DualShield includes several web consoles and portals, such as the DualShield Admin Console for the system administrators, and DualShield Service Console for the end users.
Those web consoles requires a SSL certificate. You may use a self-signed SSL certificate which will be provided by the DualShield installer itself during the installation process. However it is recommeded that you use a commercial certificate, particularly for the DualShield Service Console that is going to be accessed by end-users from the Internet.
Furthermore, if you are going to use the Out of Band Authentication (OOBA) from iOS and Android mobile devices, then you will have to make the DualShield Deployment Service and the Single Sign-On portals accessible by end users from the public network. In this case, you must not use a self-signed certificate because it will not be accepted by iOS and Android devices.
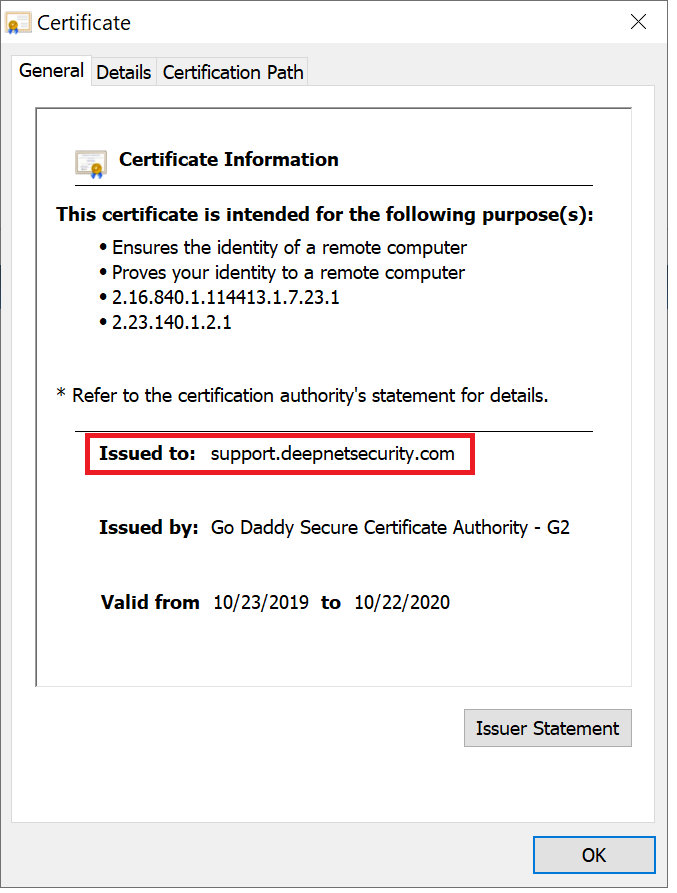
A web SSL certificate is issued to a specific FQDN (Fully Qualified Domain Name), e.g. "support.deepnetsecurity.com" in the certificate below:
Therefore, before you purchase a web SSL certificate from a commercial Certificate Providers such as GoDaddy, Comodo, DigiCert etc, you need to decide the FQDN for your DualShield server.
The certificate must be provided in the PFX format. There are various third-party tools that you can use to apply for and download an SSL certificate, or you can use the tool below: