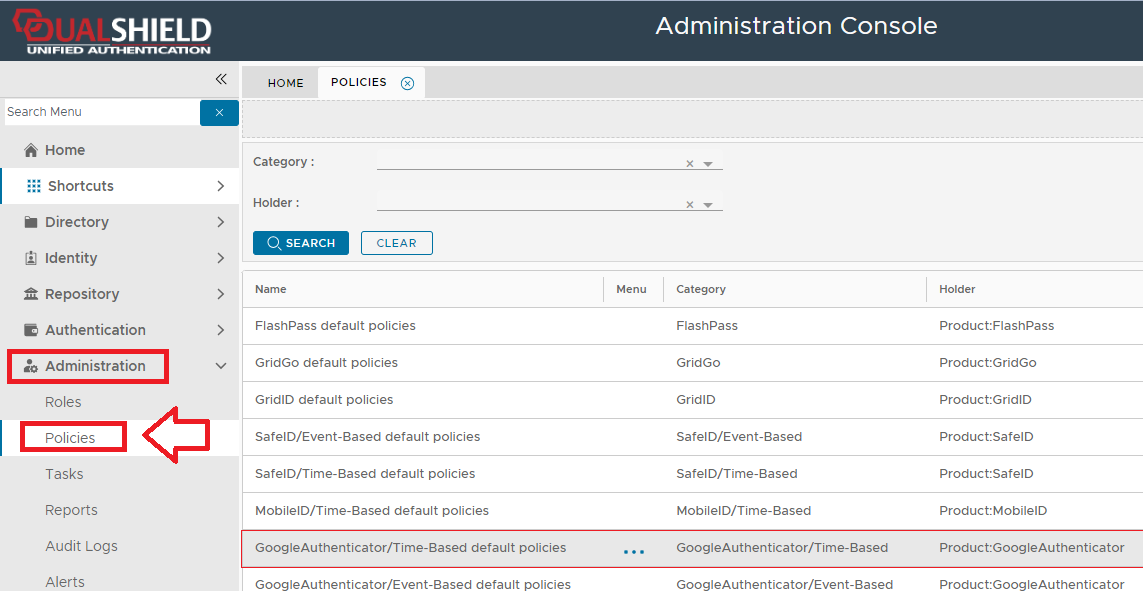
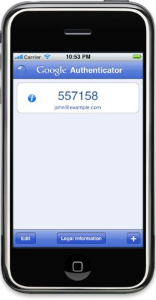
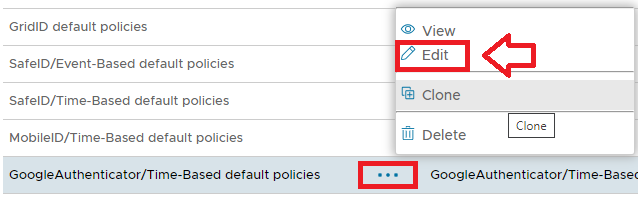
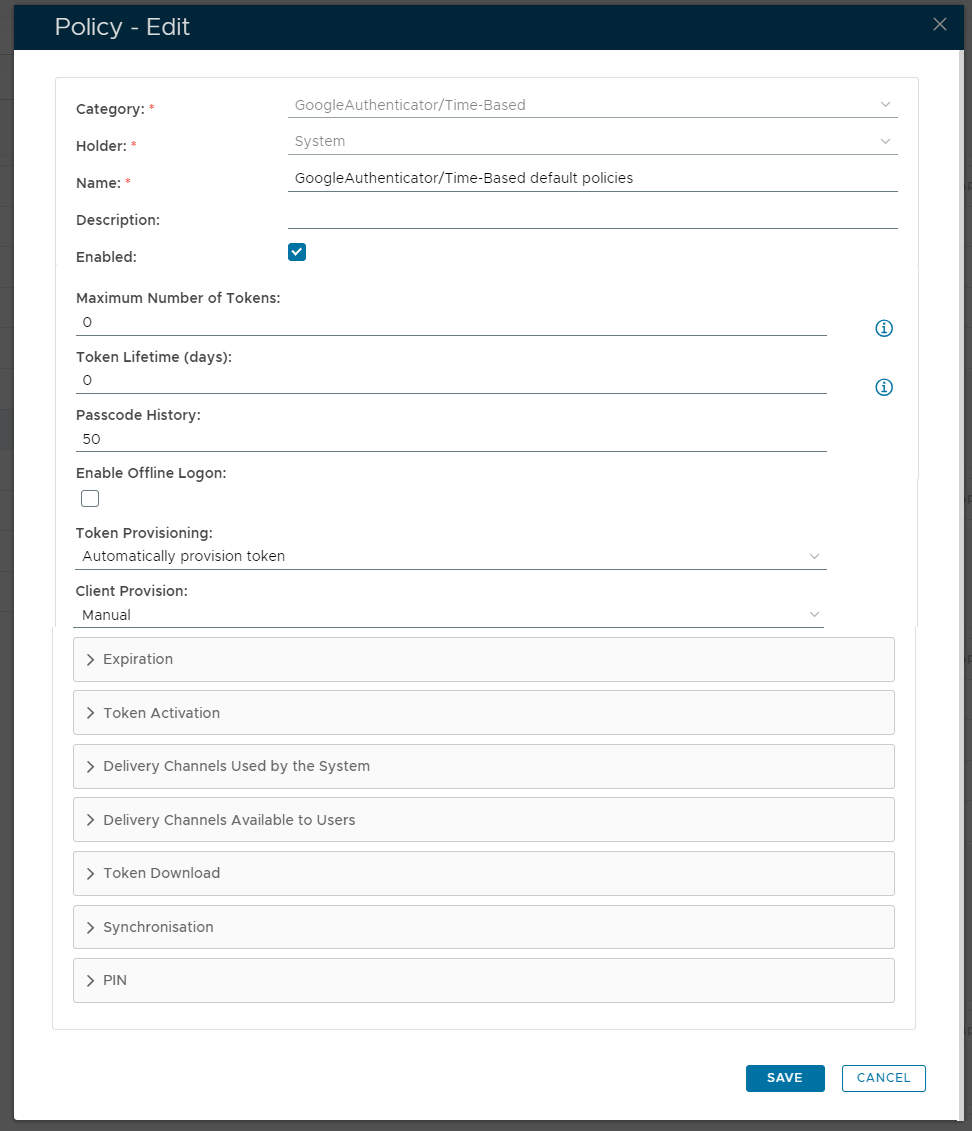
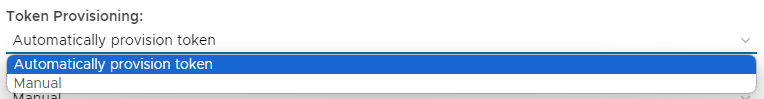
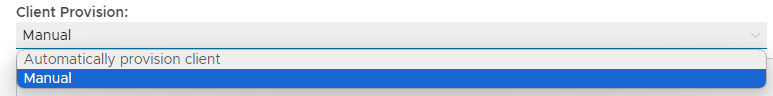
IntroductionSimilar to the Deepnet MobileID, Google Authenticator is an OATH compliant One-Time Password generator. Google Authenticator is officially available on iPhone, Android and Blackberry. Deepnet DualShield authentication server natively supports Google Authenticator, in very much the same way that it supports Deepnet MobileID. This document describes how users can use Google Authenticator with DualShied. This policy provides options that control Google-Authenticator/Time-Based Authentication (another OATH compliant One-Time Password generator that works in a similar fashion to MobileID); The following system policy settings are for the policy "GoogleAuthenticator/Time Based default policies", in the category "GoogleAuthenticator/Time Based"; |
|