If you have set up self-service console (see wiki; https://wiki.deepnetsecurity.com/display/DualShield6/Setting+up+the+Self+Service+Console ) an end user will be able to activate their own devicepass token
This Self-Service onboarding is particularly useful if you are using device fingerprinting to protect OWA, as the end-user will still need to gain access to their email in order to activate the token, therefore this gives we can give the end user a limited time period, to access their email where they will receive an activation link.
To facilitate this, the DualShield Deployment Service Console (DDS) will need to be set up. A DDS link will therefore be sent to the user so they will be able to activate the device token.
Please refer to the following wiki page to set up the DualShield Deployment Service
https://wiki.deepnetsecurity.com/display/DualShield6/DualShield+Deployment+Service+-+DDS
Sending out activation link
Activation codes are usually sent by email or SMS to the end-users, therefore the message gateway needs to be set up
Please refer to the following wiki page to set up message gateways
https://wiki.deepnetsecurity.com/display/DualShield6/Message+Gateways
DevicePass Policy
The DevicePass Policy can be set up exactly the same as outline in Policy for Device Onboarding by Admin Approval - DevicePass
The only difference is in the following sections
Device Activation Options
Set Device activation method to 'Send Activation Code to the user when created or asssigned'
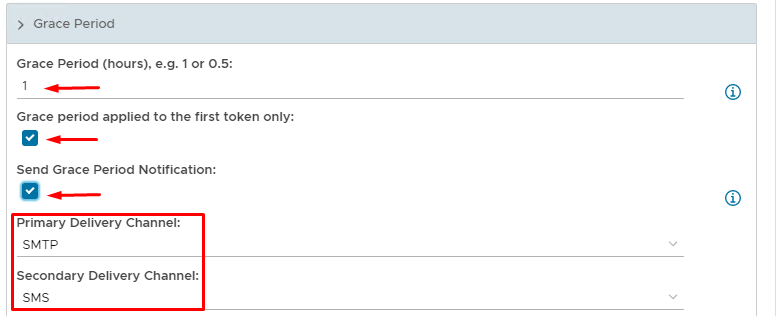
Grace Period Options
Set an appropriate time frame for the grace period
The Grace period applying to the first token only is optional
Sending a Grace Period Notification is also Optional but useful. Depending on what message gateways have been set up you can apply different delivery channels.