OAuth 2.0 is a popular authorisation protocol that allows users to grant third-party applications access to their resources without revealing their usernames or passwords. It's a standard for secure access to APIs and shared online resources.
OAuth 2.0 has four main flows or grant types. DualShield Authorisation server uses the Client Credential Grant Type and is typically used when the API endpoint is sitting on a reverse proxy Service.
There are a few key components:
Client Application: This is the application that wants to access a protected resource. In our case this will be DualShield Frontend agents such as SSO, the Self-Service Consoles, Windows Logon Agent, DualRadius Server. Authorisation Server: The server that authenticates the Client and issues access tokens (e.g DualShield Authentication server) Resource Server: The API or service the client wants to access, using the access token (also DualShield Authentication Server) Access Token: A credential issued by the authorisation server that the client uses to access protected resources. Typically a JWT (JSON Web Token) consisting of an authorisation bearer header. Proxy Server: Acting as an intermediary between a client and another server |
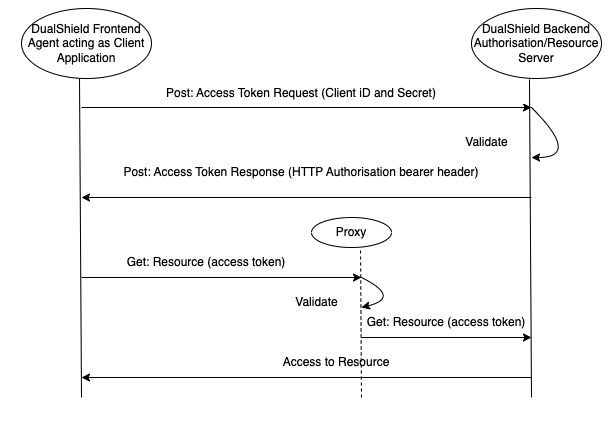
The client application (DS Frontend agent) requests an access token. To receive this token, the client posts an API call to the authorisation server (DualShield Backend). This API call will include values of the Client ID and Client Secret.
Once the authorisation server has validated this request, it will send an access token back to the client.
The Client now sends an API call (request) to the Proxy gateway. The API call will contain the Access token with the bearer header.
The Proxy server validates the access token and forwards the request to the Resource Server (In this case, DualShield backend is also the resource server)
The Resource server responds with the requested resource.
