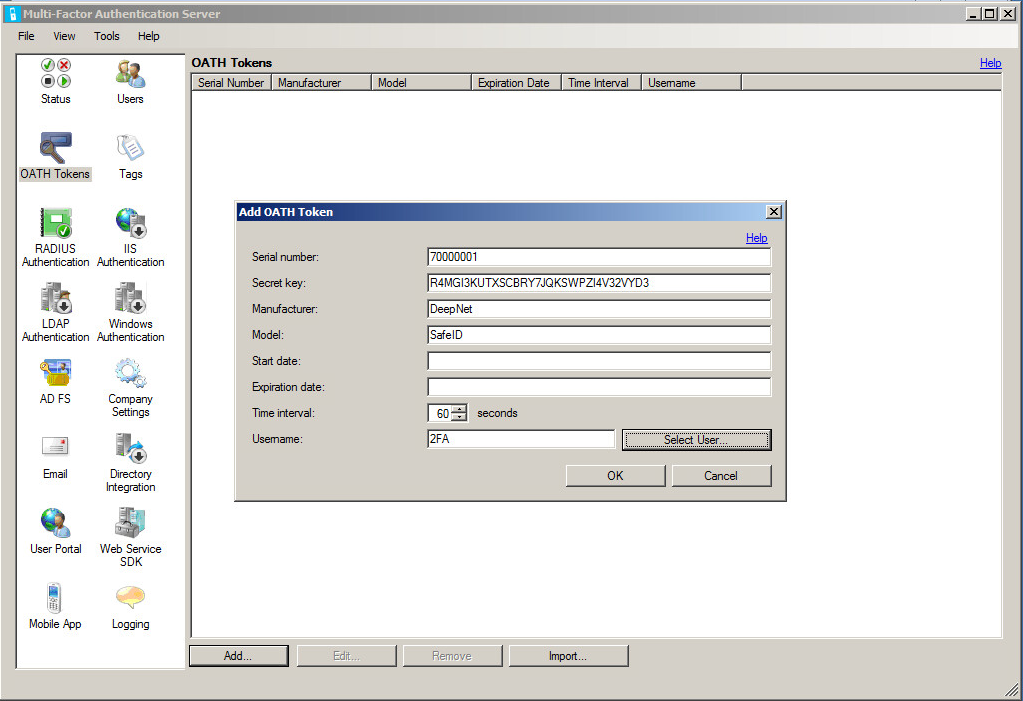
Follow the steps below to set up SafeID token in Azure MFA Cloud Service
Prepare Token Upload File
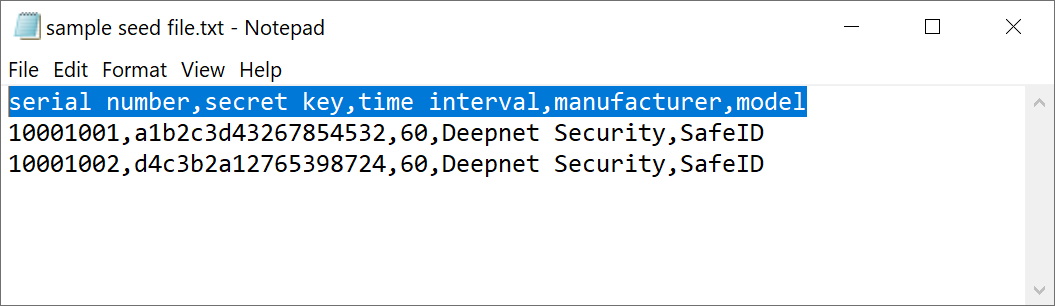
Hardware tokens must be uploaded to Azure MFA service in a comma-separated values (CSV) file. Deepnet SafeID or MobileID tokens are supplied with a CSV file that includes serial number, secret key, time interval, manufacturer, and model as the example below shows.
serial number,secret key,time interval,manufacturer,model
10001001,a1b2c3d43267854532,60,Deepnet Security,SafeID
10001002,d4c3b2a12765398724,60,Deepnet Security,SafeID
*Please note that the above seed file is only an example. If you have not received the seed file of your tokens, please contact your reseller or Deepnet Security.
Azure MFA requires one extra information to be added into the CSV file: the user principal name (UPN) of each token. Therefore, you MUST edit the CSV file in the text editor and add an UPN to each of the tokens, as the example below shows.
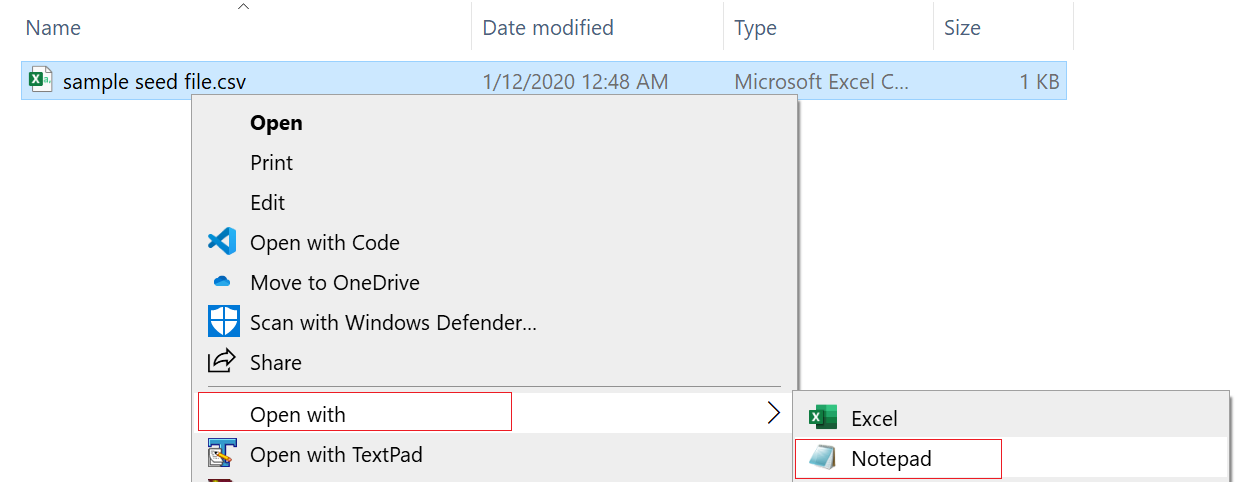
Add 'upn' to the header row, so that the header reads:
upn,serial number,secret key,timeinterval,manufacturer,model
then, add users' UPNs in every row, e.g.
user001@contoso.com,1234567,1234567890abcdef,60,Deepnet Security,SafeID
The revised content looks like below:
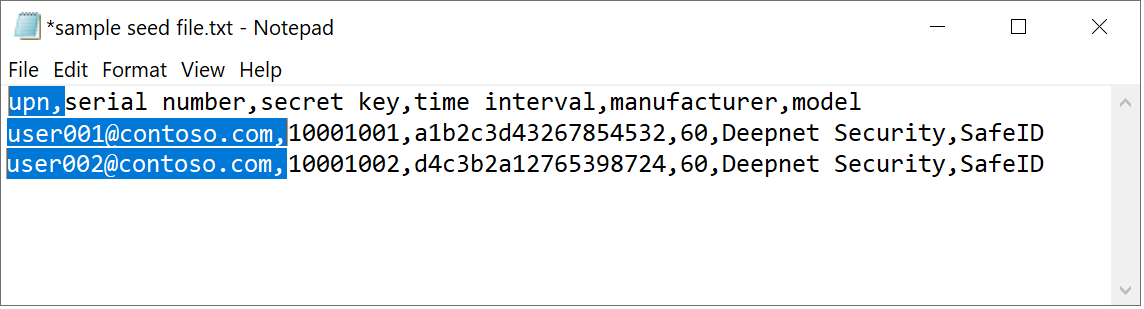
Save the file on completion.
Upload Tokens
Now, sign in to the Azure portal and navigate to Azure Active Directory, then to Security and to MFA.
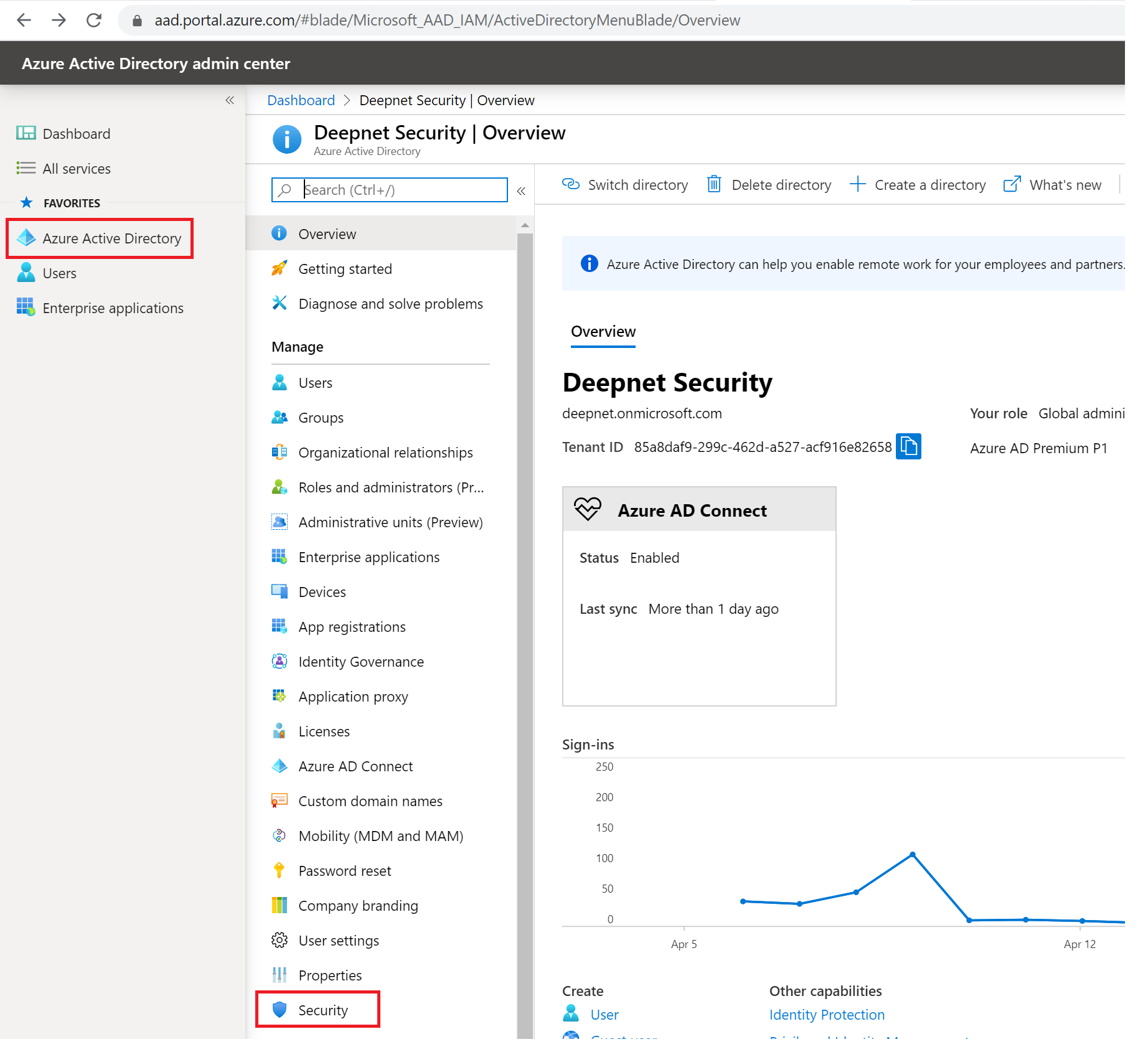
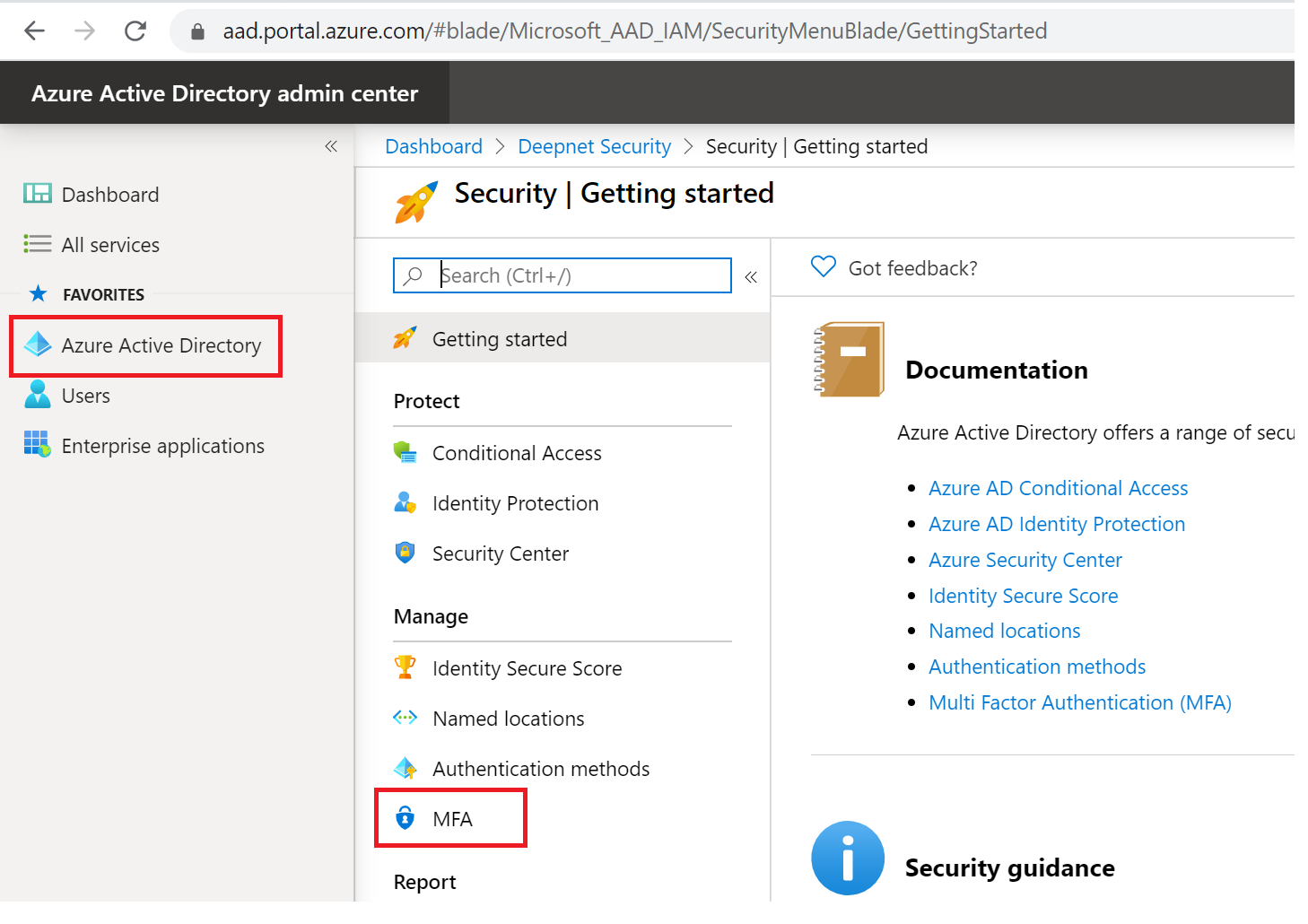
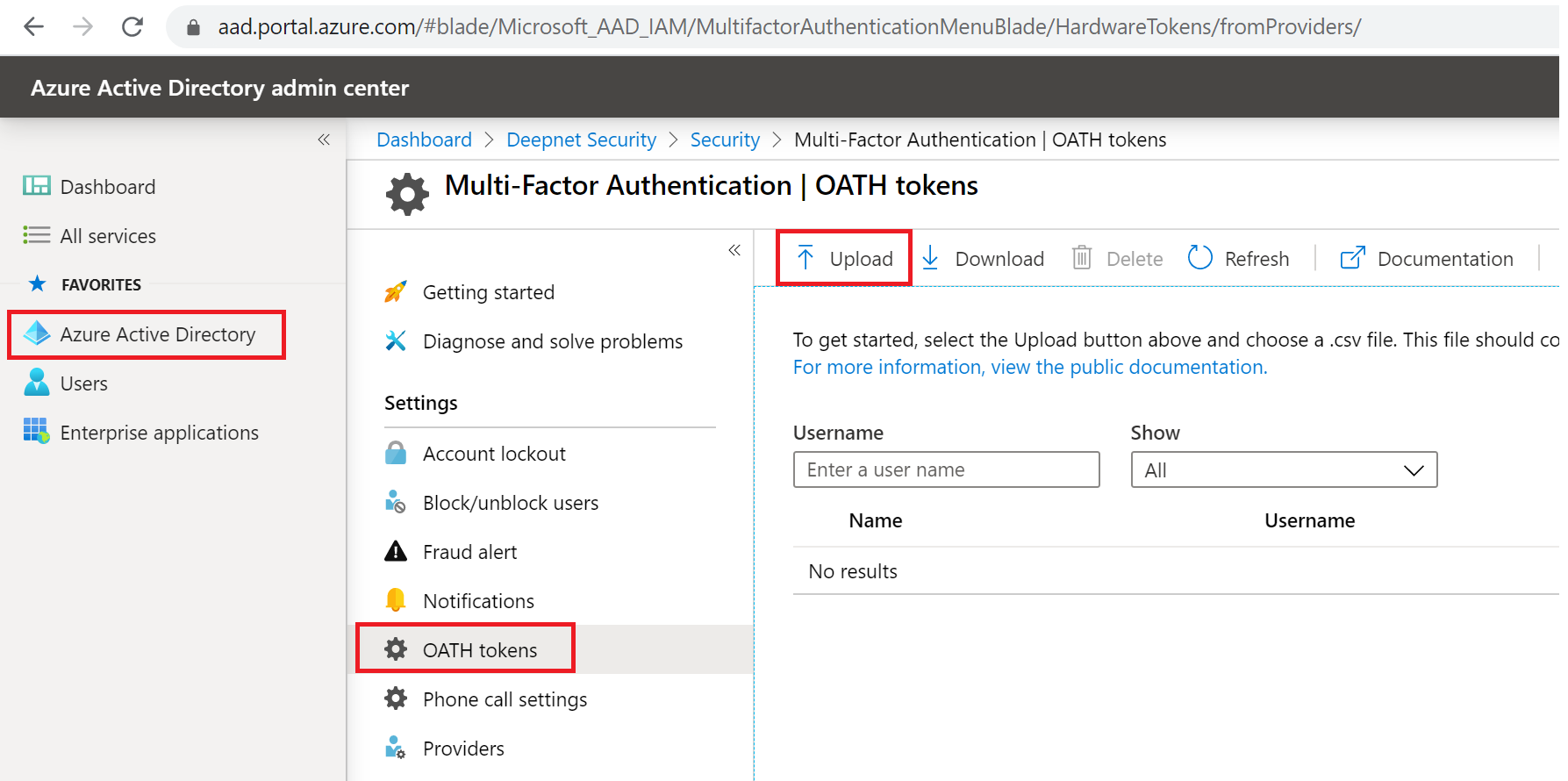
Select OATH tokens and click the “Upload” button.
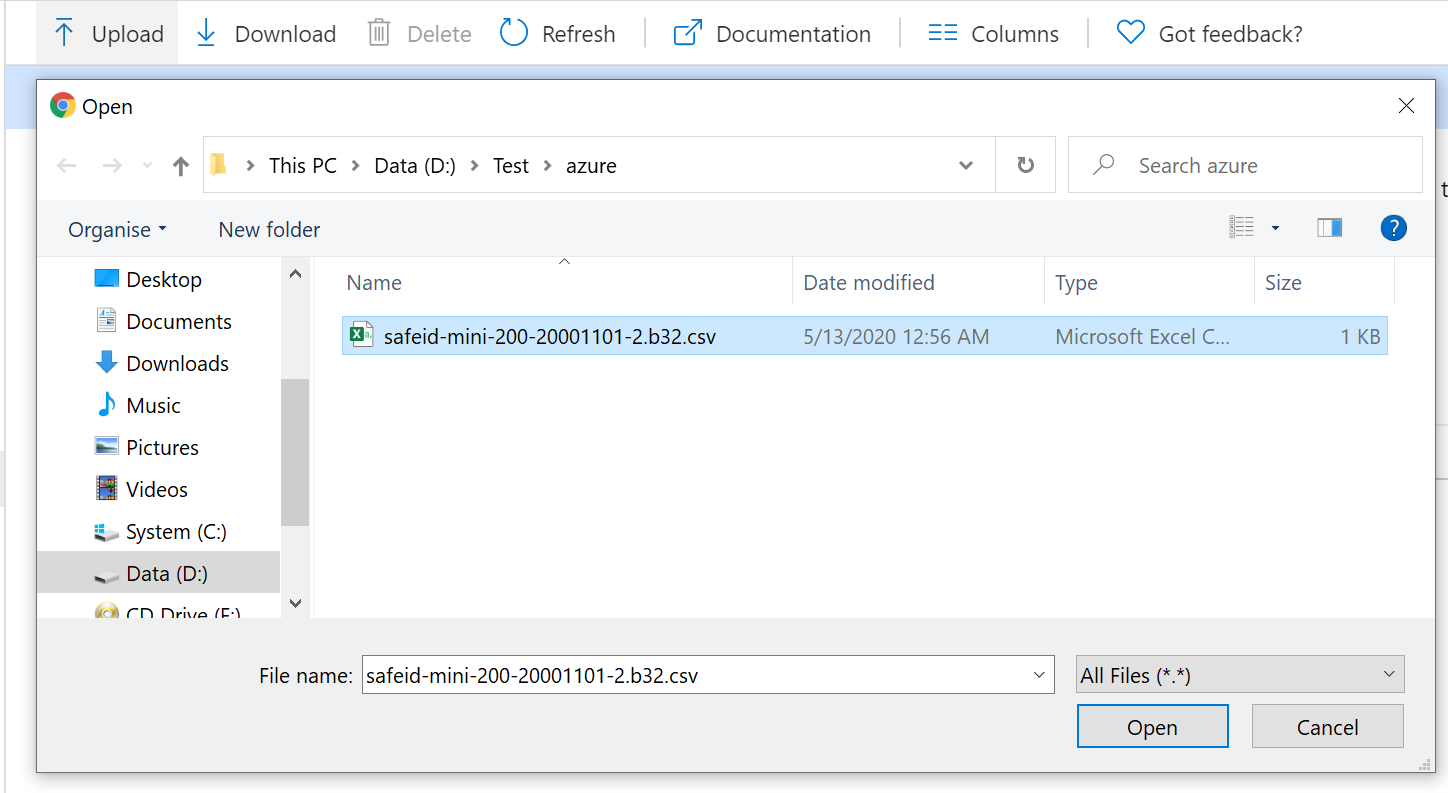
Select the CSV file to be uploaded, then click the Open button.
Depending on the size of the CSV file, it may take a few minutes to process.
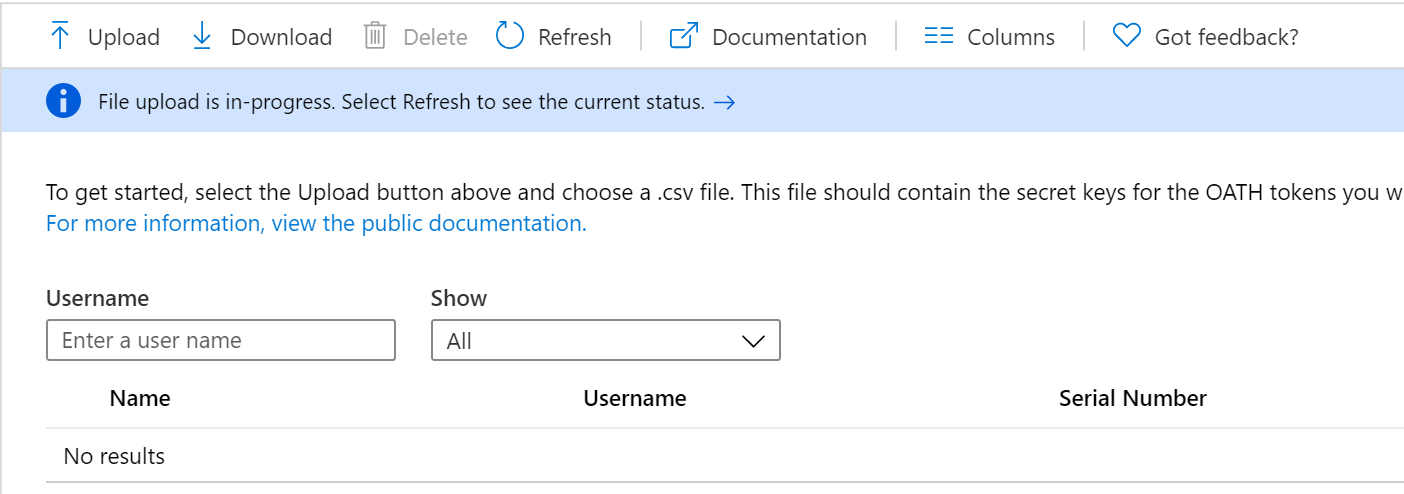
Click the Refresh button to get the current status. If there are any errors in the file, you will have the option to download a CSV file listing any errors for you to resolve.
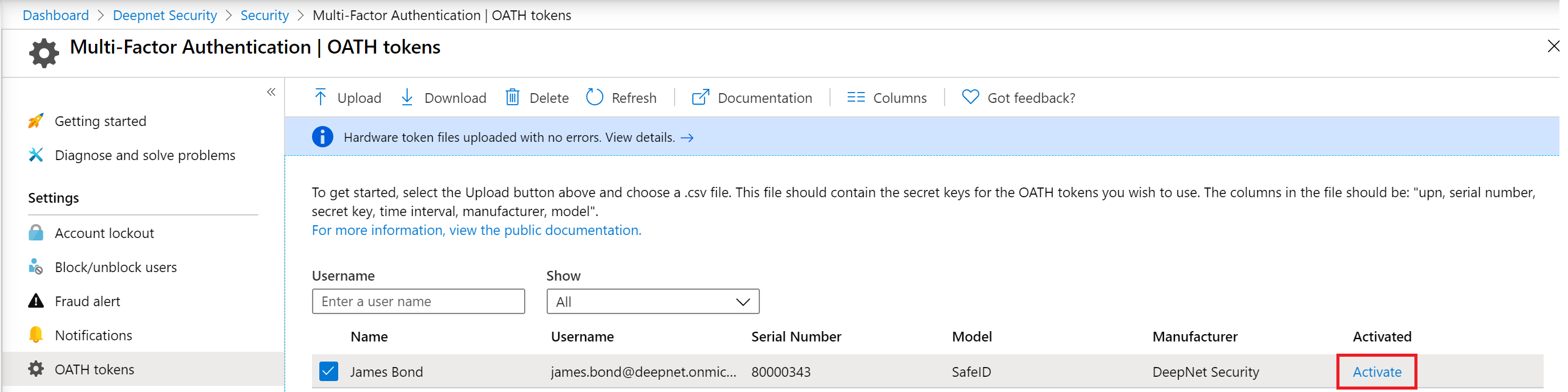
Once the uploading process has been completed, the list of tokens will be displayed.
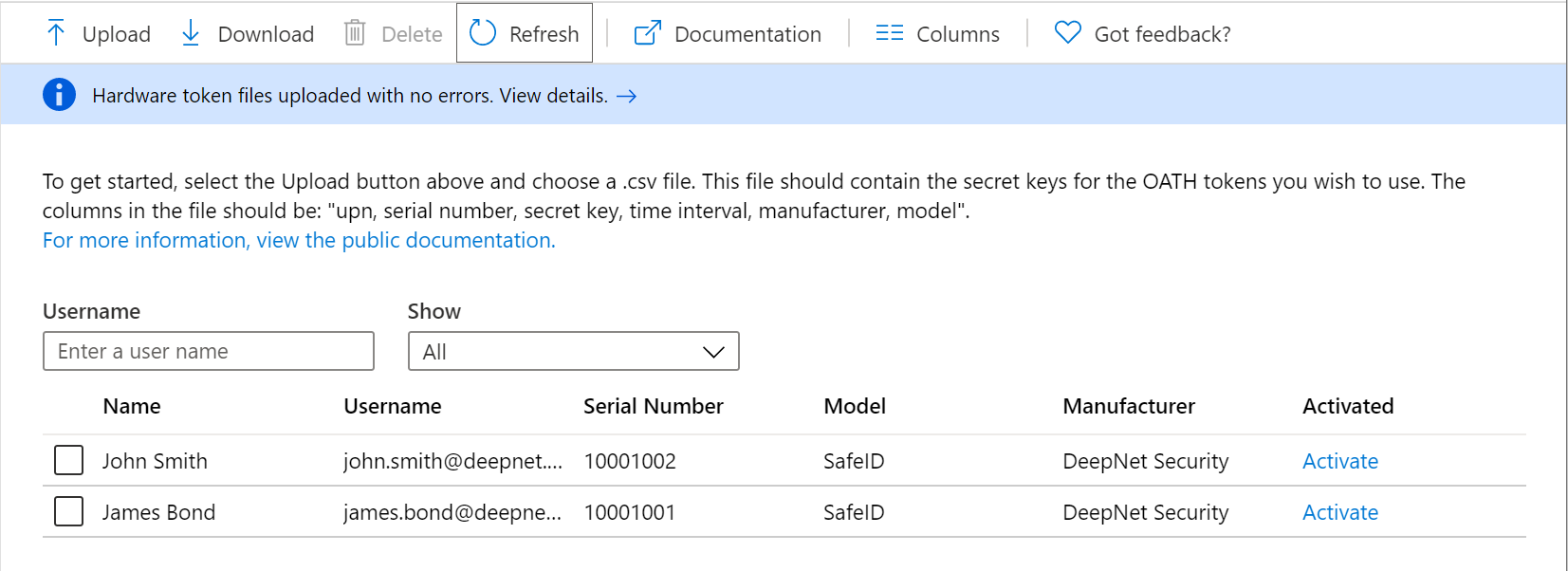
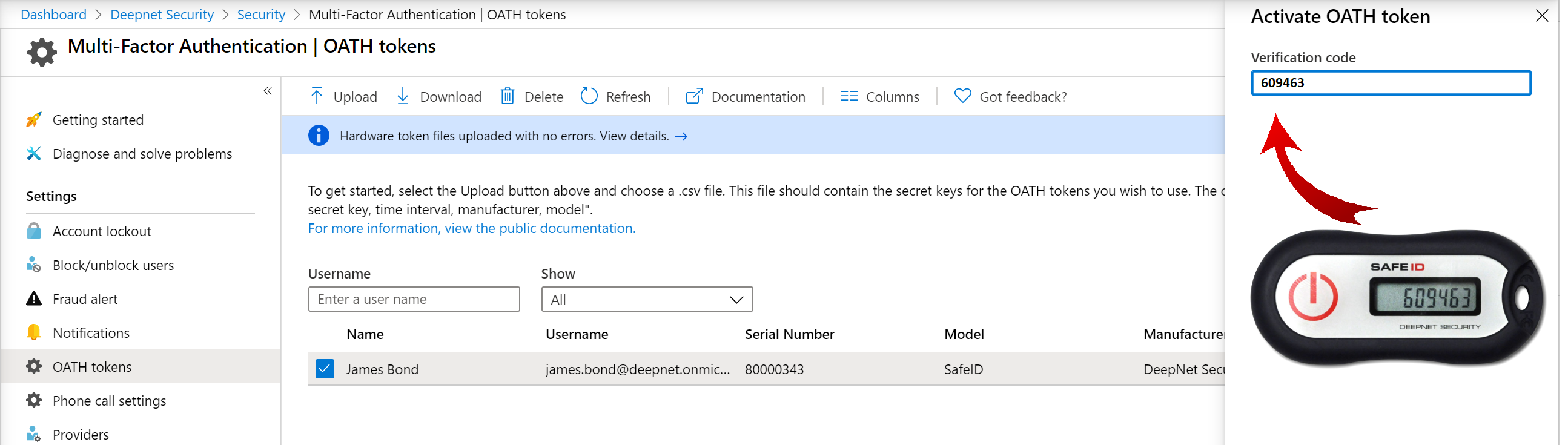
Activate Tokens
The administrator can activate each token by clicking Activate on the token to be activated and entering the passcode displayed on the token to verify
Related Articles
How to use SafeID Hardware OTP Token in Office 365 MFA login
How to set OTP token as the default sign-in method for Office 365 MFA login