- Created by Adam Darwin, last modified on Feb 13, 2022
Set up Deployment Service
Mobile Push Authentication requires the DualShield Deployment Service (DDS) to be accessible from the public network. DDS is used to deploy the MobileID app.
Set up Logon Procedure
Logon Procedure defines how users will be authenticated when they attempt to login to the portal. You can define a logon procedure of 1-step, 2-step and 3-step verification, for instance.
In the Admin Console, select "Logon Procedures"

There is a pre-defined logon procedure named "Deployment Service".
To change its logon steps, click its context menu, select "Logon Steps"

You can define the logon steps according to your own requirements

Set up Application
In the Admin Console, select "Applications"

There is a pre-defined application named "Deployment Service"
Normally, you do not have to make changes to the default setup.
Set up Realm
Realm is a group of user domains. It defines who is allowed to access the application that's associated with the realm.
In the Admin Console, select "Realm"

There is a pre-define realm named "Deployment Service"
You must change the domains that are to be included in this realm, e.g. deepnetid.com
Set up SSO Service
Mobile Push Authentication requires the DualShield SSO service to be accessible from the public network. SSO provides the function of OOBA registration and verification.
Configure Policy Settings

Enable OOBA (Out-of-Band Authentication)
To enable or Disable Out-of-Band Authentication
OOBA URL
In DualShield 6, OOBA registration and verification functions are provided by the DualShield SSO service. In a DualShield system in which there are multiple DualShield SSO servers, e.g. one in the frontend and one in the backend, then you must specify the SSO server that is to be used for OOBA by entering the FQDN of the SSO server in this entry.
Registration Authentication
- Always ask the user to verify the password when registering a new device
When a user attempts to register a device for OOBA, password authentication is required.
- Only ask the user to verify if the link session timed out
When the registration link has timed out, password authentication is required.
Registration Session Timeout
Defines the timeout period of the registration link.
Logon Request Timeout
Defines the timeout period of the logon request.
Enforce Local Authentication
If this option is enabled, then users must be verified by the specified local authentication in order to approve a push authentication request
Local Authentication Method
Define the local authentication method to be used to verify the user
Configure Logon Procedure

Register MobileID App
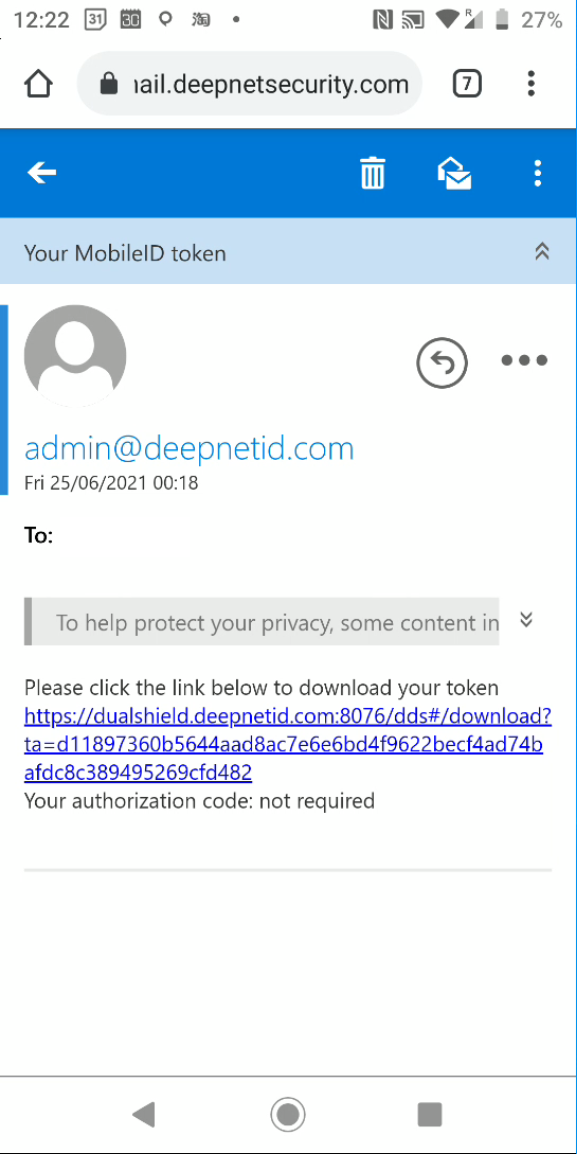
Please note: 'Your-Dualshield-FQDN:8074' must be accessible to your mobile devices in order for the MobileID token to register for OOBA services.
There are several ways of installing a MobileID token. However, in order to register a token for OOBA, you must install the token by QR code or by link.
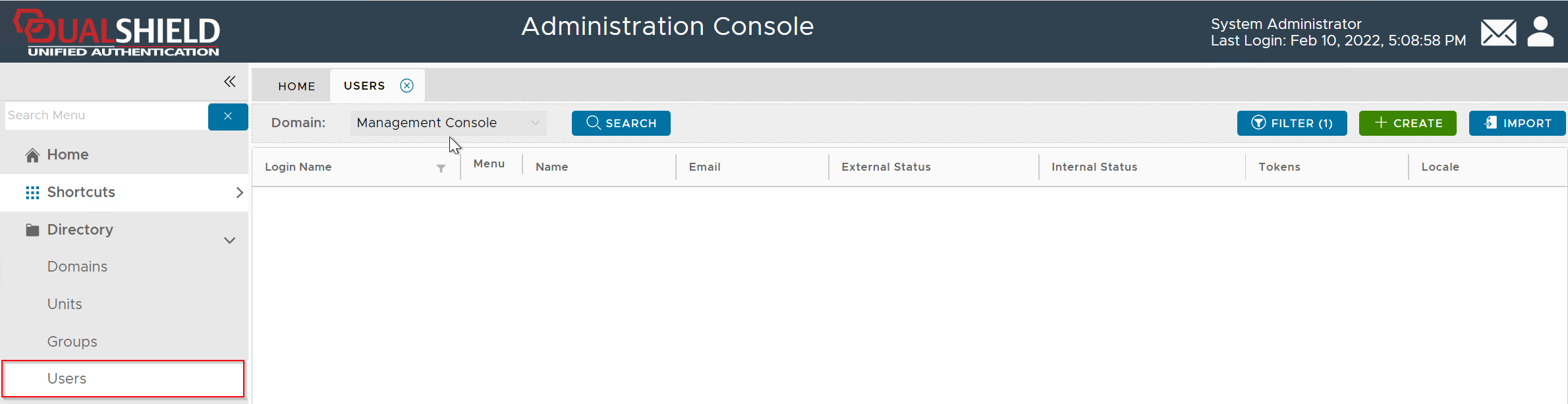
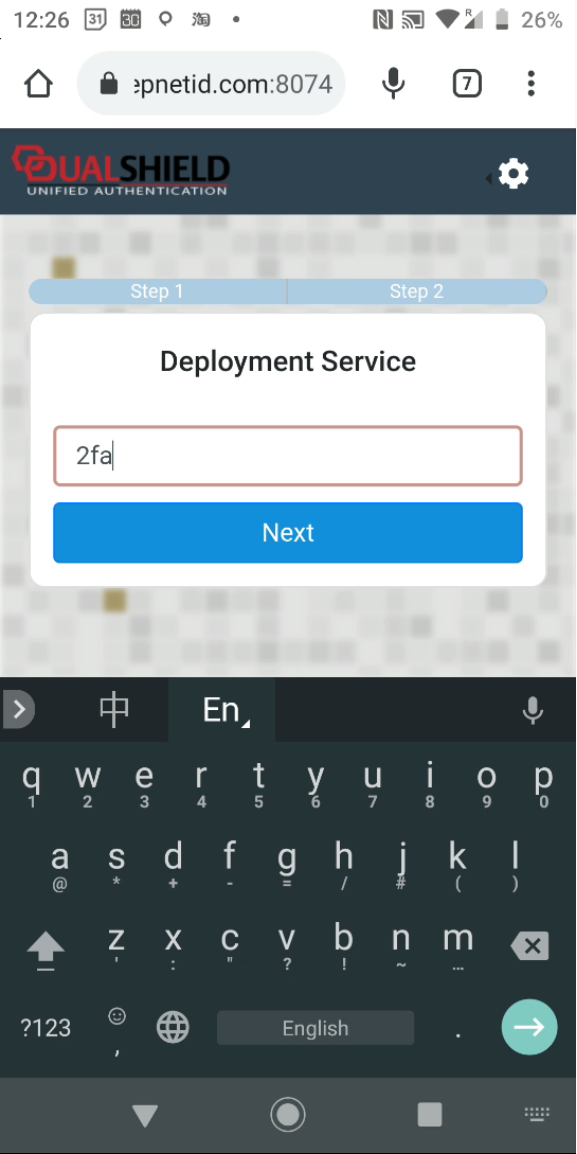
In the Domain list, select the domain that you want to work on, e.g. DeepnetMFA.com
If you click the "Search" button, it will list all users in the entire directory up to the query limit.
To narrow down your search, click the "Filter" button
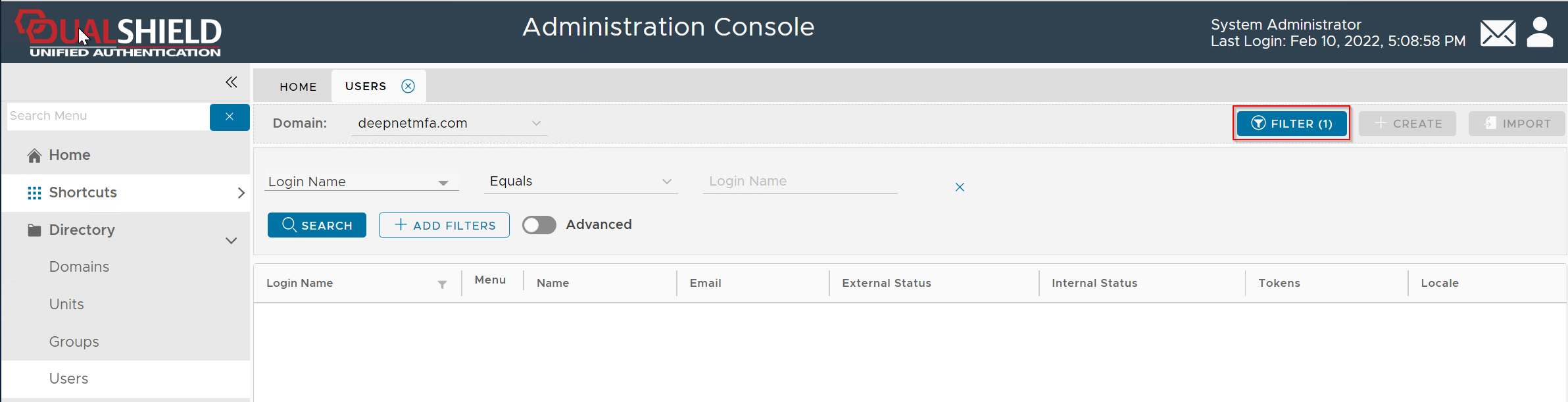
Enter the user's login name, e.g. 2FA, then click the "Search" button (You can change the search filter or add more filters)
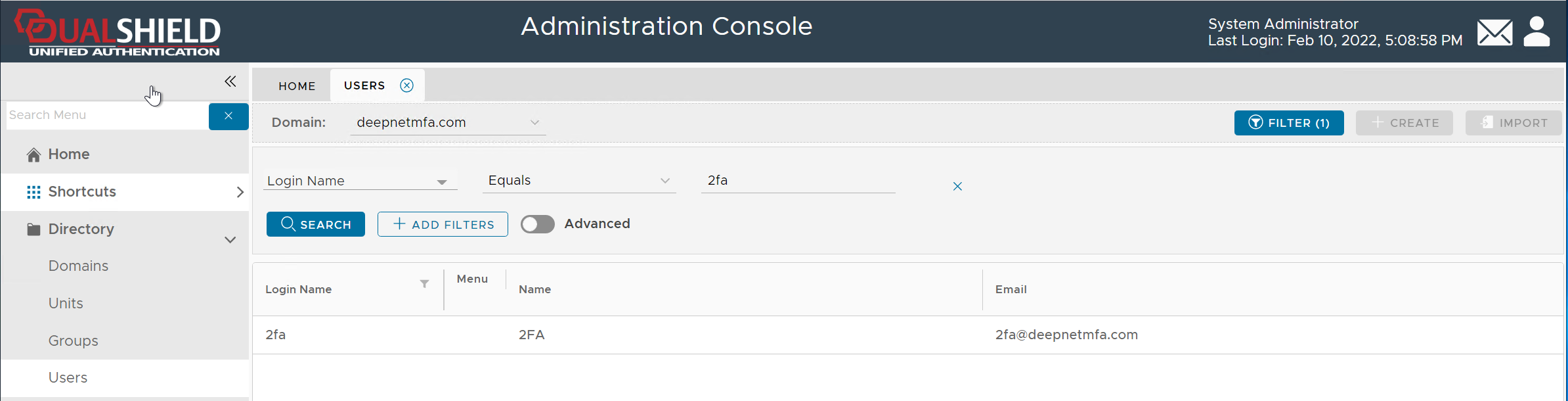
Once you have found the user account, click on its context menu icon "..." to bring up the context menu:
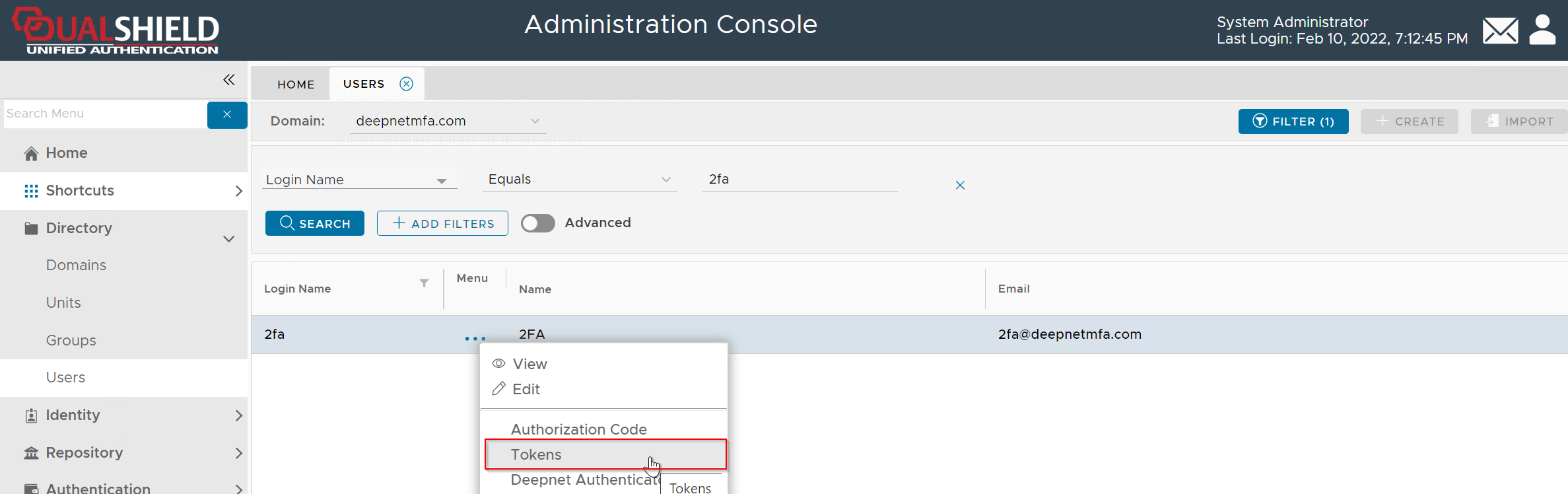
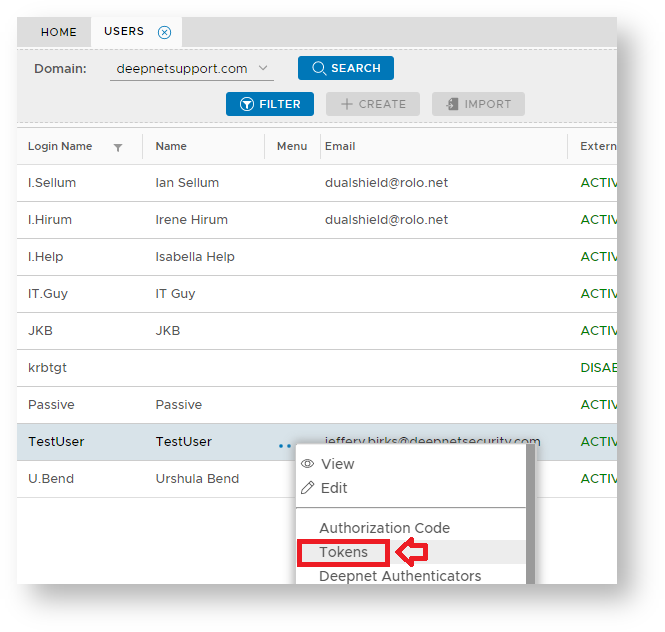
Click "Tokens" from the context menu
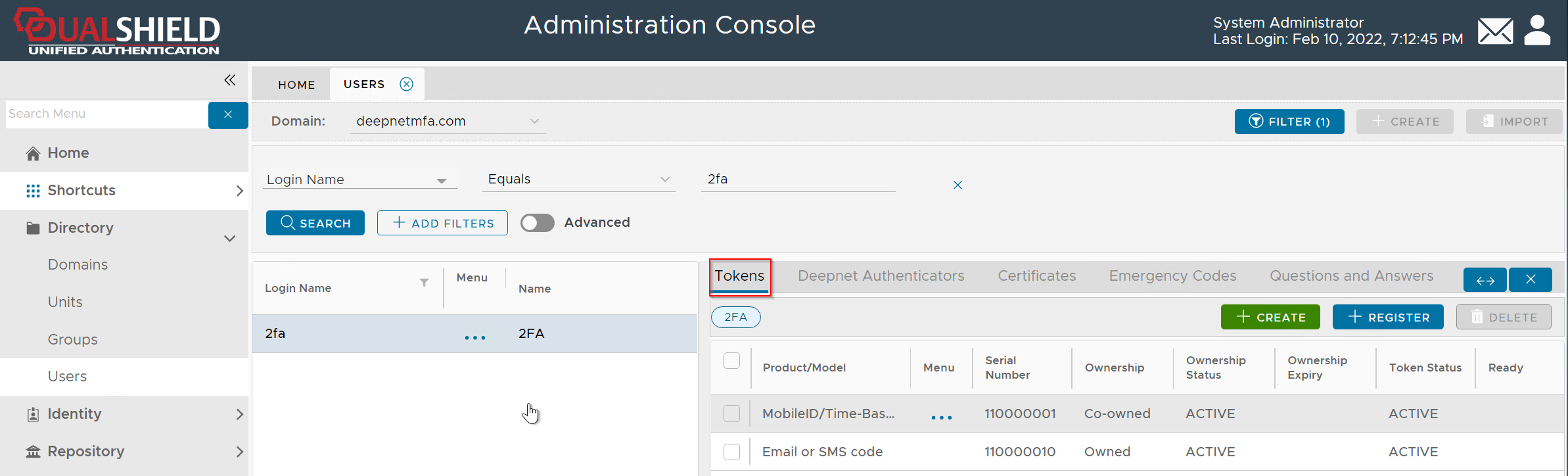
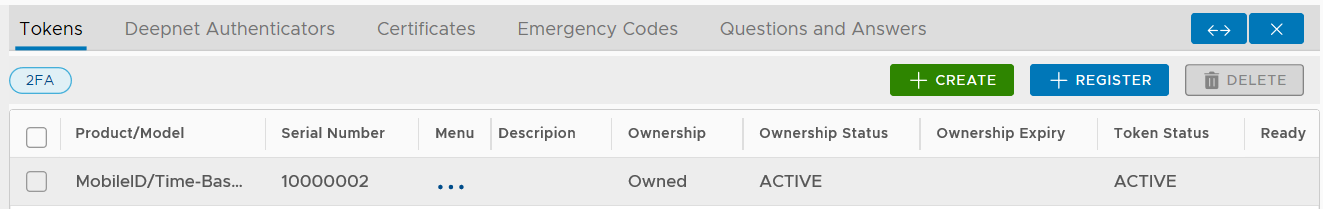
Now, click the token's context menu icon "..." to bring up its context menu:
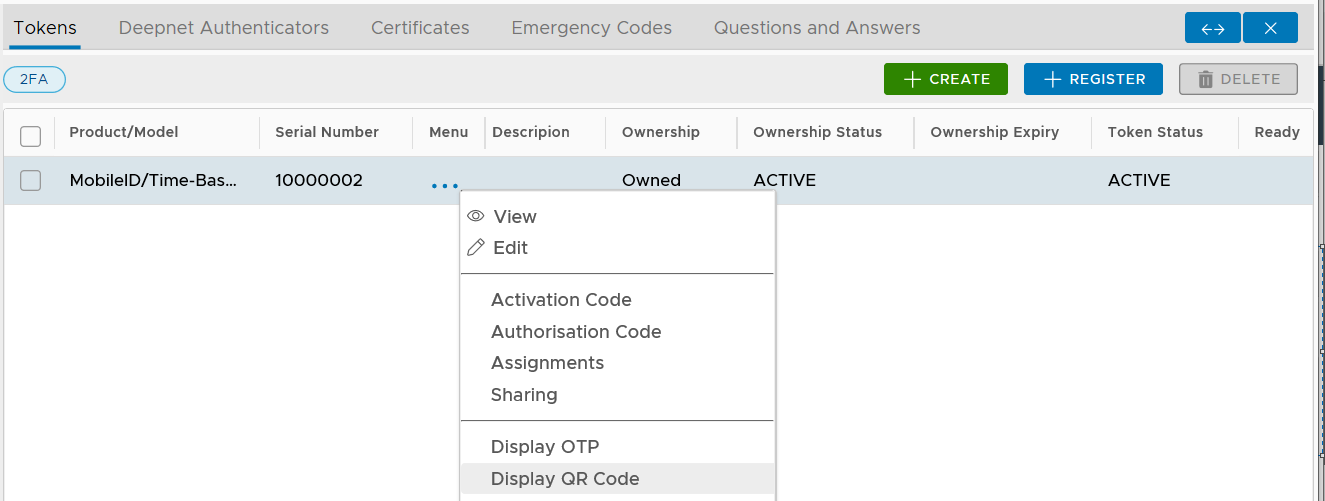
Select "Display QR Code"
Find the MobileID token, click its context menu
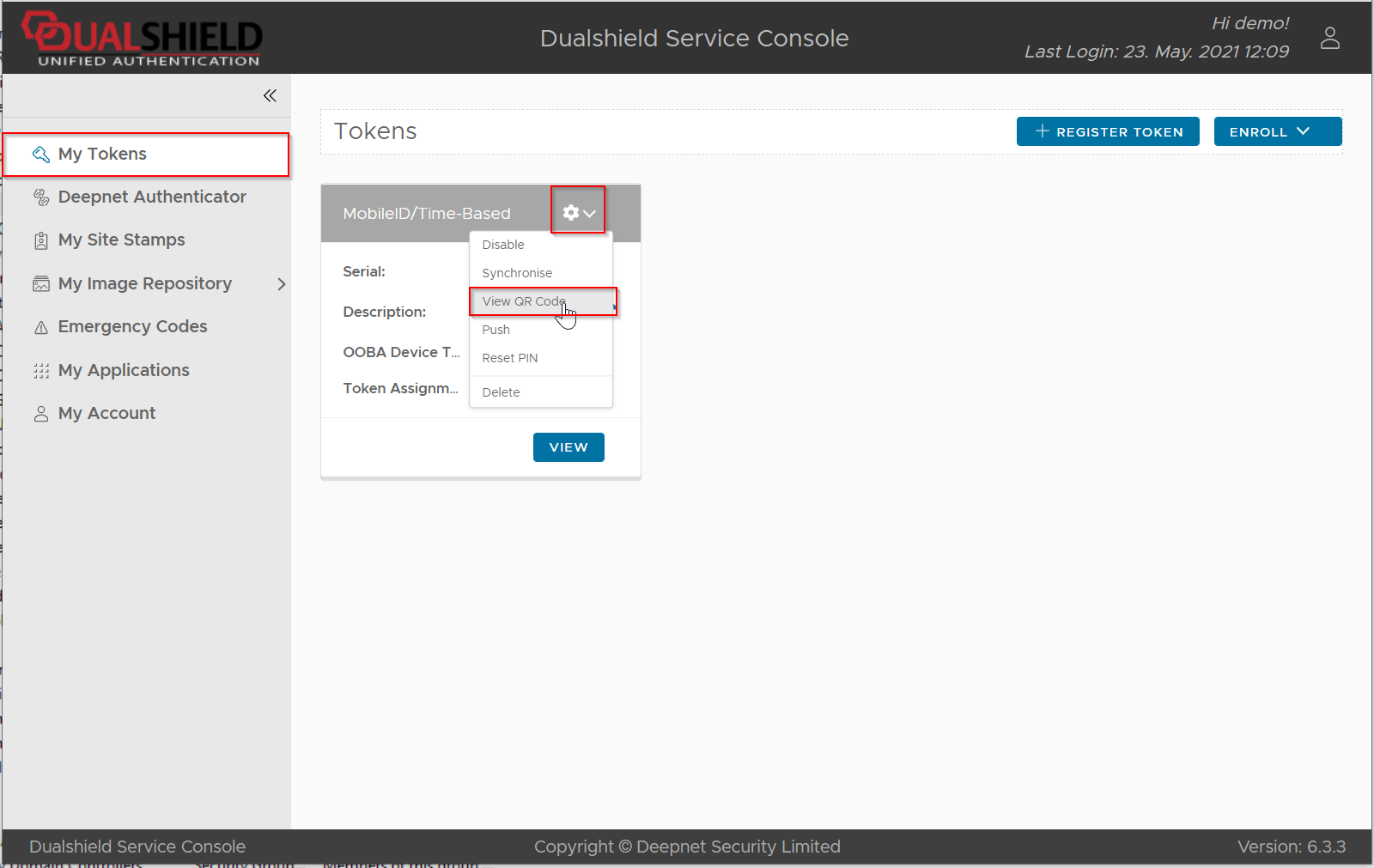
Select "View QR Code" from its context menu
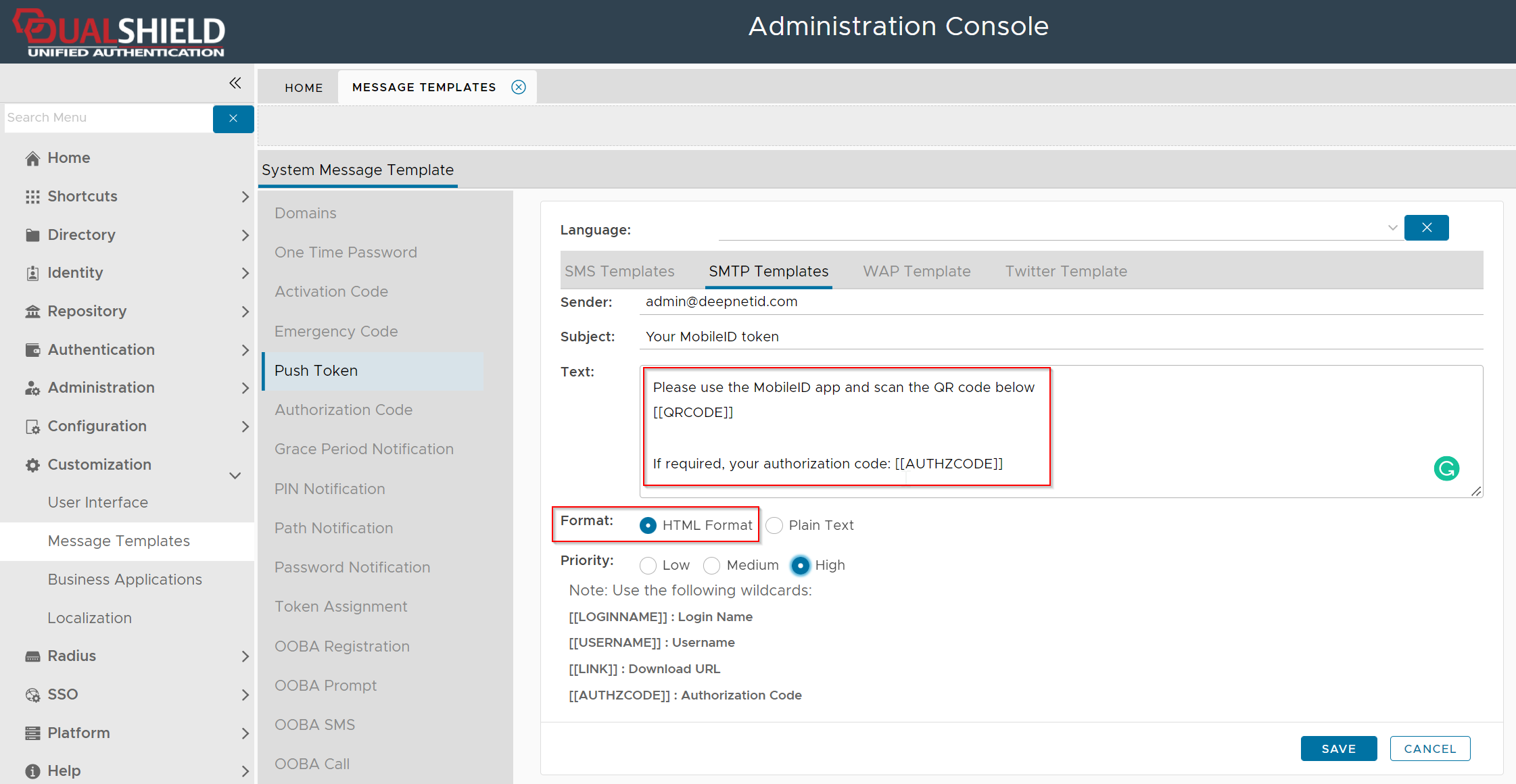
A token can be pushed to the user by the server automatically or pushed to the user manually by the administrator in the admin console. Either way, a message template called "Push Token" will be used to create the email message. Therefore, you must customize the Push Token message temple first if you want users to receive their token's QR code by email.
Customize Push Token Message Template
You must customize the message template according to your requirements.
SMTP Template
If you want the server to push OTP tokens to users by email, then you need to customize the SMTP Template
Navigate to Customization | Message Templates | Push Token | SMTP Templates
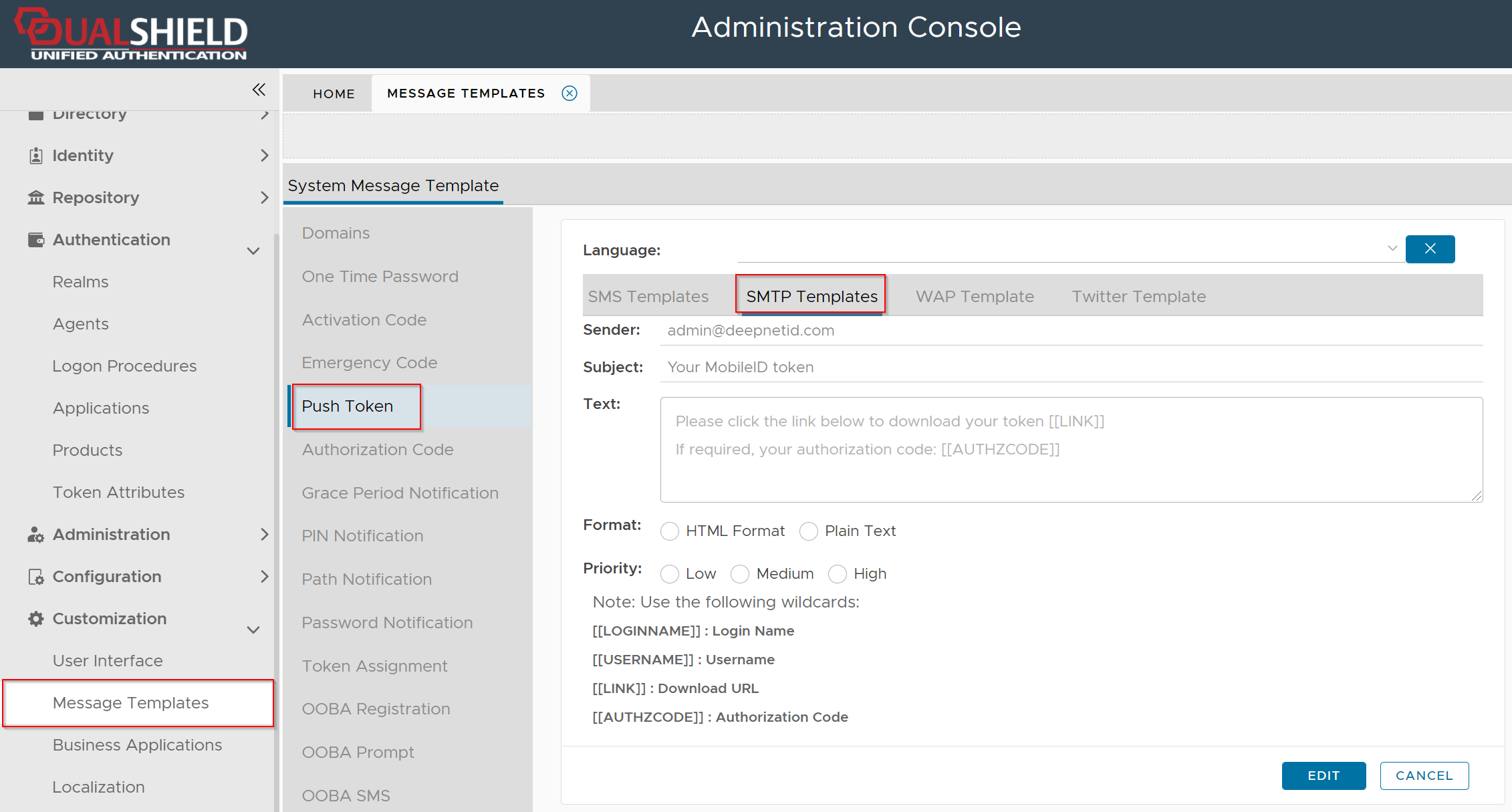
Typically, you would need to change the Sender, Subject, and Text field which is the body of the message.
There are 3 wildcards that you can use in the message body depending on your requirements
| Wildcard | Remarks | Examples |
|---|---|---|
[[LINK]] | This wildcard represents the download link of the user's MobileID token. Use this wildcard if you want to send the token's download link to the user. |
|
[[QRCODE]] | This wildcard represents the QR code image of the user's OTP token. Use this wildcard if you want to send the token's QR code to the user. |
|
[[AUTHZCODE]] | Depending on the token's policy, installing an OTP token might require an authorization code. This wildcard represents the authorization code of the user's token if it is required. |
You must select "HTML Format" if include the wirldcard [[QRCODE]] in the message text.
SMS Template
If you want the server to push OTP tokens to users by SMS message, then you need to customize the SMS Template
Navigate to Customization | Message Templates | Push Token | SMS Templates
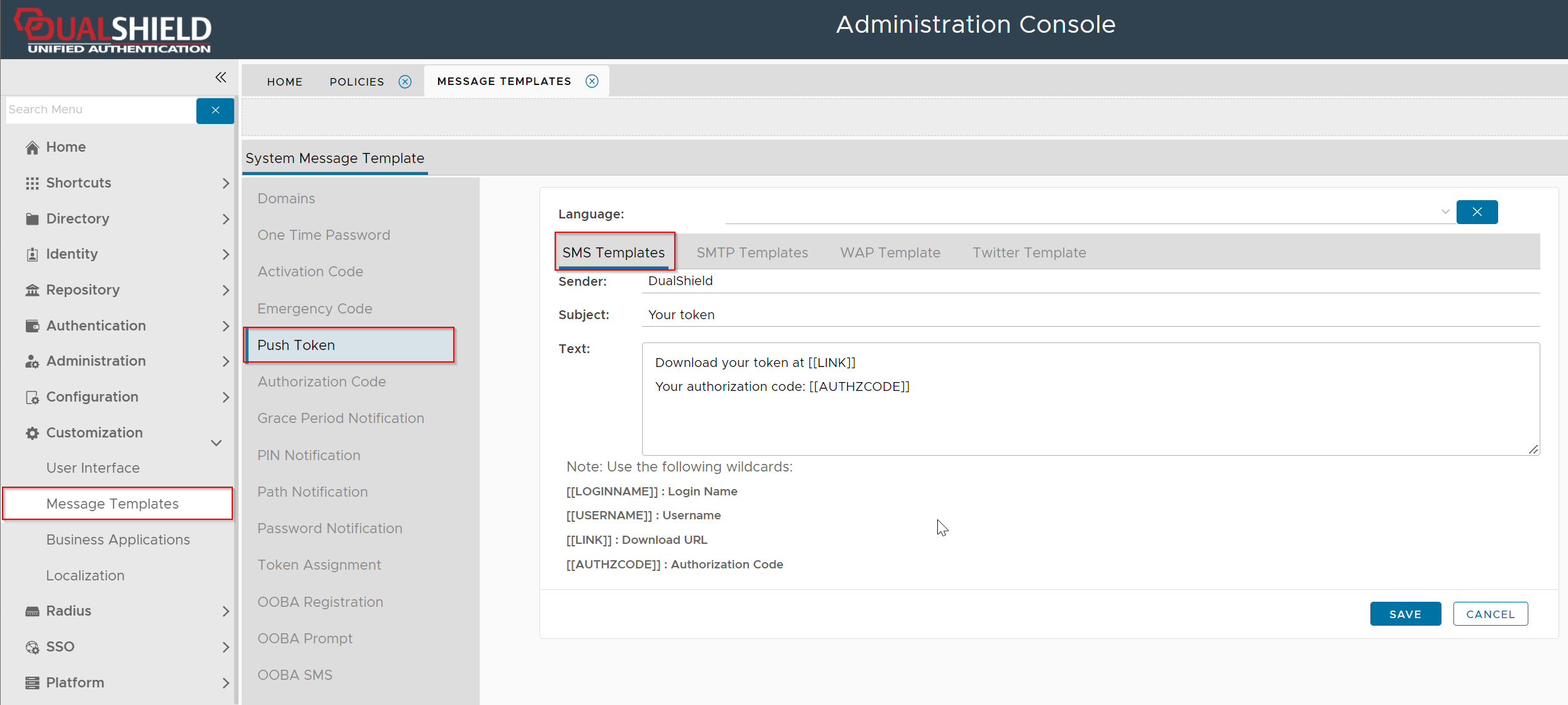
Below is an example of the Push Token SMTP message template
Push Token Manually
The following procedure demonstrates how the system administrator can send the QR code to users by emails
Navigate to "Directory | Users", select the domain for your external directory, then for a selected user left click on the context menu and select "Tokens";
The token details for the selected user will now be show, left click on the context menu of the token to be pushed to the user then select the message channel to send the token (normally "By Email");
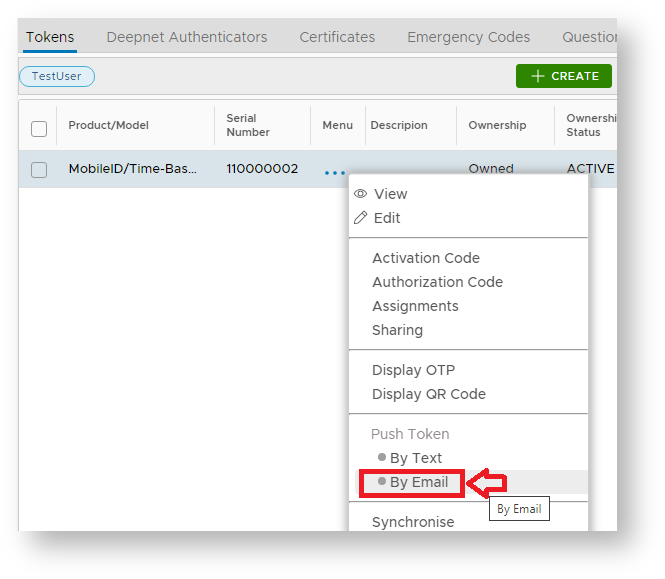
The QR code for the selected token will now be sent to the user by email.
End User Experience
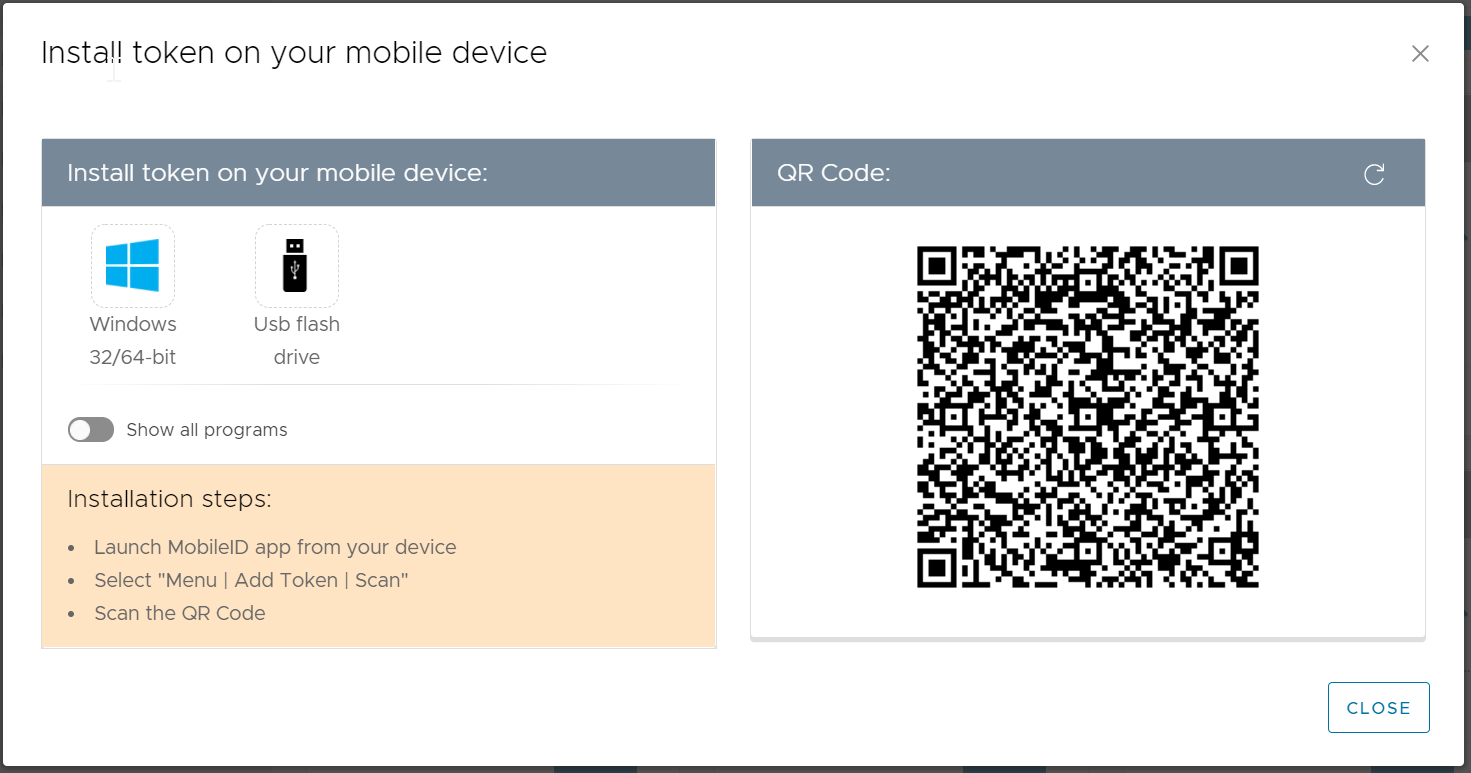
Once the token has been sent to the user an email will arrive that includes the required QR code (example below);
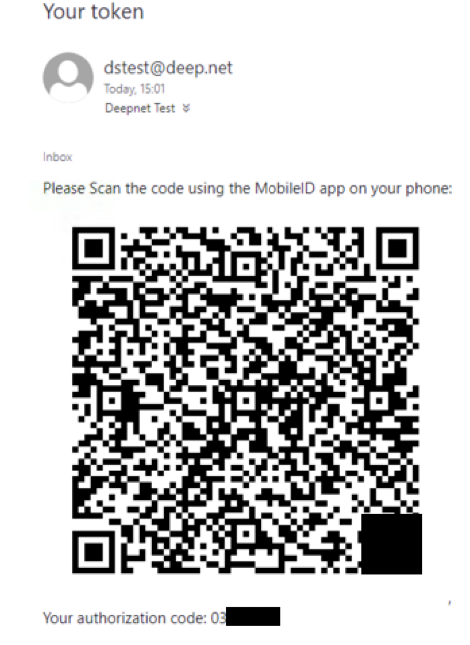
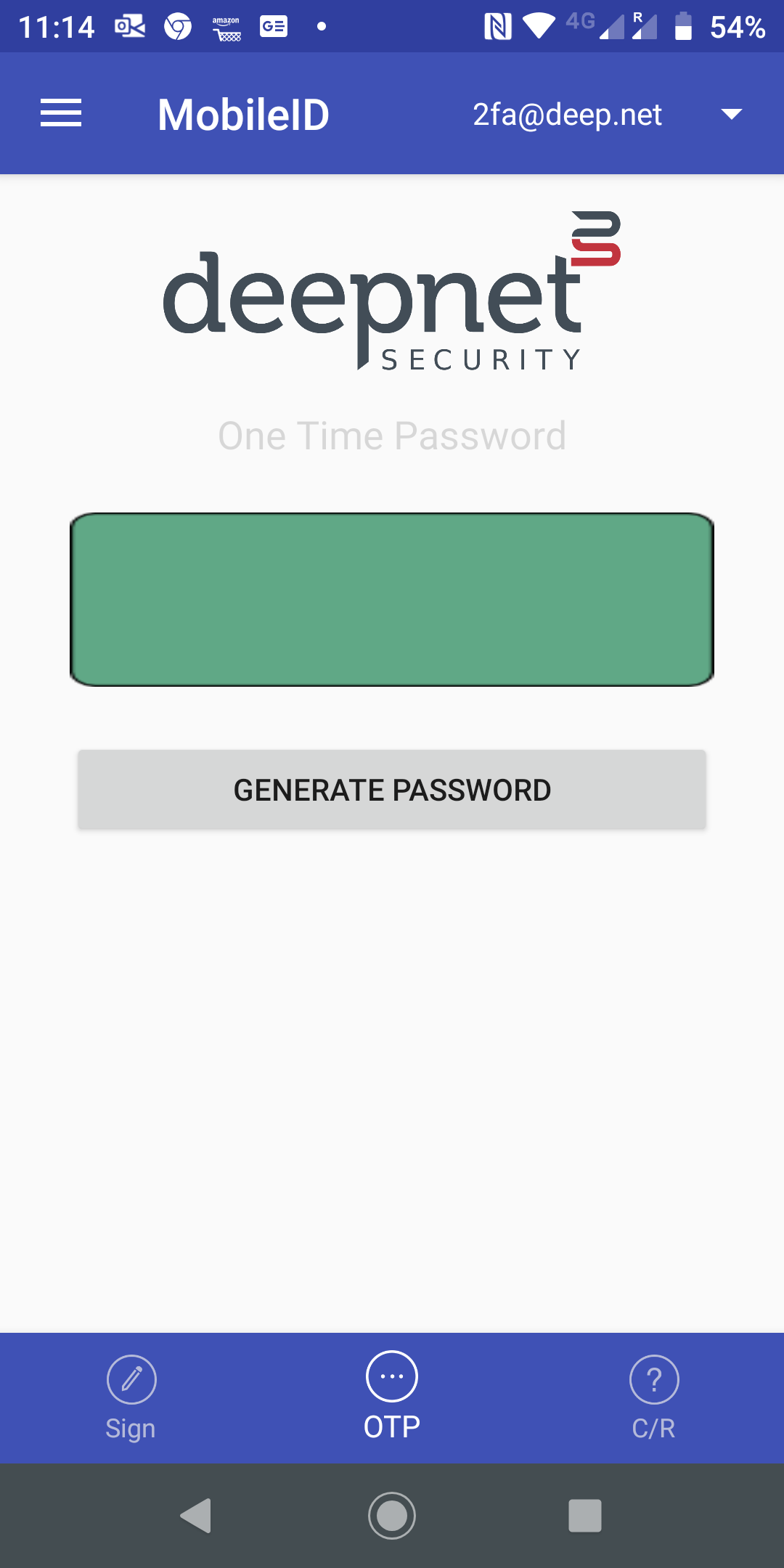
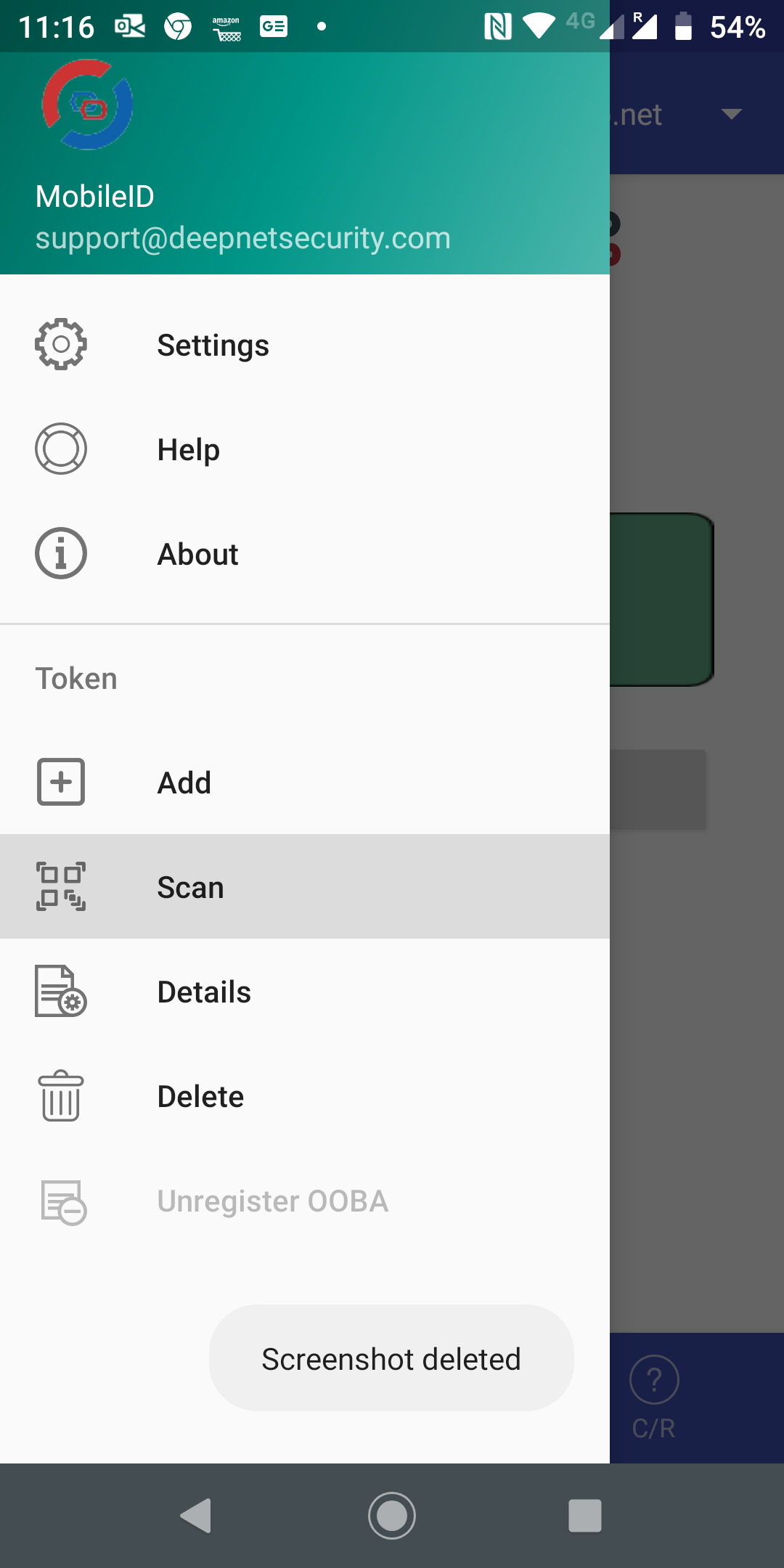
Now, open the MobileID app on your smartphone
click the menu icon on the top-left corner
select Scan to start the QR code
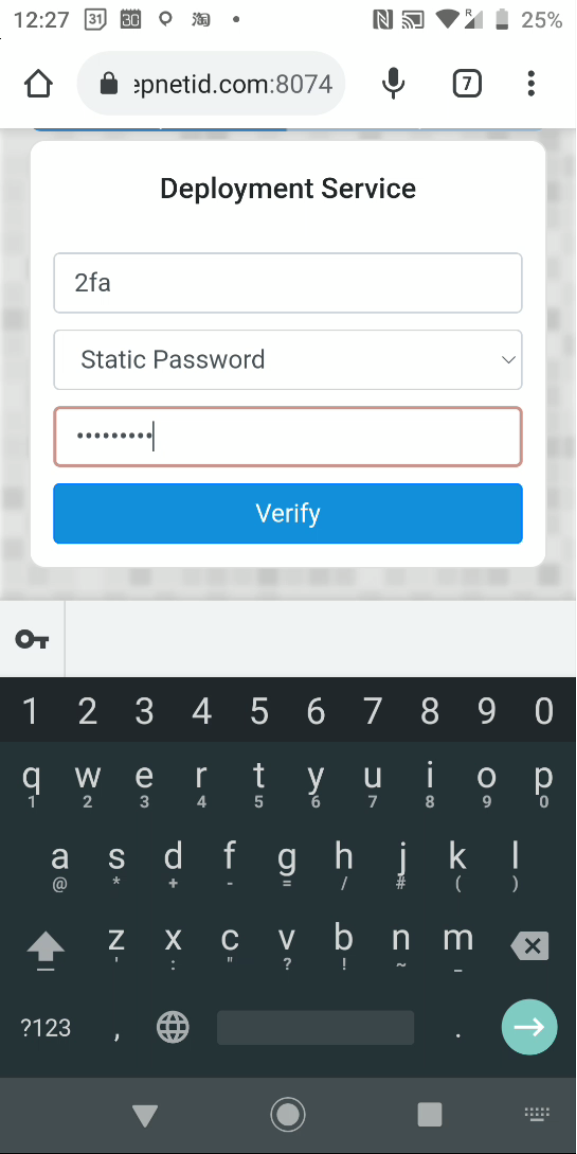
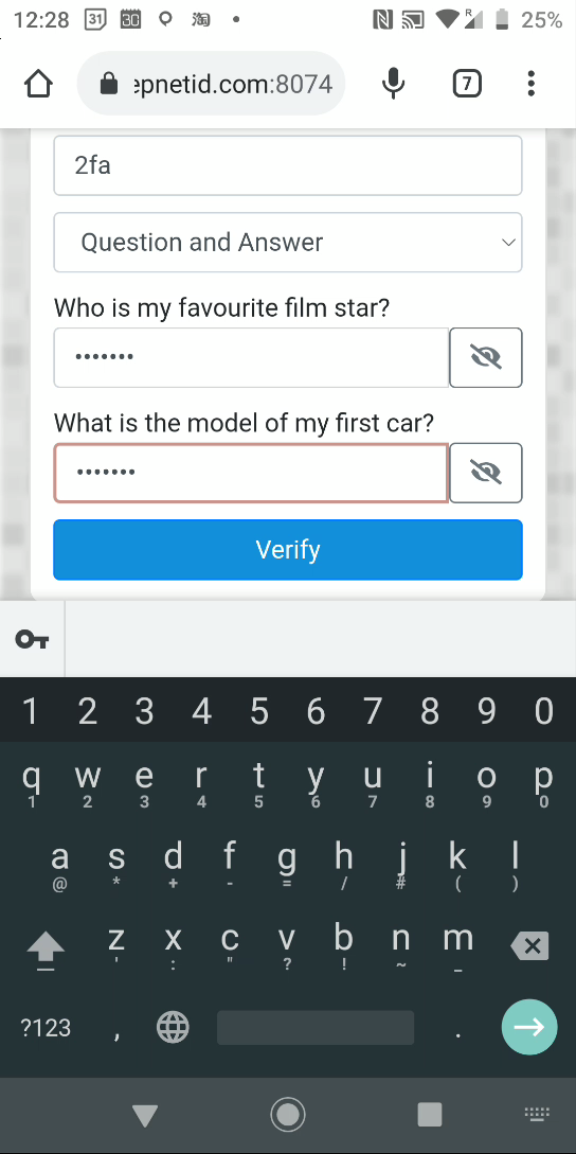
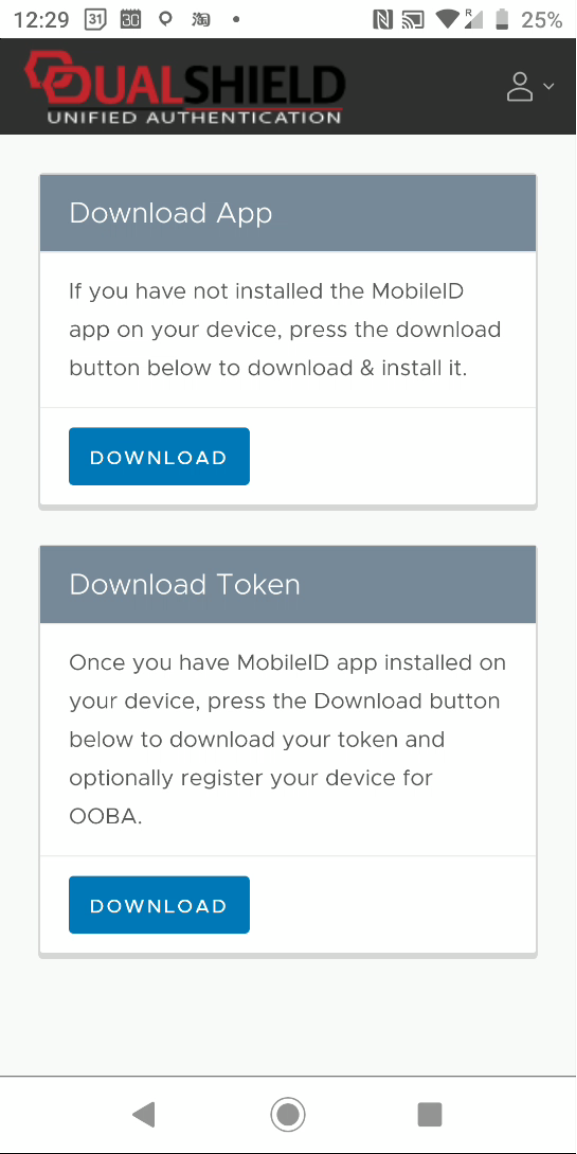
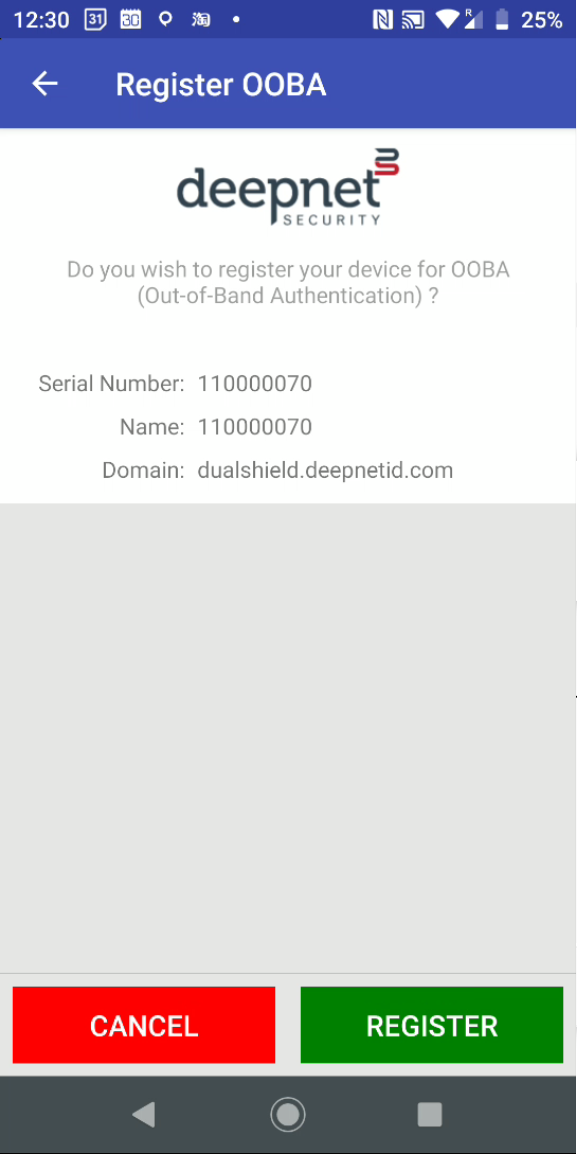
In the process of installing a token, you will be asked if they want to register the token for OOBA. You must press the "REGISTER" button

Related Articles
- No labels