Many organizations have blocked the Microsoft Outlook App for iOS and Android, for some security concerns. Following are 2 main concerns
1 - Your user credentials and email data are sent to and stored in the Microsoft cloud server
Outlook App for iOS and Android does not connect directly to your corporate Exchange server. Instead, it connects to a server or service hosted in the cloud by Microsoft. When you configure an account in Outlook App on iOS and Android, the app connects to the Microsoft cloud service and the cloud service connects to your mailbox on your on-premises Exchange server, on your behalf using your user credential. The cloud service will store your user credential and cache your email data. Effectively, the Microsoft cloud service acts as a middle man.
Not only that you might not trust Microsoft to securely store and safeguard your data including your credentials, but also, providing your user credentials to a third party is a breach of many IT usage policies. The Outlook app doesn’t even make clear to end users that this is occurring. In fact, the typical end user would have no idea that this is happening.
2 - Outlook app does not always provide a unique device ID
If a user runs the Outlook App on multiple devices of the same OS, then Outlook App will provide the same device ID for the user on those devices. This will weaken the enforcement of MFA that is based on the device ID.
3 - Outlook app can change the device ID sporadically on the same device
Occasionally, the Outlook app may change the device ID of the same device. As a result, applications that use the device ID will stop working.
For organizations that have a problem with any of the concerns above, you can block the Outlook App from accessing your Exchange mailboxes. Microsoft provides a guide below:
We recommend a more direct and effective way below:
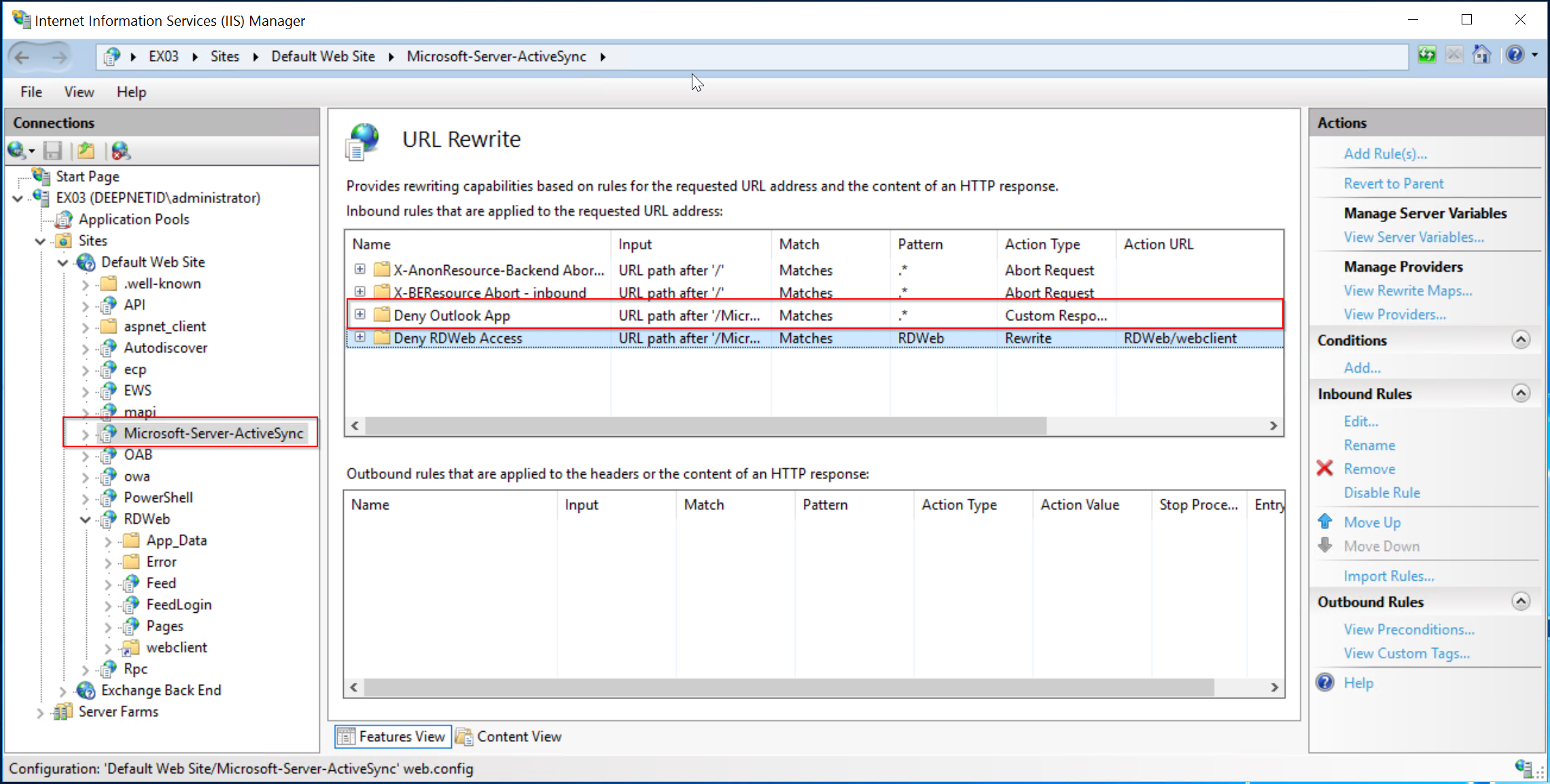
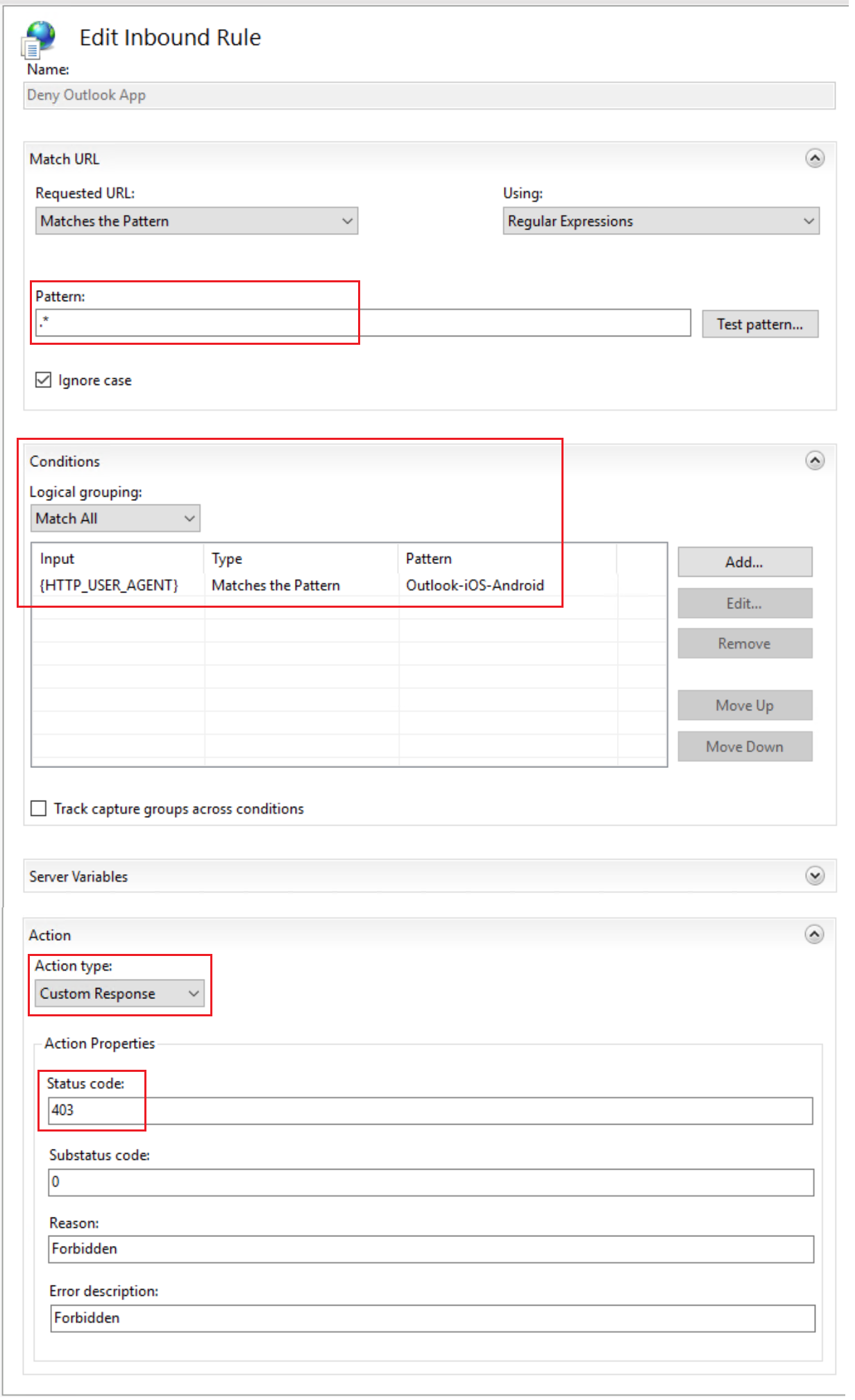
On your Exchange servers, add a URL Rewrite rule as follows