In the initial stage of deploying MFA across your entire domain and user base, you might not want to enforce MFA on all user accounts on day one. Instead, you might consider enforcing MFA gradually across your user base, in stages. To do so, you need to create a special user group in AD and a couple of logon policies in DualShield. For the simplicity of this guide, let's call this AD group as DualShield MFA group.
The strategy is that MFA will only be enforced on users who are a member of the DualShield MFA group. All other domain users will be able to continue to login into the domain with password only.
The first step is to create the DualShield MFA group in your AD server.
Then, create 2 logon policies in your DualShield server. A domain policy and a group policy.
The domain policy is bound to the entire domain, and multi-factor authentication is not required on all users.
The group policy is bound to the DualShield MFA user group, and multi-factor authentication is required on all users.
Below is an example.
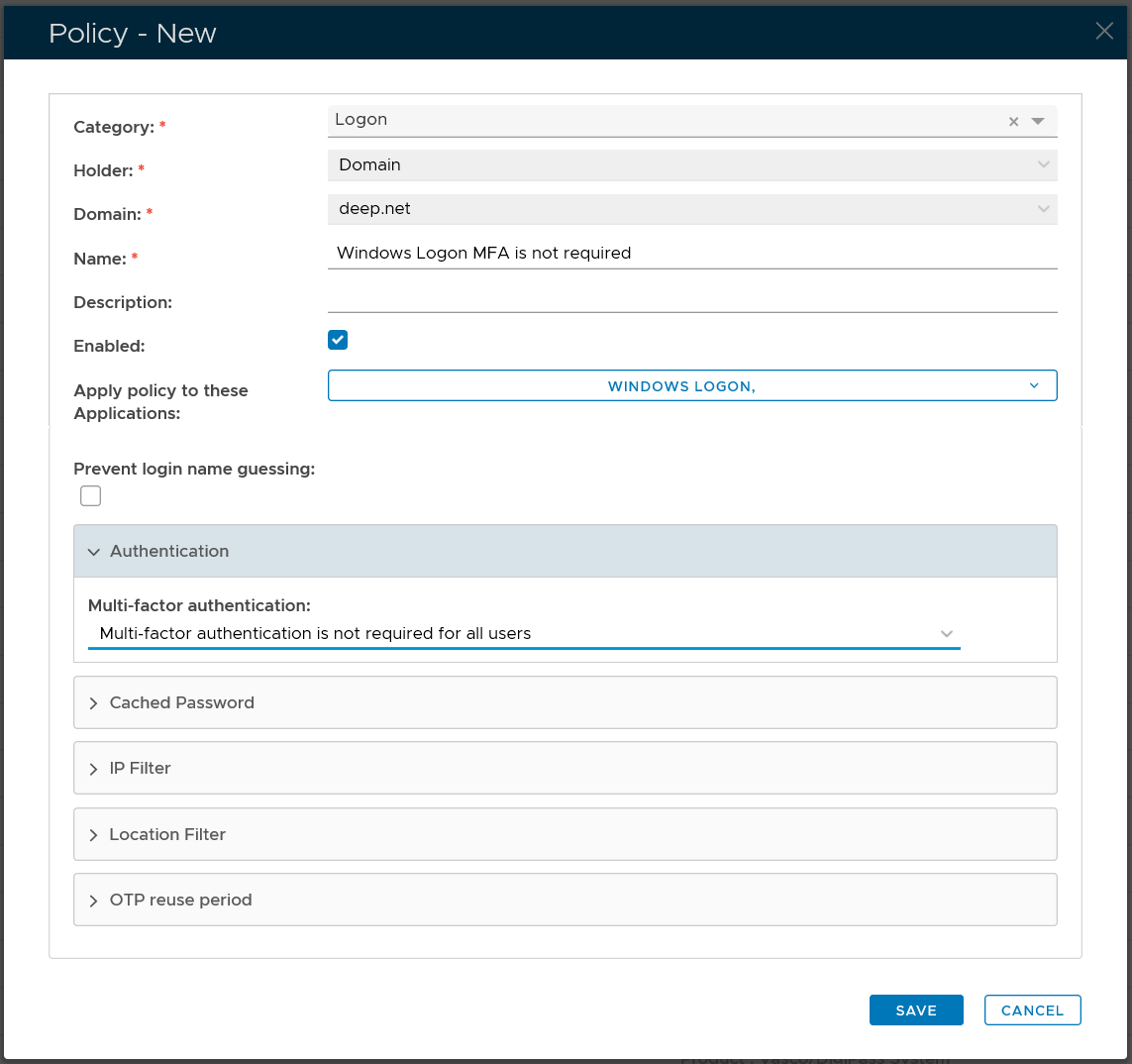
Domain Logon Policy
| Option | Value |
|---|---|
| Category: | Logon |
| Holder: | Domain |
| Domain: | Select your AD domain |
| Name: | Describe the purpose of this policy |
| Apply policy to these applications: | Select the application that this policy will be applied to |
| Authentication: | Select "Multi-factor authentication is not required for all users" |
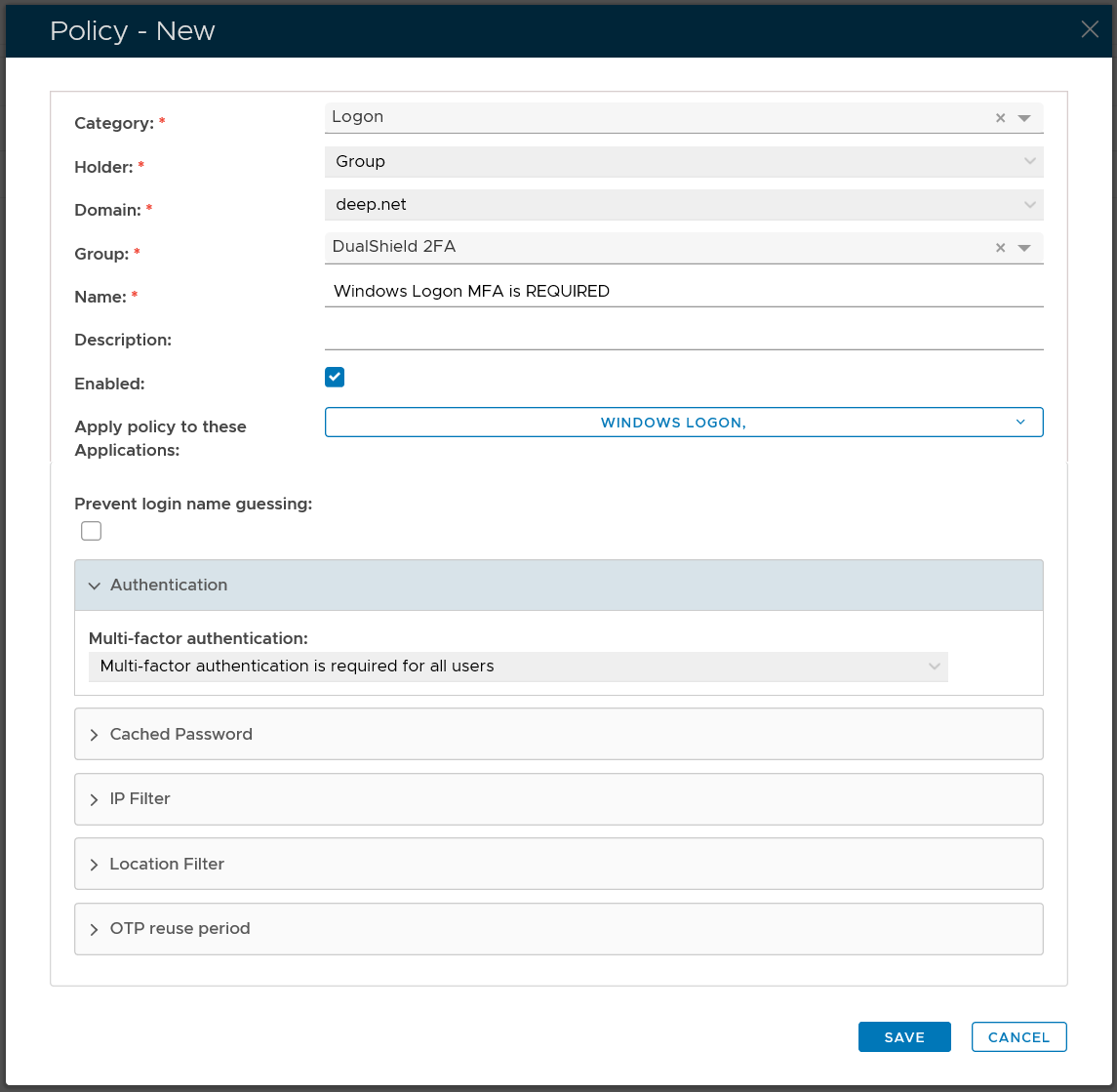
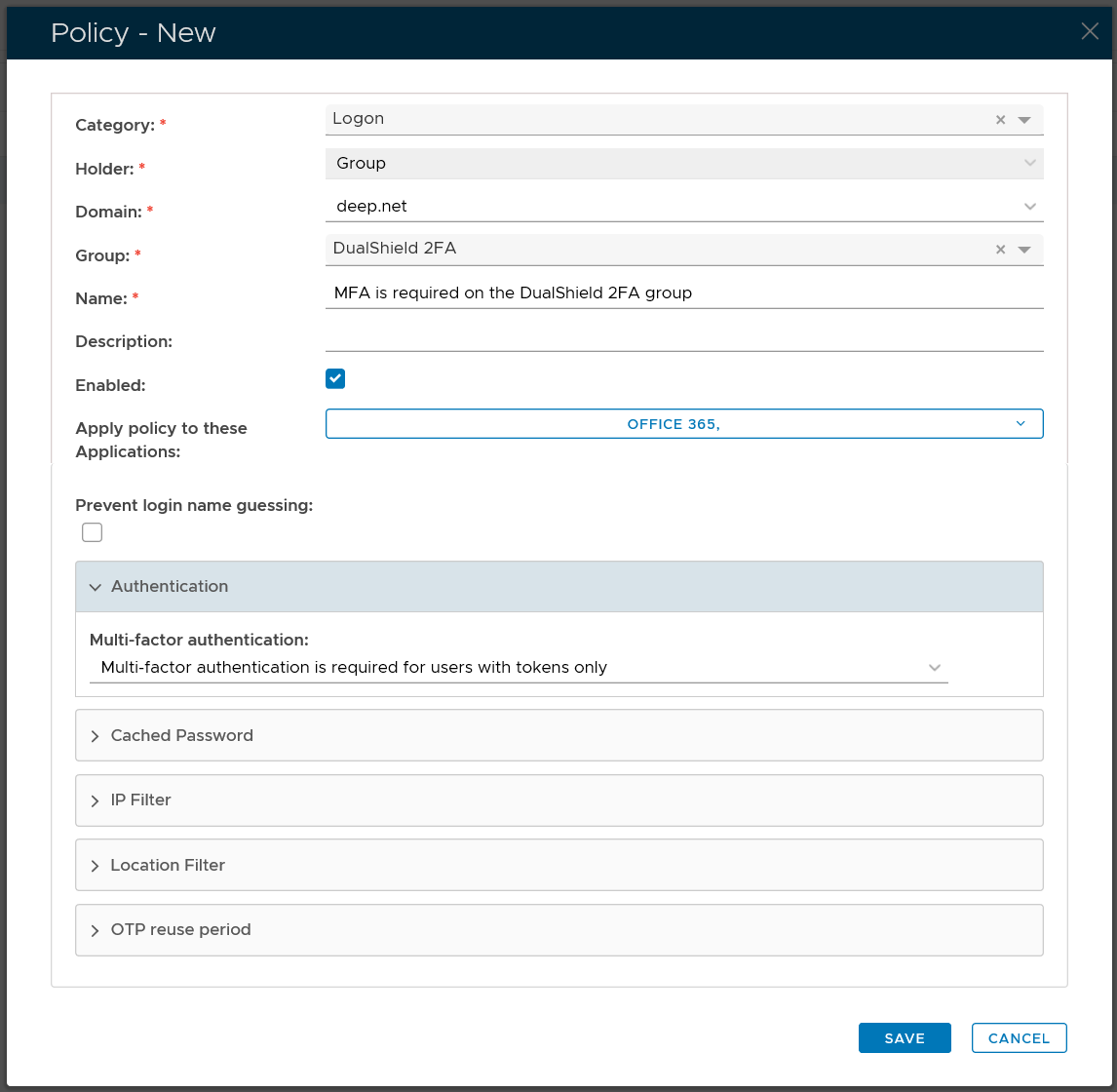
Group Logon Policy
| Option | Value |
|---|---|
| Category: | Logon |
| Holder: | Group |
| Domain: | Select your AD domain |
| Group | Select the DualShield MFA group |
| Name: | Describe the purpose of this policy |
| Apply policy to these applications: | Select the application that this policy will be applied to |
| Authentication: | Select "Multi-factor authentication is required for all users" |
For the general guide of creating a logon policy, expand the link below