Both Azure MFA on-premises server and cloud service now support hardware tokens using time-based one time passcodes (OATH TOTP). Deepnet SafeKey/Classic is a USB key that supports both FIDO and OATH OTP. It can be configured to generate time-based OTP, and used with Azure MFA.
First, administrators need to seed SafePass USB keys with TOTP tokens, then upload the token seeds onto the Azure MFA server. As the SafePass USB key does not have the display function, user will use the SafePass application to display OTP generated by the SafePass USB key.
Install the OTP Programmer Tool
To program the SafeKey/Classic security keys as an OTP token, you need to use the SafeKey/Classic OTP Programming Tool.
Click the link below to download the tool
SafeKey/Classic OTP Programming Tool
Unzip it into a folder on your local hard drive.
Create a TOTP Token
To create a TOTP token in a SafeKey/Classic device, follow the steps below (these instructions only apply to the NFC variants of the SafeKey/classic devices - the USB-A variant only supports the HOTP algorithm).
1. Insert a SafeKey/Classic USB key into your PC
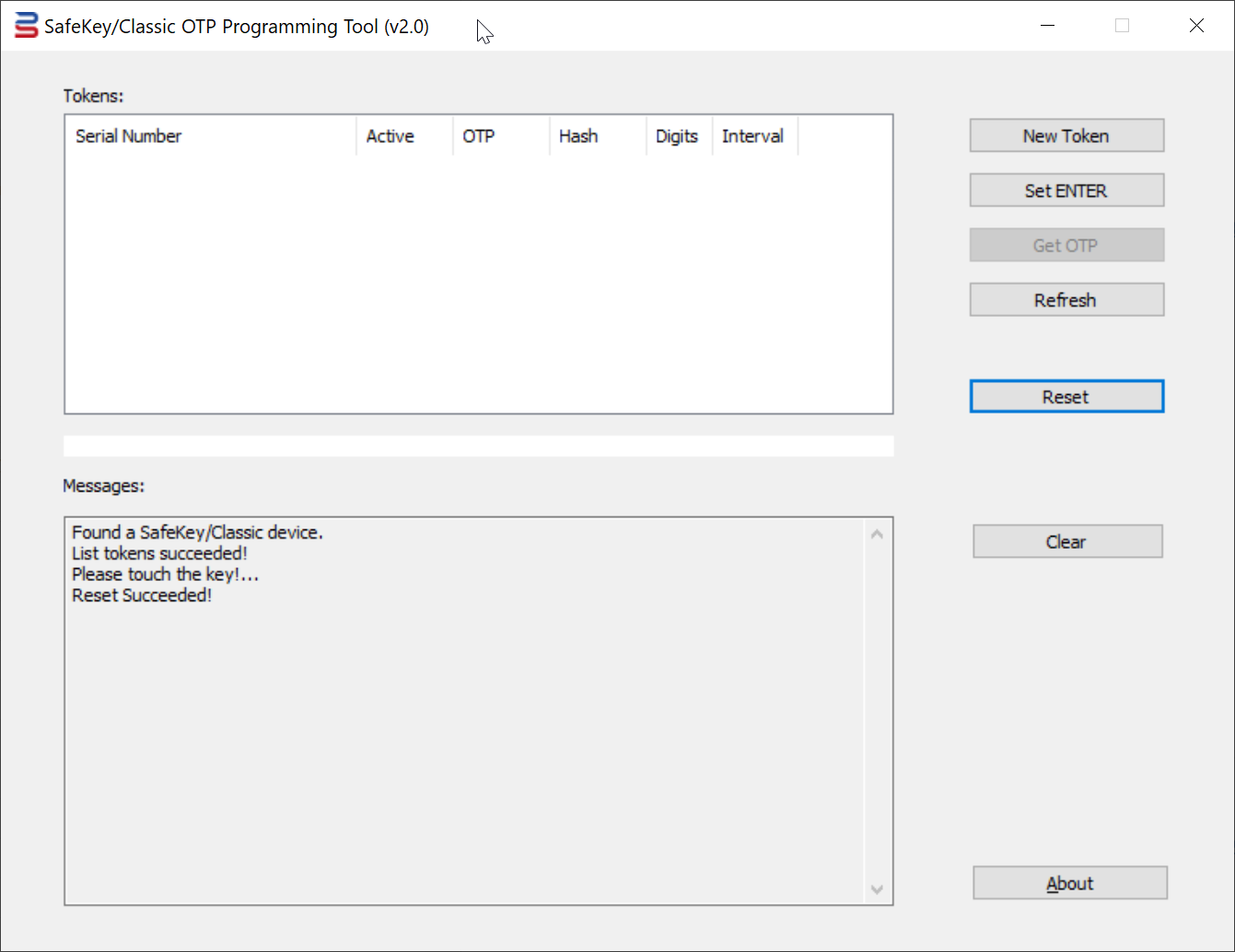
2. Run the SafeKey/Classic Programming Tool as Administrator
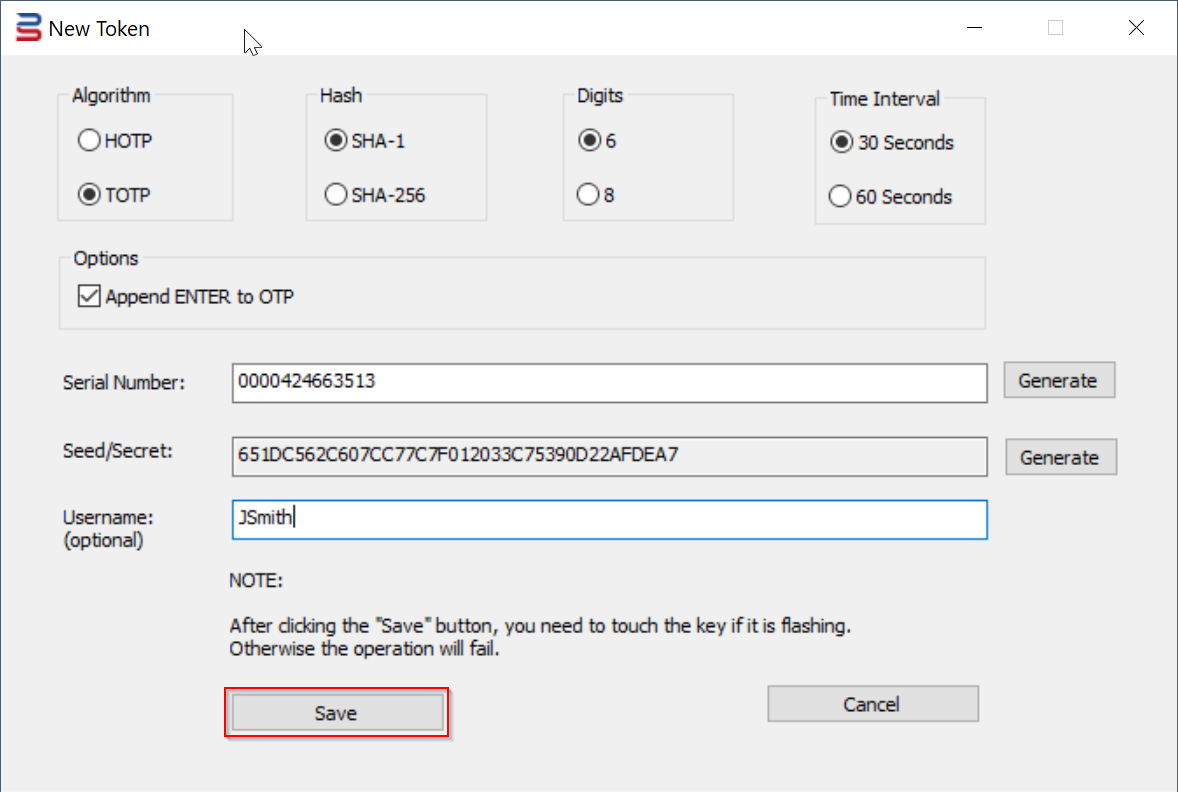
3. Press the "New Token" button
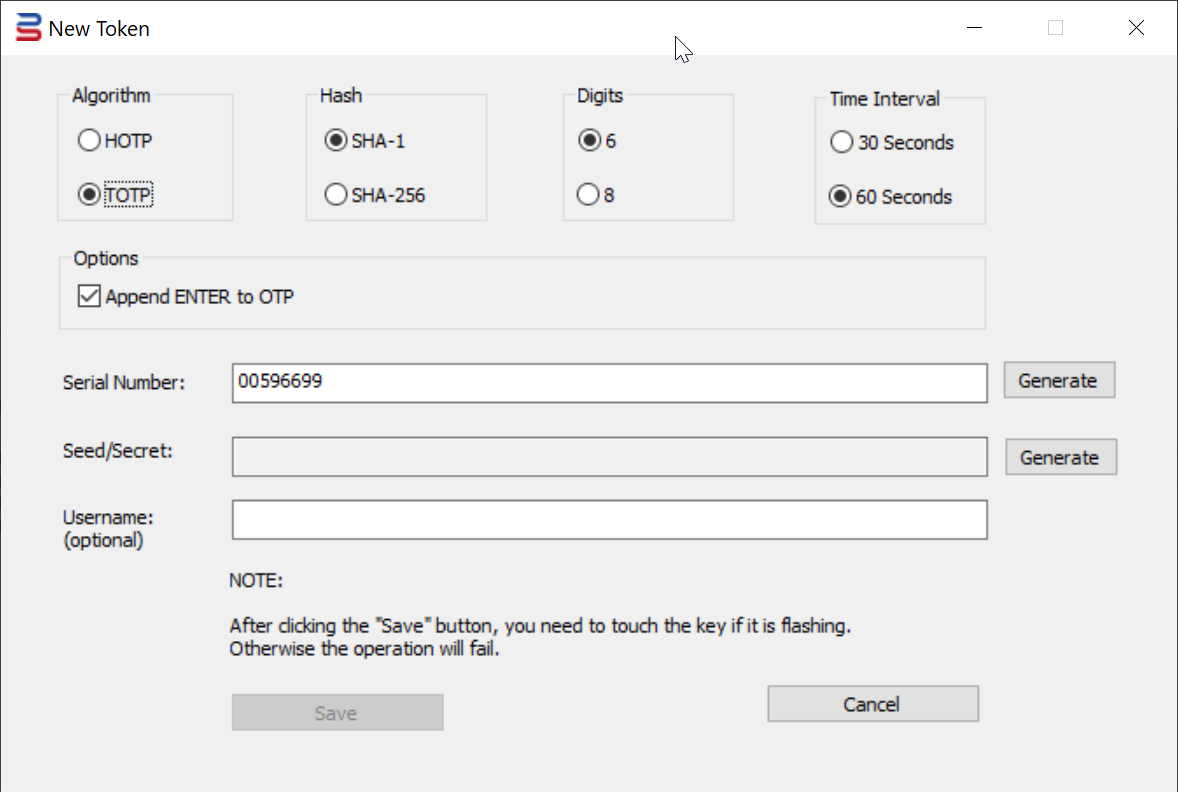
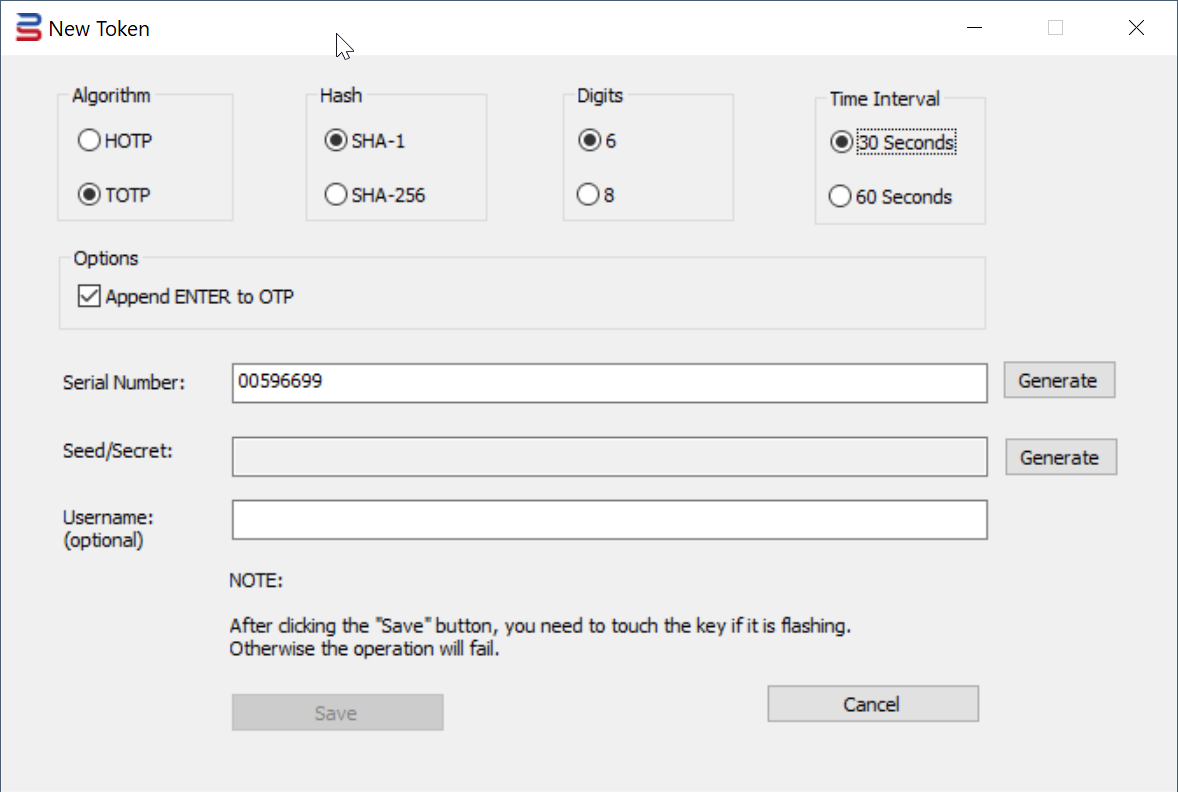
The "New Token" dialog box will pop up
4. Select the option "Algorithm", e.g. "TOTP"
5. Select the option "Hash", e.g. "SHA-1"
6. Select the option "Digits", e.g. select "6"
7. Select the option "Time Interval", e.g. "30 seconds"
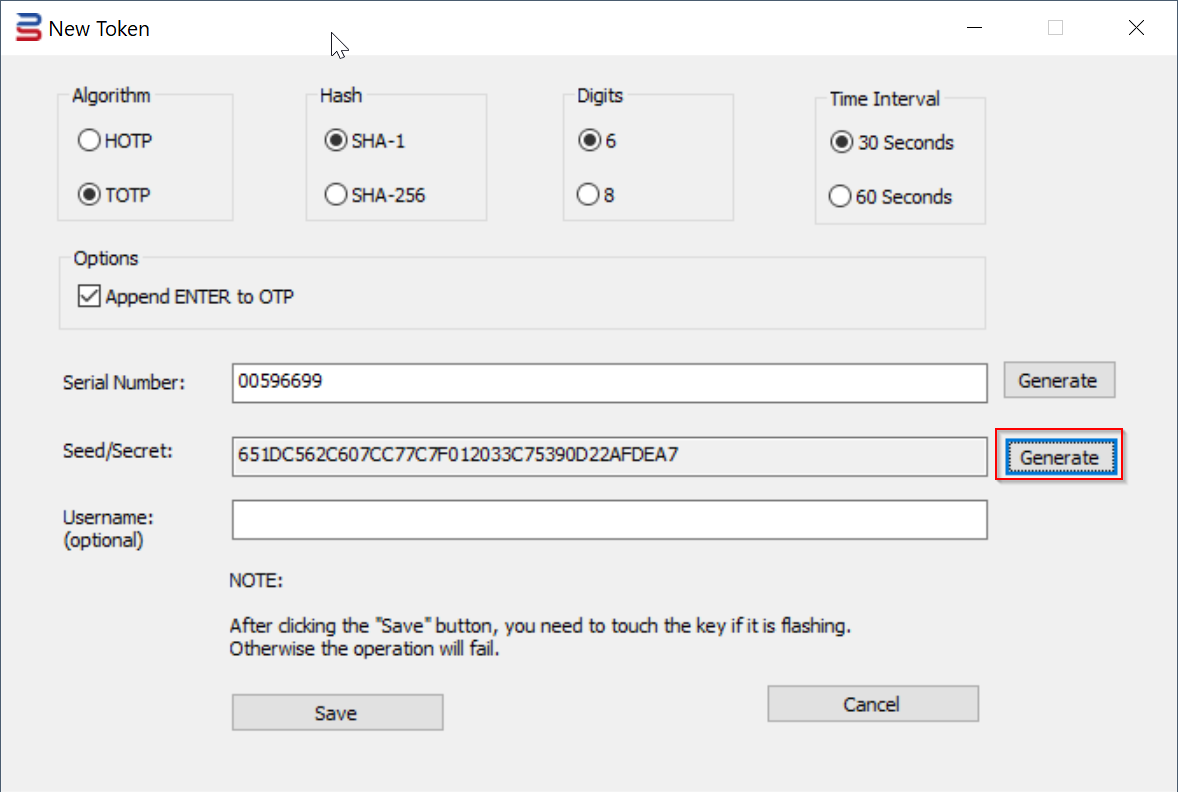
9. Press the "Generate" button to generate a random Seed/Secret data
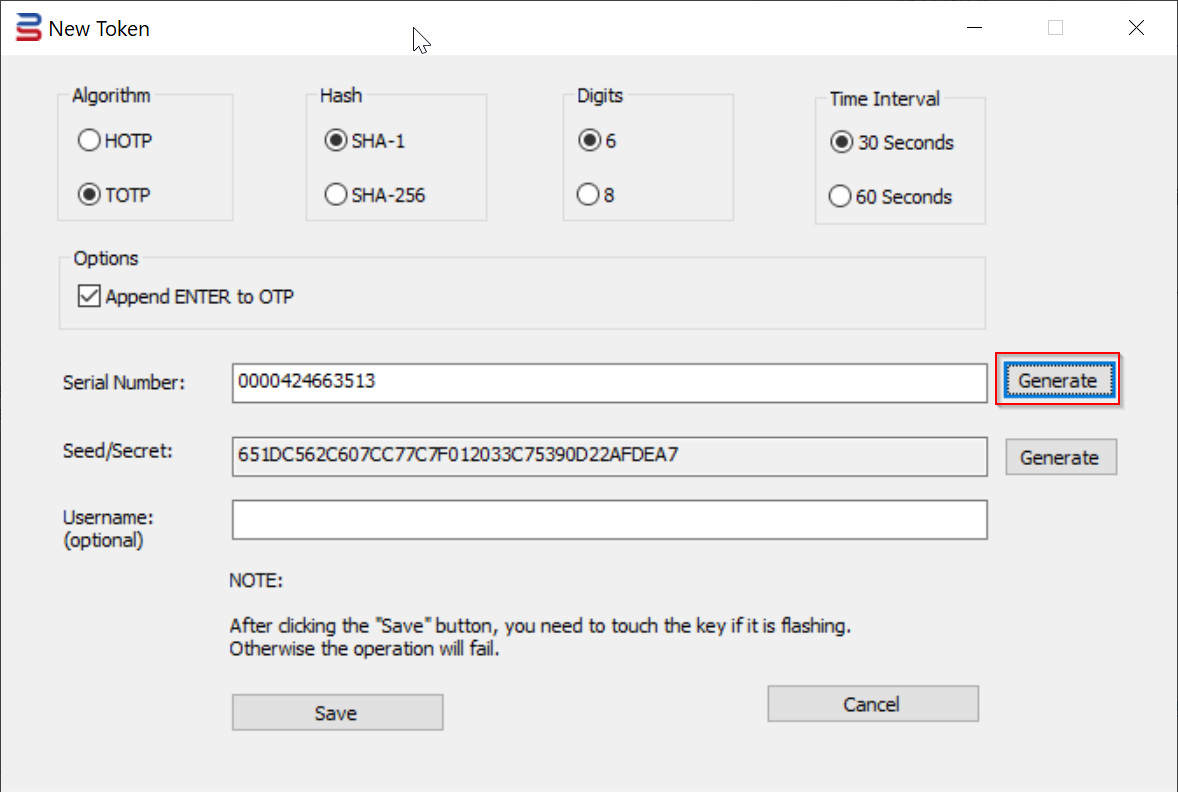
Optionally, you can also generate a random Serial Number, or you can enter your own Serial Number
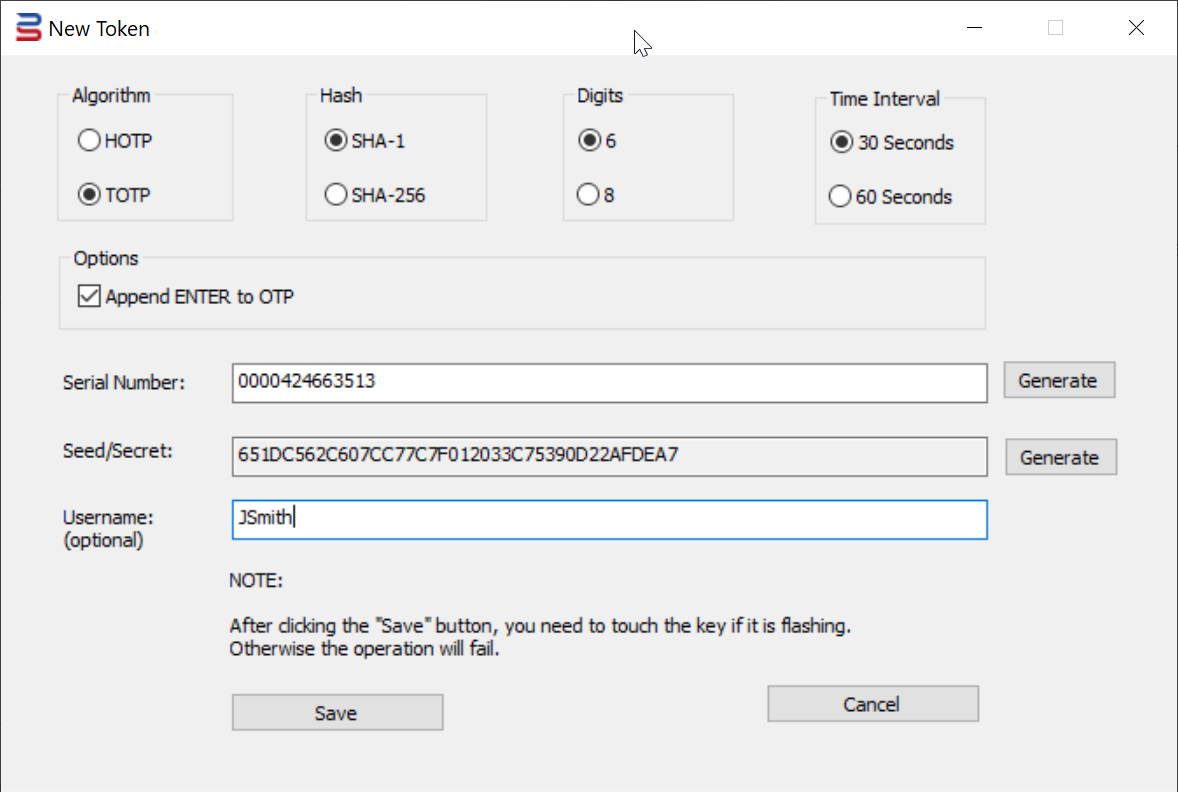
10. If you're programming the key for an O365 user, then you might want to enter the user's UPN in the Username box
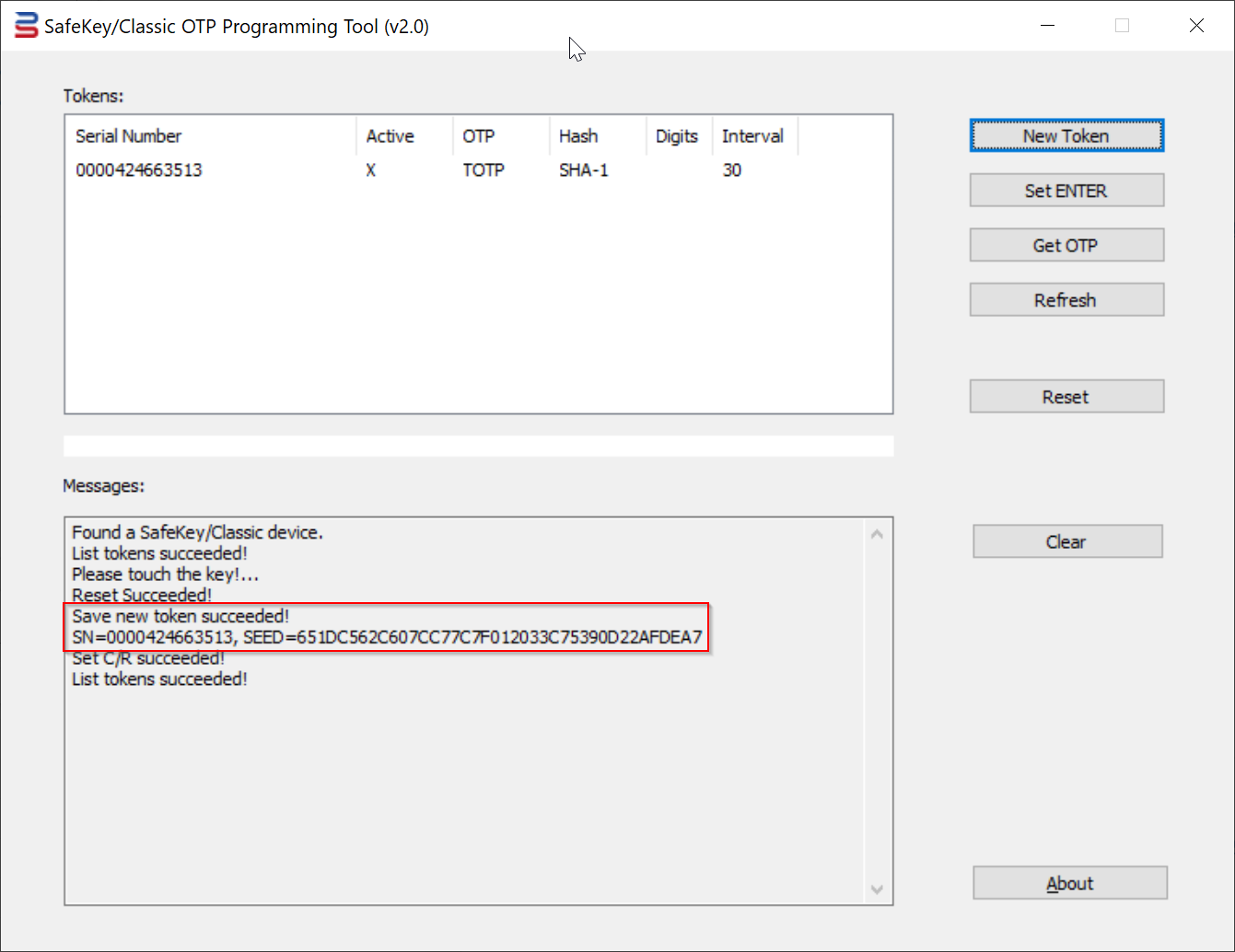
11. Finally, press the "Save" button to save the token into the USB key.
You will see the key flashing. You must touch the key to complete the operation
To continue programming more SafeKey devices, insert a new key and repeat the Step 9 to 11.
Once all keys have been programmed, close the Tool.
Token Seed Files
The SafeKey programming tool generates the following files
| File Name | Comment |
|---|---|
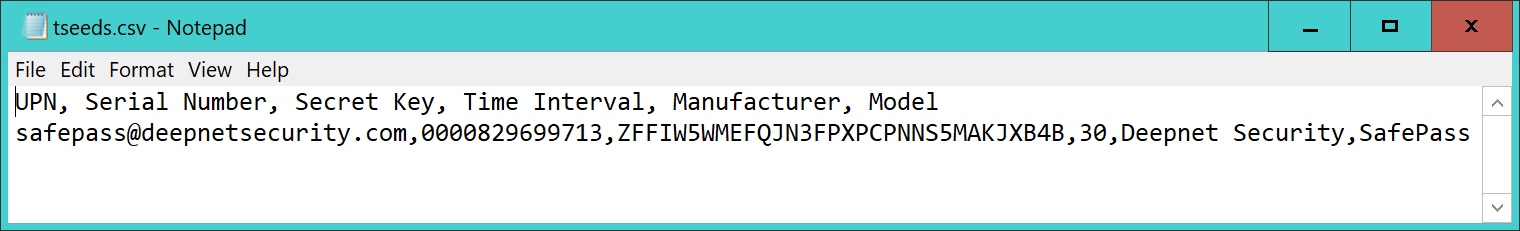
| tseeds.csv | This CSV is for TOTP tokens. It is in the format for Azure MFA. Token secret is encoded in BASE64 |
| tseeds.xml | This XML is for TOTP tokens. It is in the format for DualShield MFA |
| hseeds.csv | This CSV is for HOTP tokens. It is in the format for general purposes. Token secret is encoded in HEX |
| hseeds.xml | This XML is for HOTP tokens. It is in the format for DualShield MFA |
Upload Seed File to Azure MFA
In the Admin Tool folder, you will see a file named "tseed.csv"
This is the seed file in the format required by the Azure MFA cloud service.
This file can be directly uploaded onto the Azure MFA cloud service.
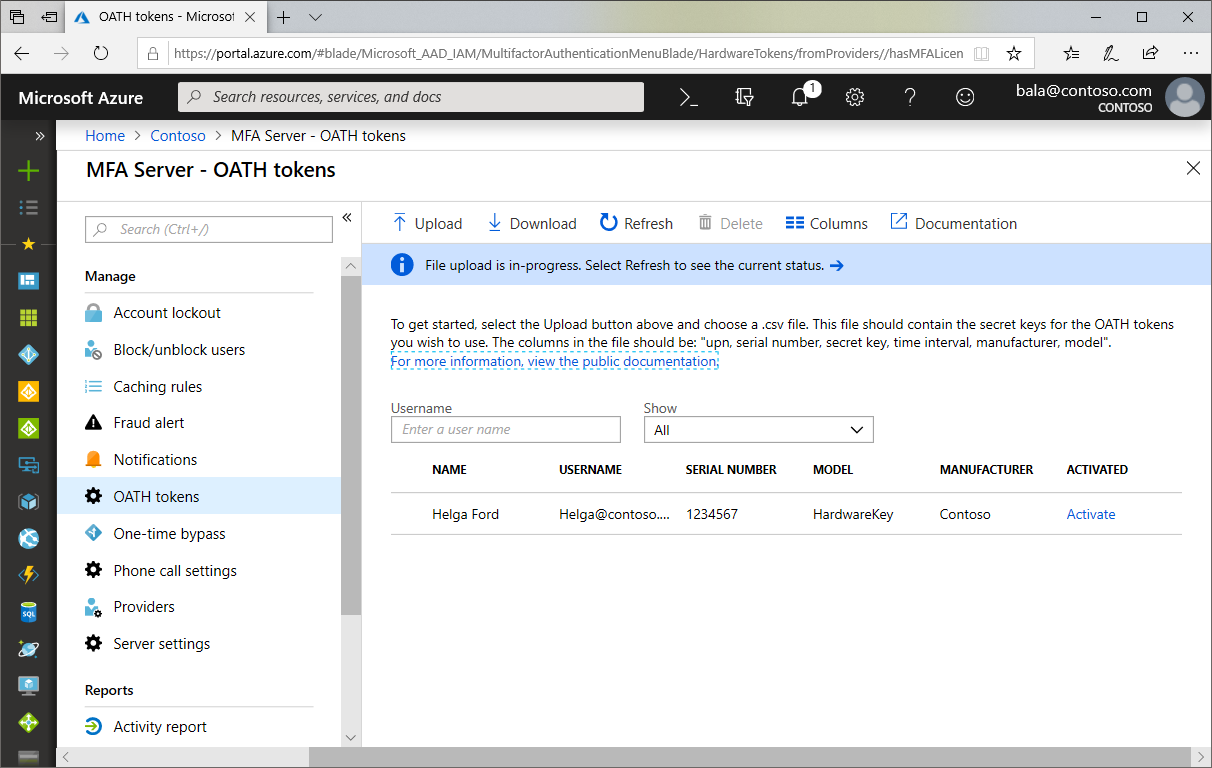
Now, sign in to the Azure portal and navigate to Azure Active Directory, MFA Server, OATH tokens
Select "Upload" to upload the CSV file.
Depending on the size of the CSV file, it may take a few minutes to process. Click the Refresh button to get the current status. If there are any errors in the file, you will have the option to download a CSV file listing any errors for you to resolve.
Once any errors have been addressed, the administrator then can activate each key by clicking Activate for the token to be activated and entering the OTP displayed on the token.
Generating OTP
To generate OTPs, the user will need to run the SafeKey OTP Authenticator application.
Install the OTP Authenticator App
SafeKey/Classic OTP authenticator app is a desktop application that works with SafeKey/Classic USB keys to generate TOTP codes.
Download the SafeKey TOTP app from the links below:
SafeKey OTP Authenticator for Windows
SafeKey OTP Authenticator for MacOS
Install it on your Windows PC or Mac.
Display an OTP Code
To generate an OTP code, follow the steps below.
Firstly, insert the SafeKey device into a USB port in your computer
Then, run the SafeID OTP Authenticator application as an administrator.
Your SafeKey device should now be flashing now...
Touch the SafeKey, then an OTP code will be displayed: