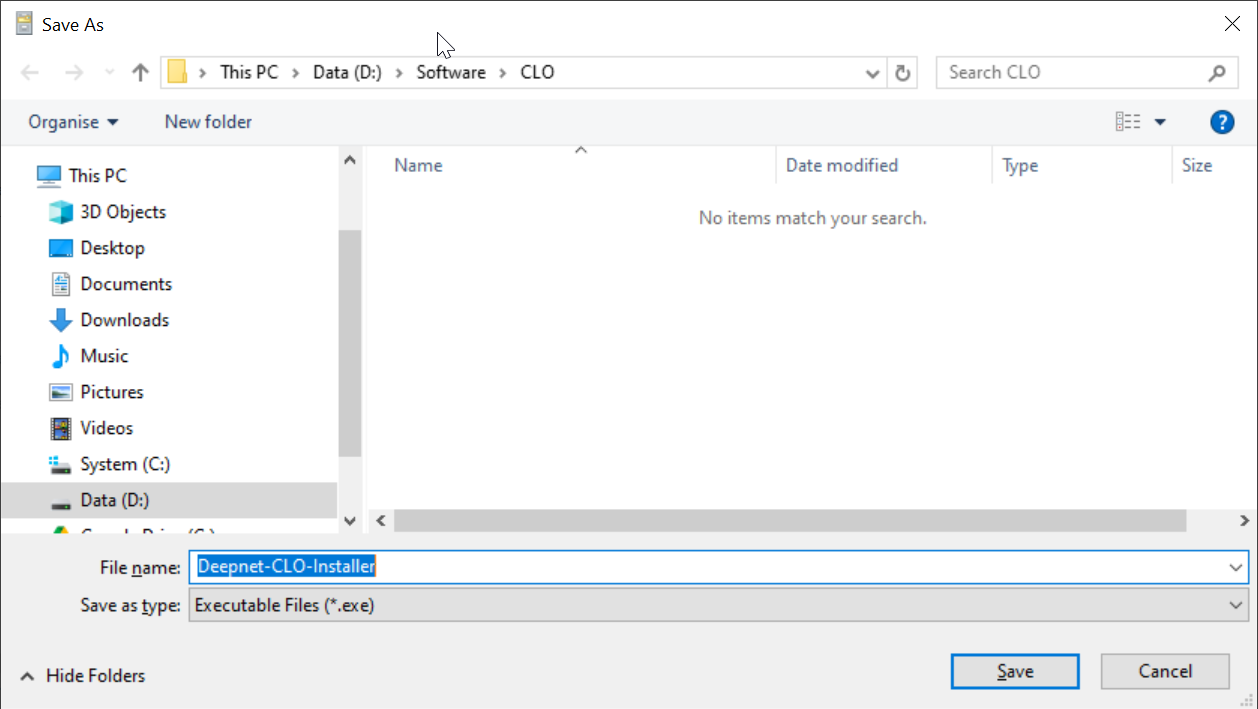
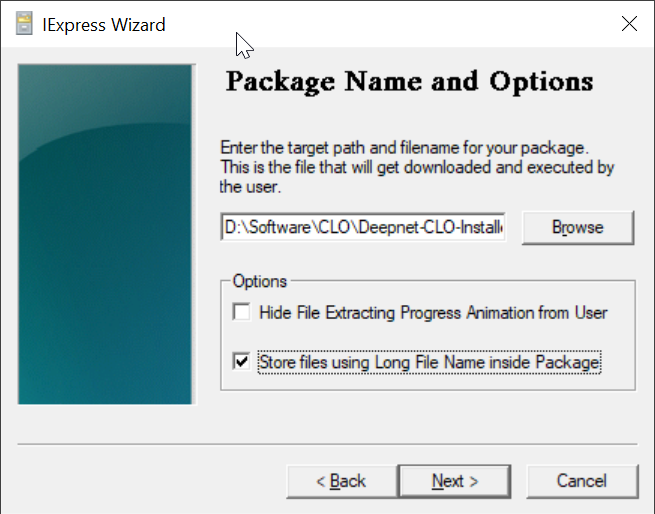
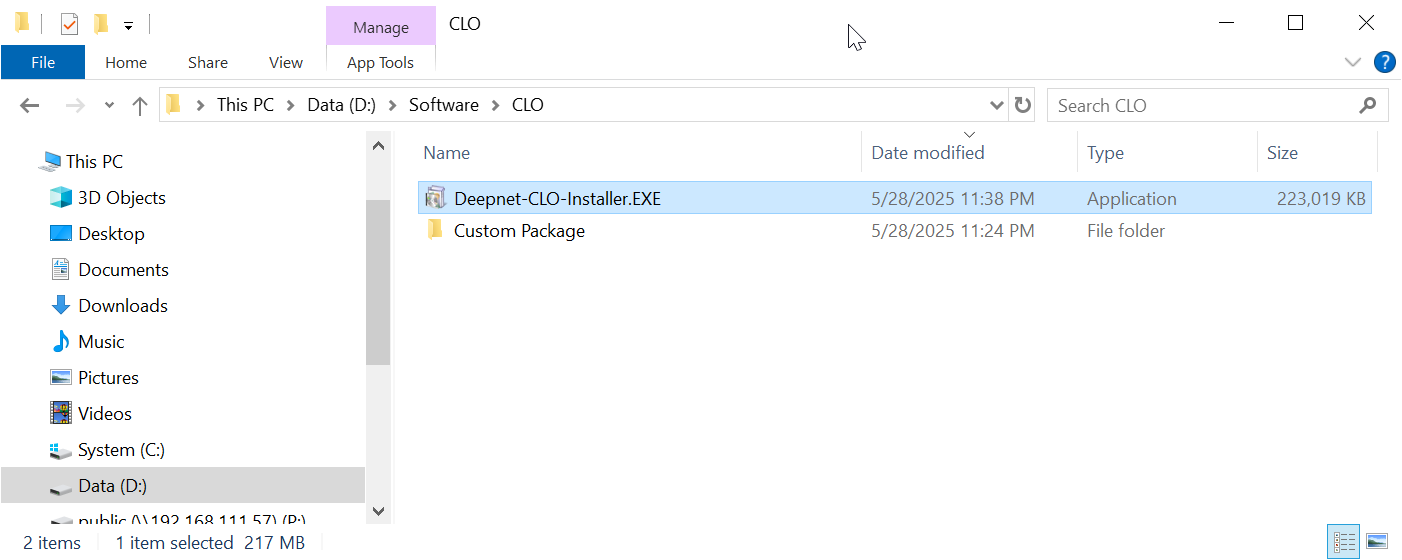
Click the "Browse" button to select a folder where you want to save the custom installer file. e.g. "D:\Software\CLO"
In the "File name" box, enter the name for your customer installer, e.g. Deepnet-CLO-Installer
Click "Save"
Select "Store files using Long File Name inside Package"
Click "Next"
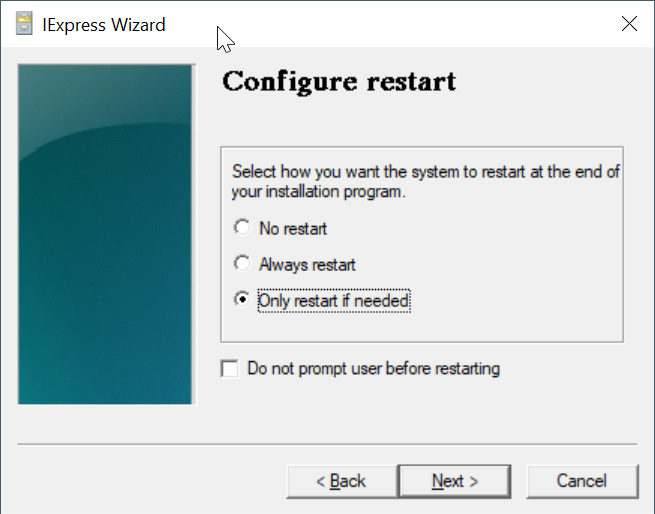
Click "Next"
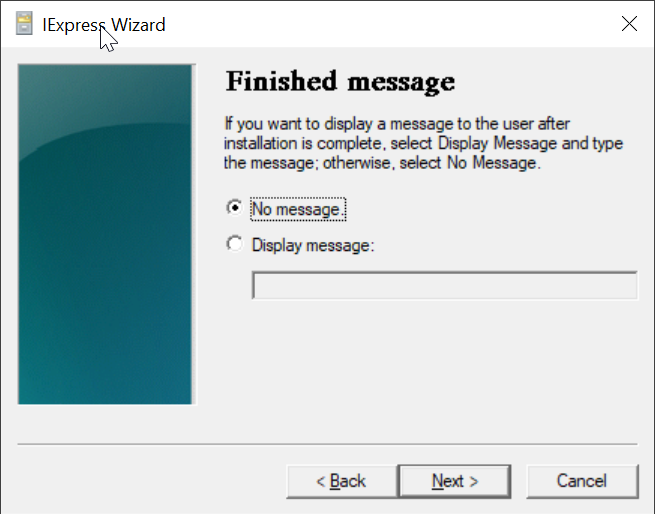
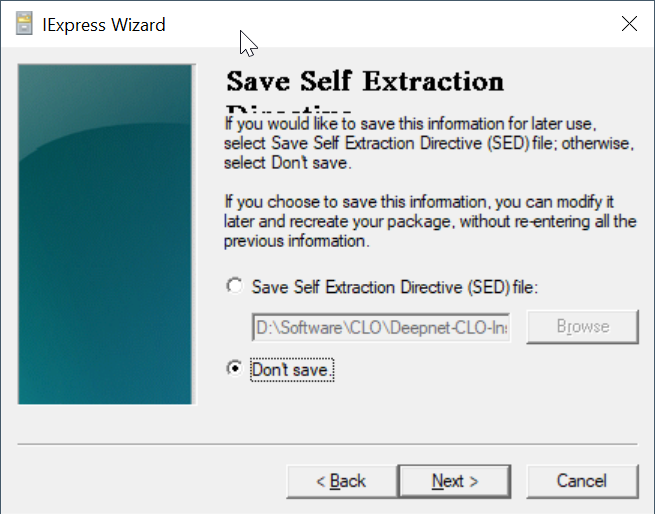
Select "Don't save"
Click "Next"
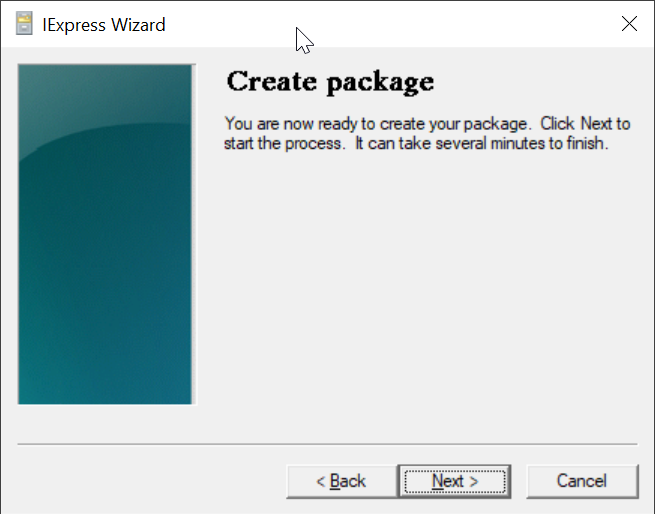
Click "Next"
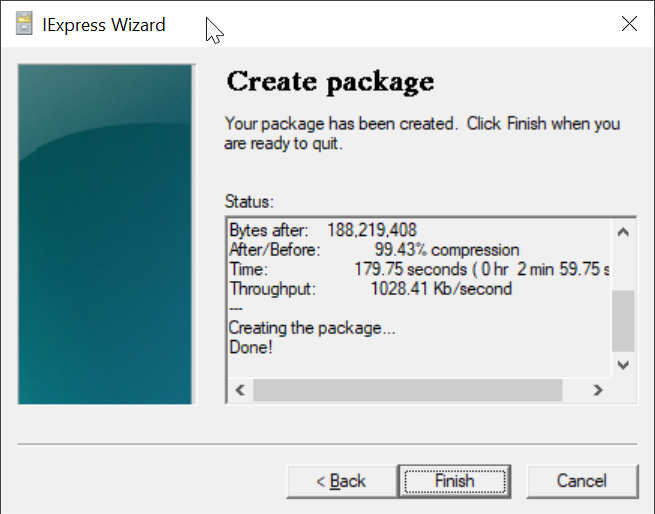
Wait for it to finish
Click "Finish"
Now, you can distribute your custom installer "Deepnet-CLO-Installer.EXE" to your users.