To set up Passwordless Authentication in Computer Logon using Certificate, follow the steps below
Install AD Certificate Service
To implement passwordless authentication using certificates, you will need the Active Directory Certificate Service.
Install Active Directory Certificate Service in the Domain Controller.
After installation, configure the Certificate Authority accordingly.
Create a CA Certificate in DualShield
Create or import a CA certificate in the DualShield Certificate Authorities, and bind to the target domain, ie. deepnetpb.com
Import CA Certificate into Domain Controller
Export this CA certificate, and then import it into the Trusted Root Certification Authorities on the Domain Controller
Configure Enterprise PKI
Now, open the Microsoft Management Console (MMC) and add the 'Enterprise PKI' snap-in.
Launch the Enterprise PKI snap-in console and right-click on EnterprisePKI and select Manage AD Containers...
Add the new CA that was created.
Click Ok and then click on the CA entry that appears under Enterprise PKI...
If you see all of the following 4 certificates and their status is OK, then your domain is ready for DualShield Computer Logon Passwordless Authentication.
- CA Certificate
- AIA Location #1
- CDP Location
- DeltaCRL Location #1
Configure Policy Options in DualShield
In the admin console, navigate to the Computer Logon Client Policy and make the following changes:
- Enable the option "Enable Passwordless Login".
- Set the "Passwordless Certificate Lifetime".
- Set the option "Renew Passwordless Certificate N days before it expires"
- Leave the option "Certificate Revocation List (CRL) URL" empty.
Note: if you have implemented the Device Certificate authentication method, then you must follow the instructions below to set up a new Certificate Revocation List (CRL) URL
User Experience
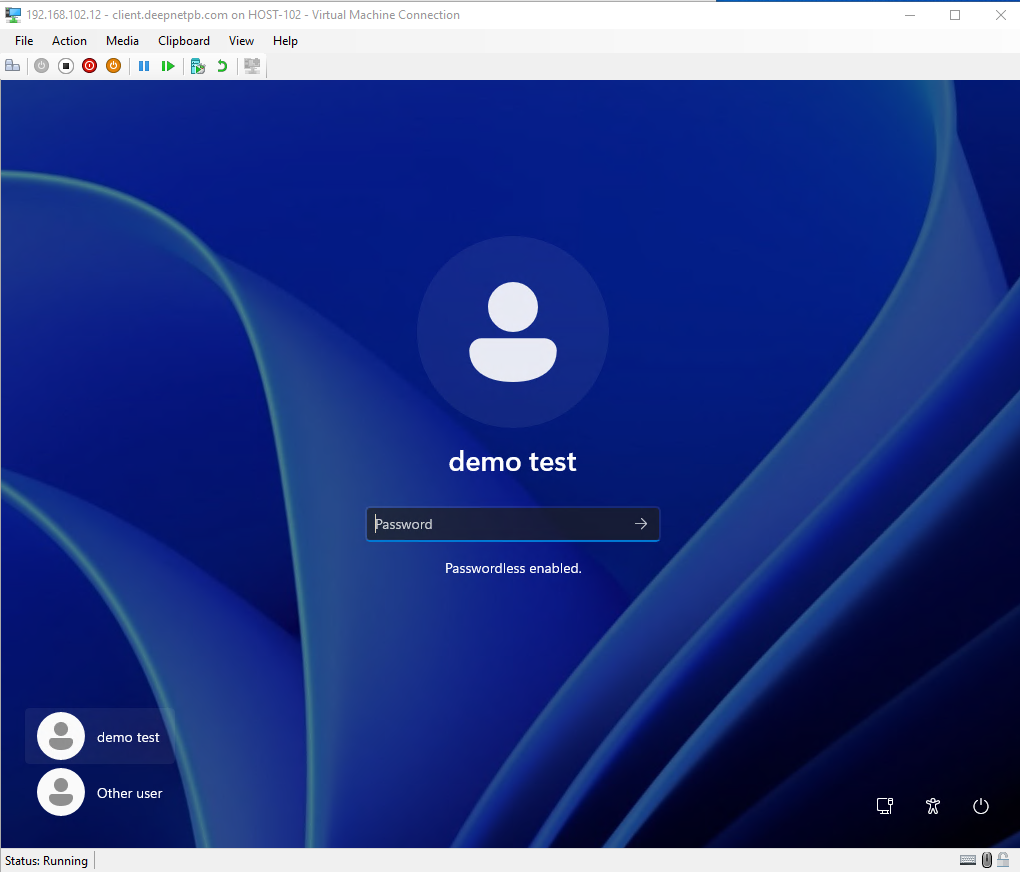
With the password authentication enabled, users will see the hint 'Passwordless enabled" under the password entry box on the login screen.
Do not enter anything in the password box
Click the continue button to continue
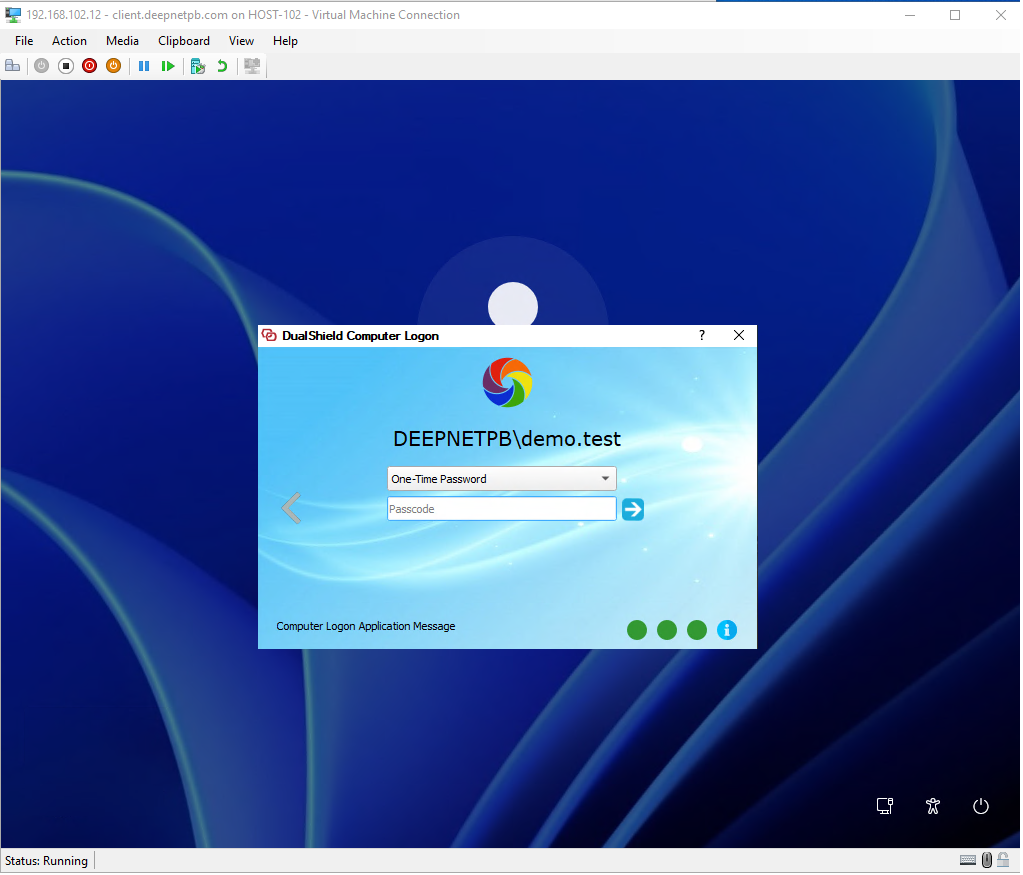
The 2FA/MFA window will be prompted: