Sign into Azure AD portal at https://portal.azure.com/
Click "Create a resource"
In the search box, enter "key vault" and then select "Key Vault" from the drop-down list
Click the "Create" button
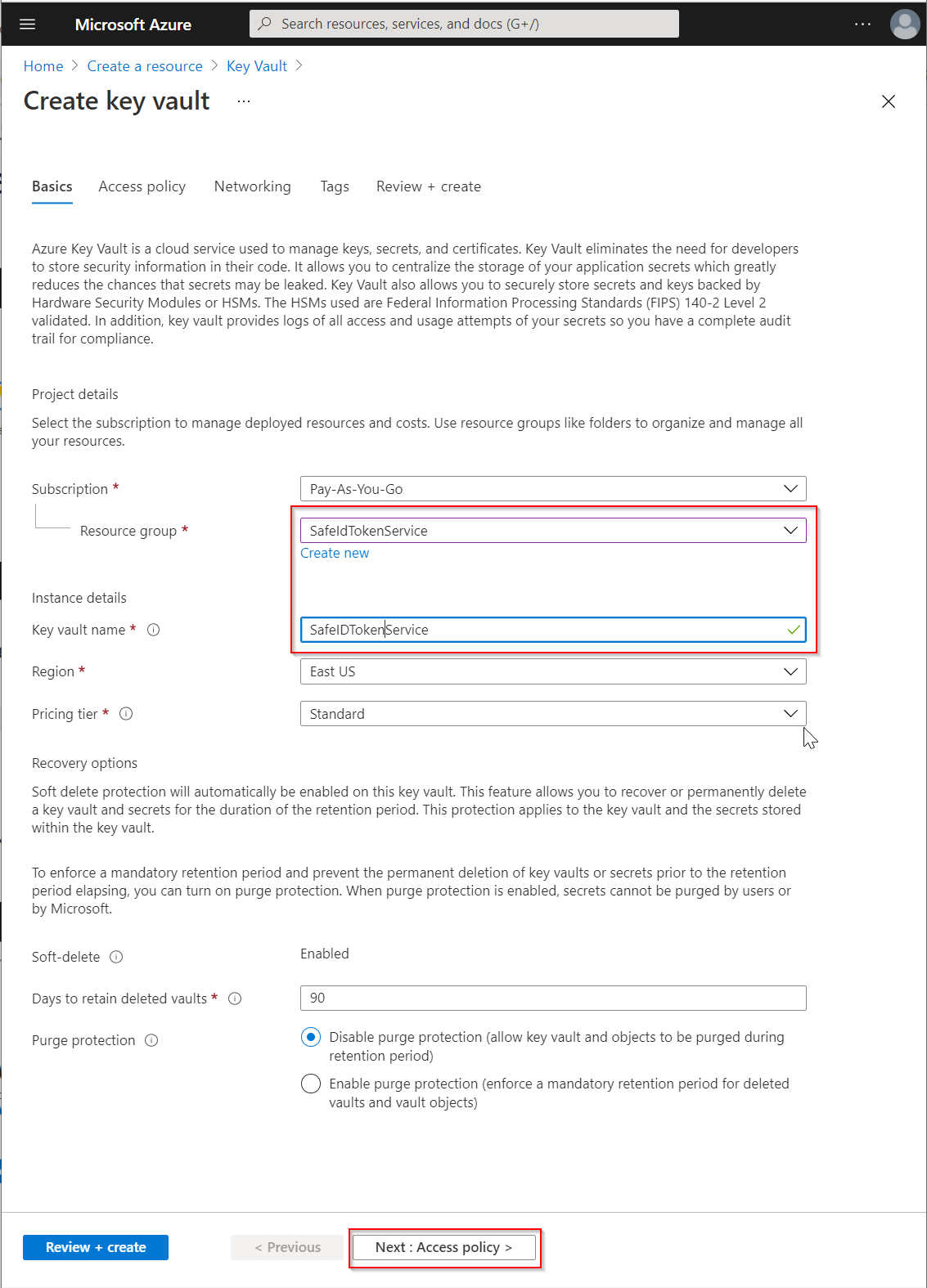
Select the Resource group that you have already created for SafeID Token Service, e.g. "SafeIdTokenService"
Enter the "Key vault name", e.g. "SafeIdTokenService"
Change other options if neccessary
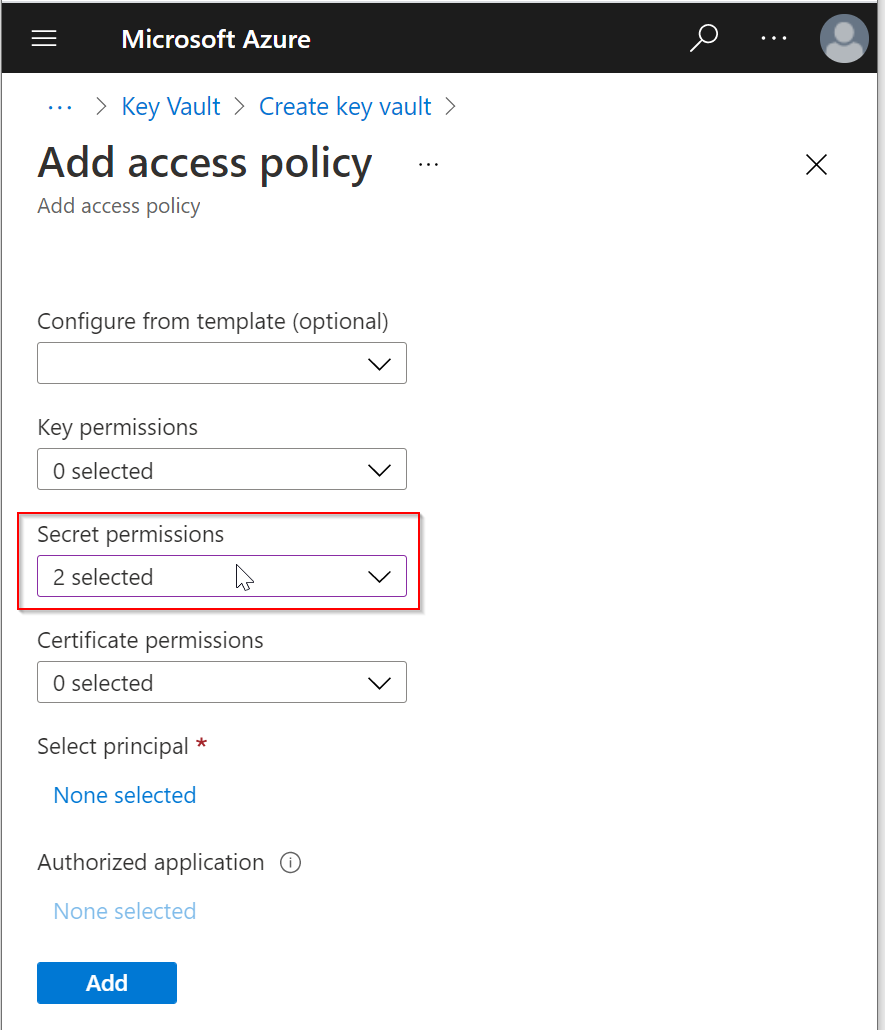
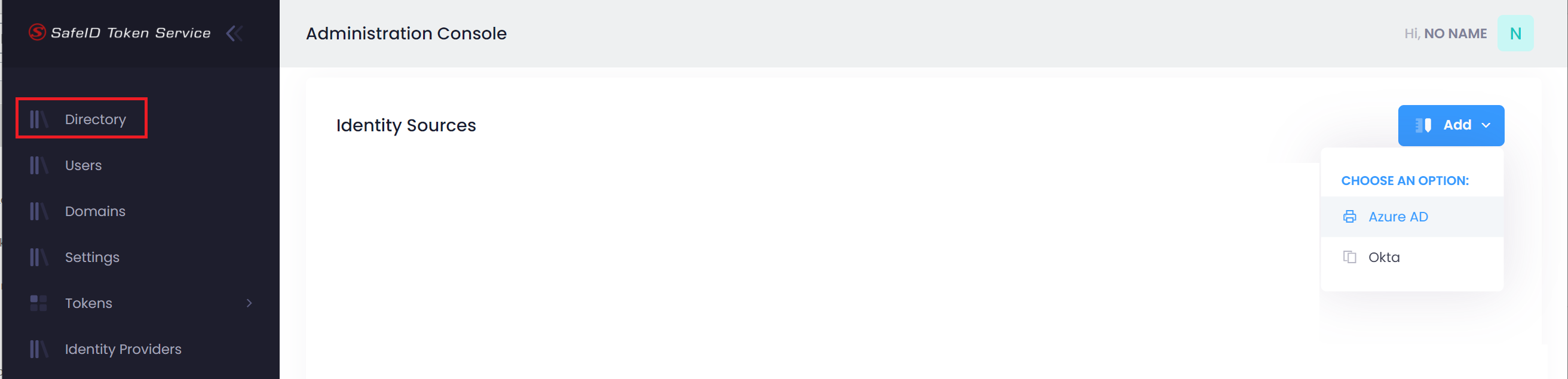
Click the "Access policy" button
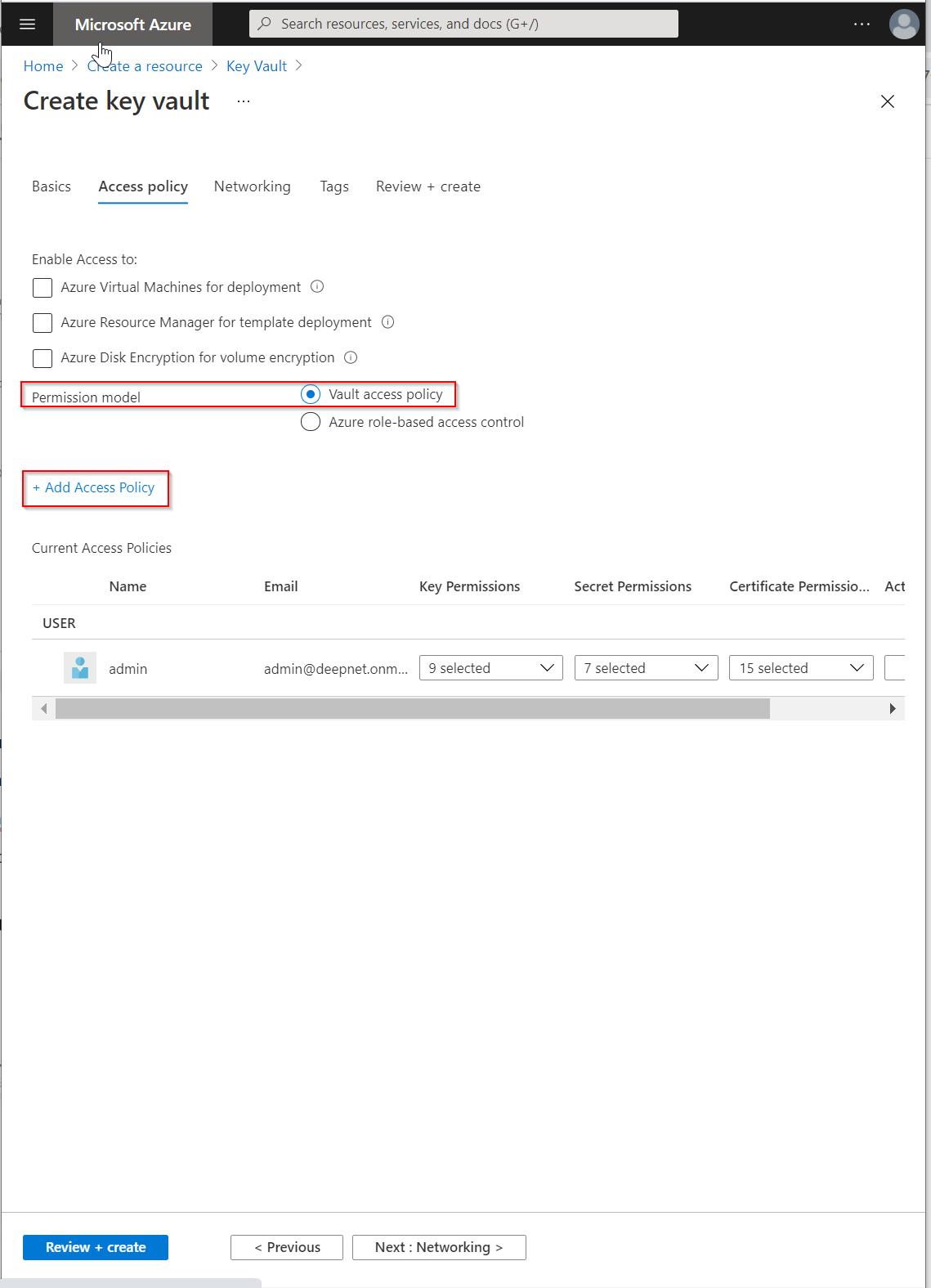
Make sure the "Permission model" is set to "Vault access policy"
Click "+Add Access Policy"
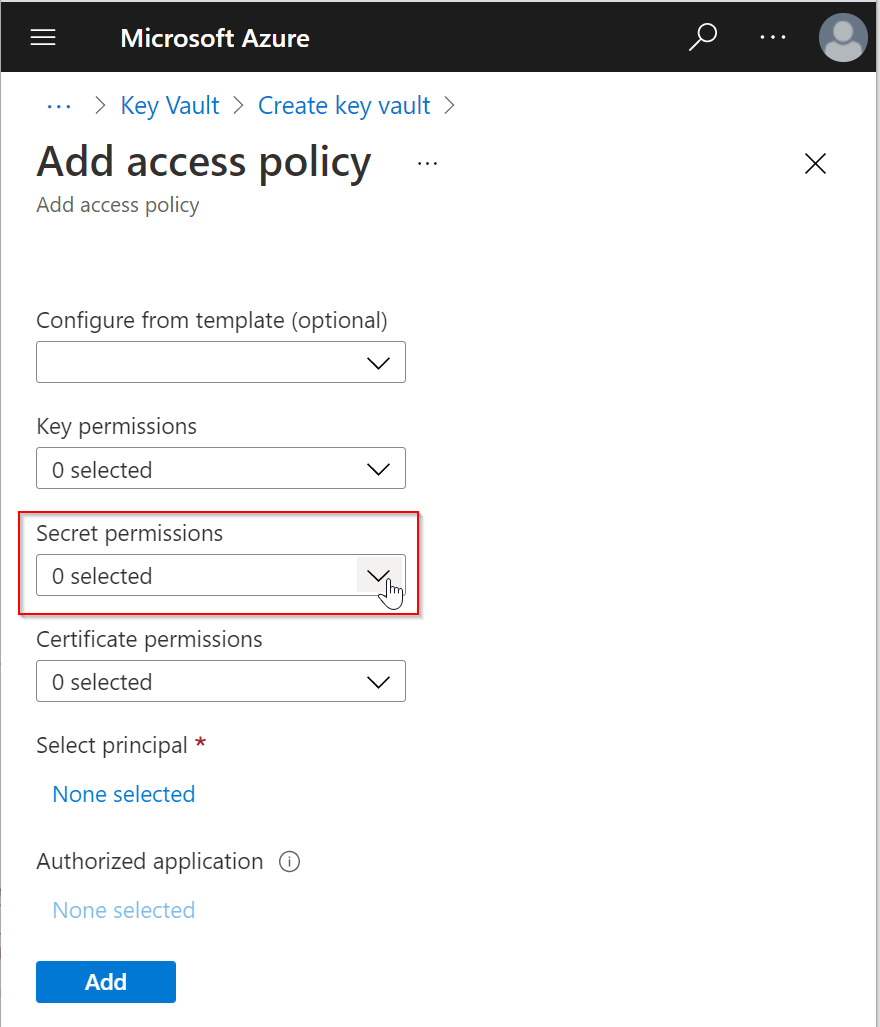
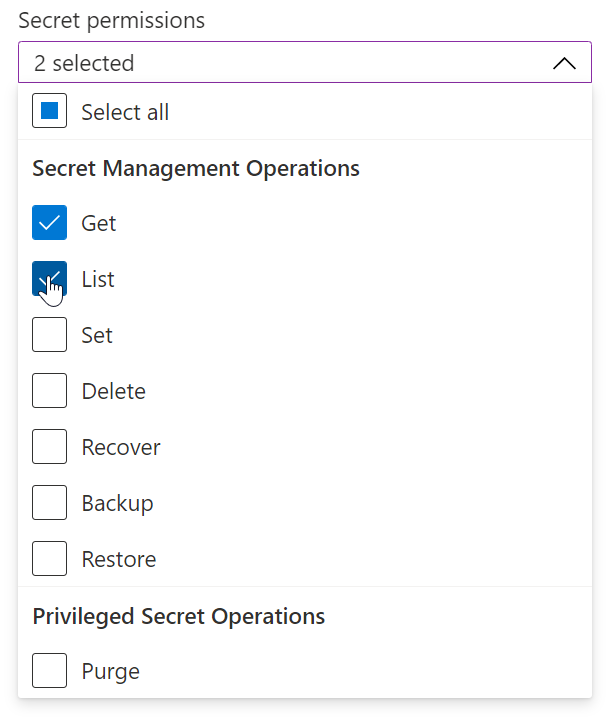
Click the down-down arrow on the right of Secret permissions, and then select "Get" and "List"
Click "None selected" under "Select principal"
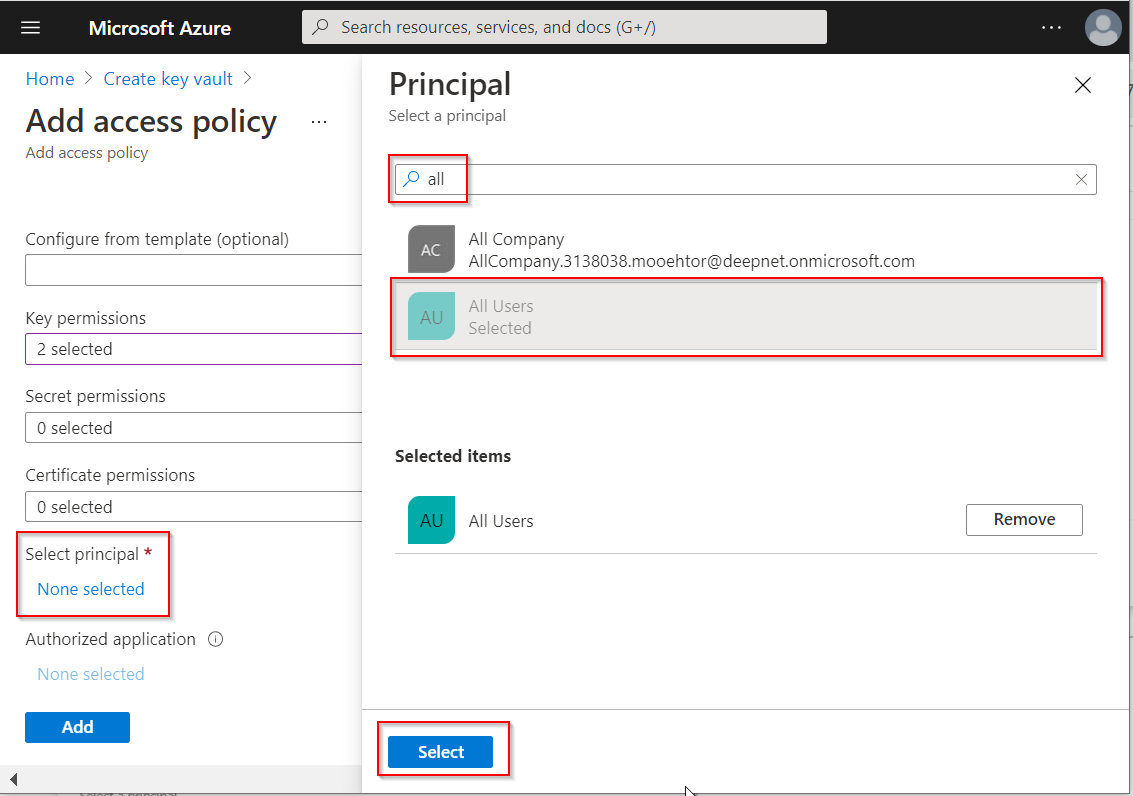
Enter "all" in the search box, and then select "All Users"
Click the "Select" button
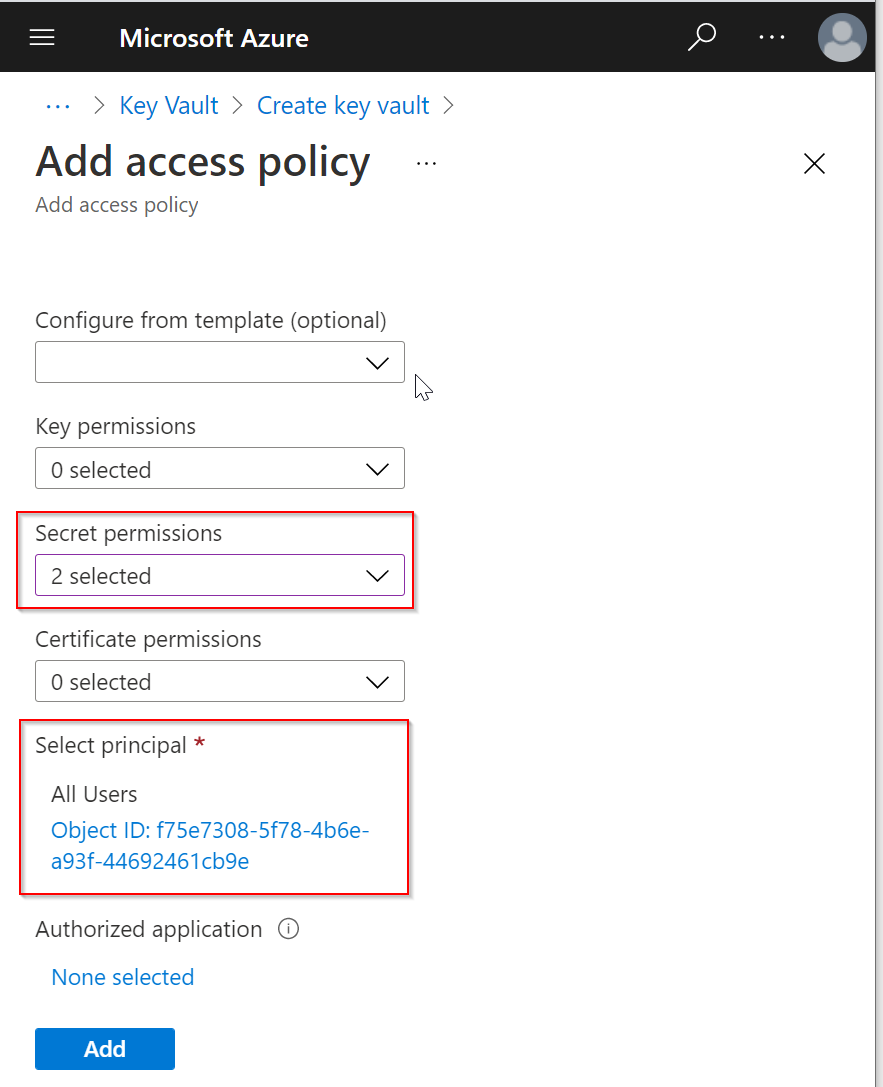
Click "None selected" under "Authorized application"
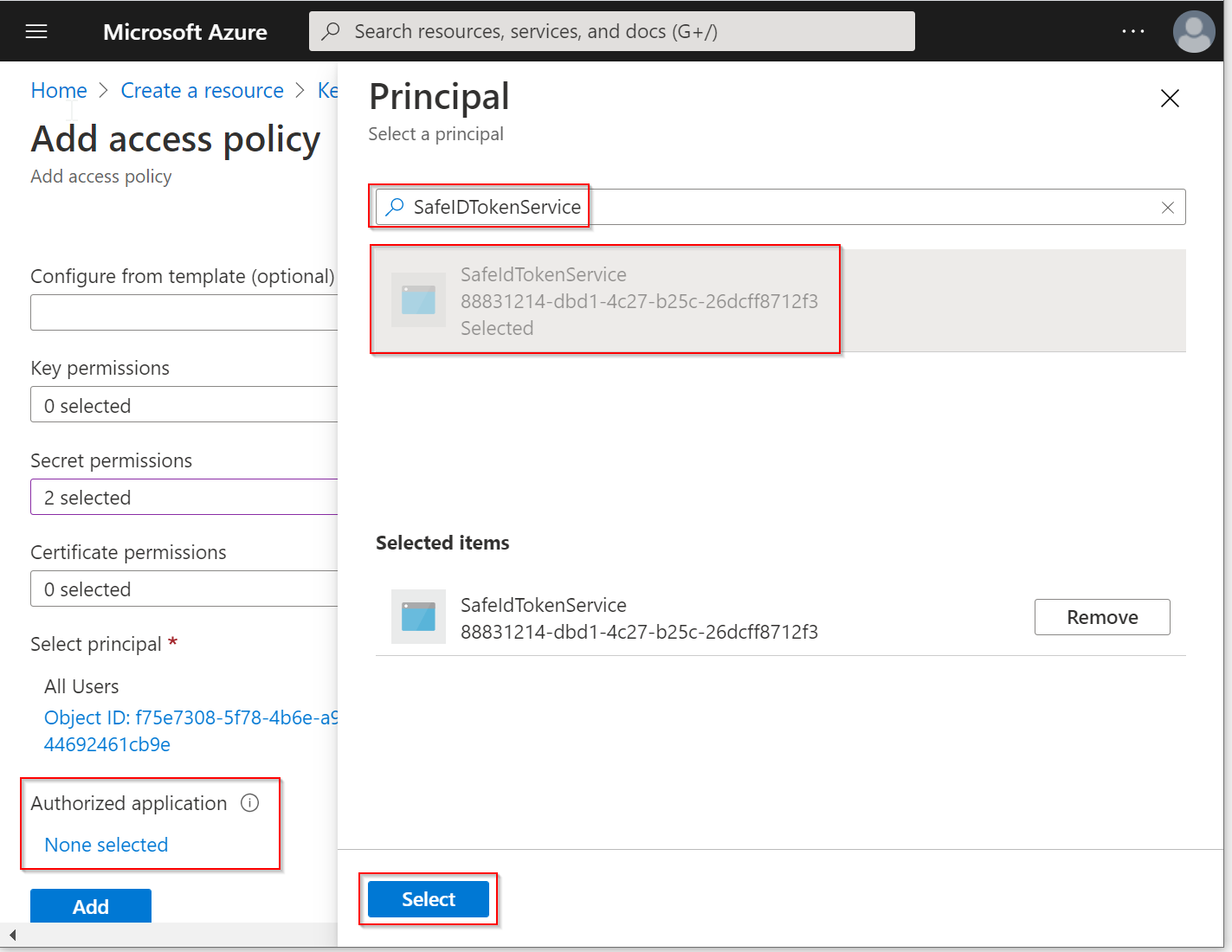
In the search box, enter the name of the application that you have previously created for STS, and then select it
Click the "Select" button
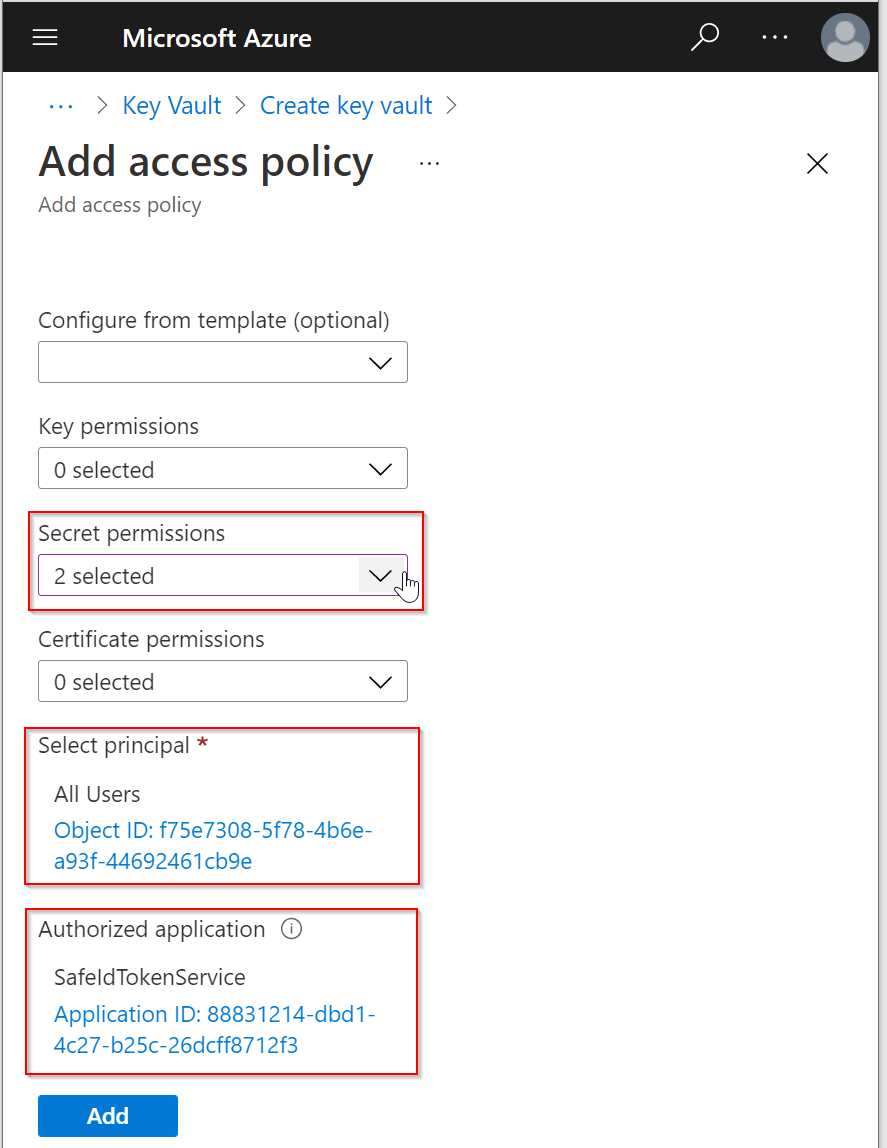
Now, click the "Add" button to add this new access policy
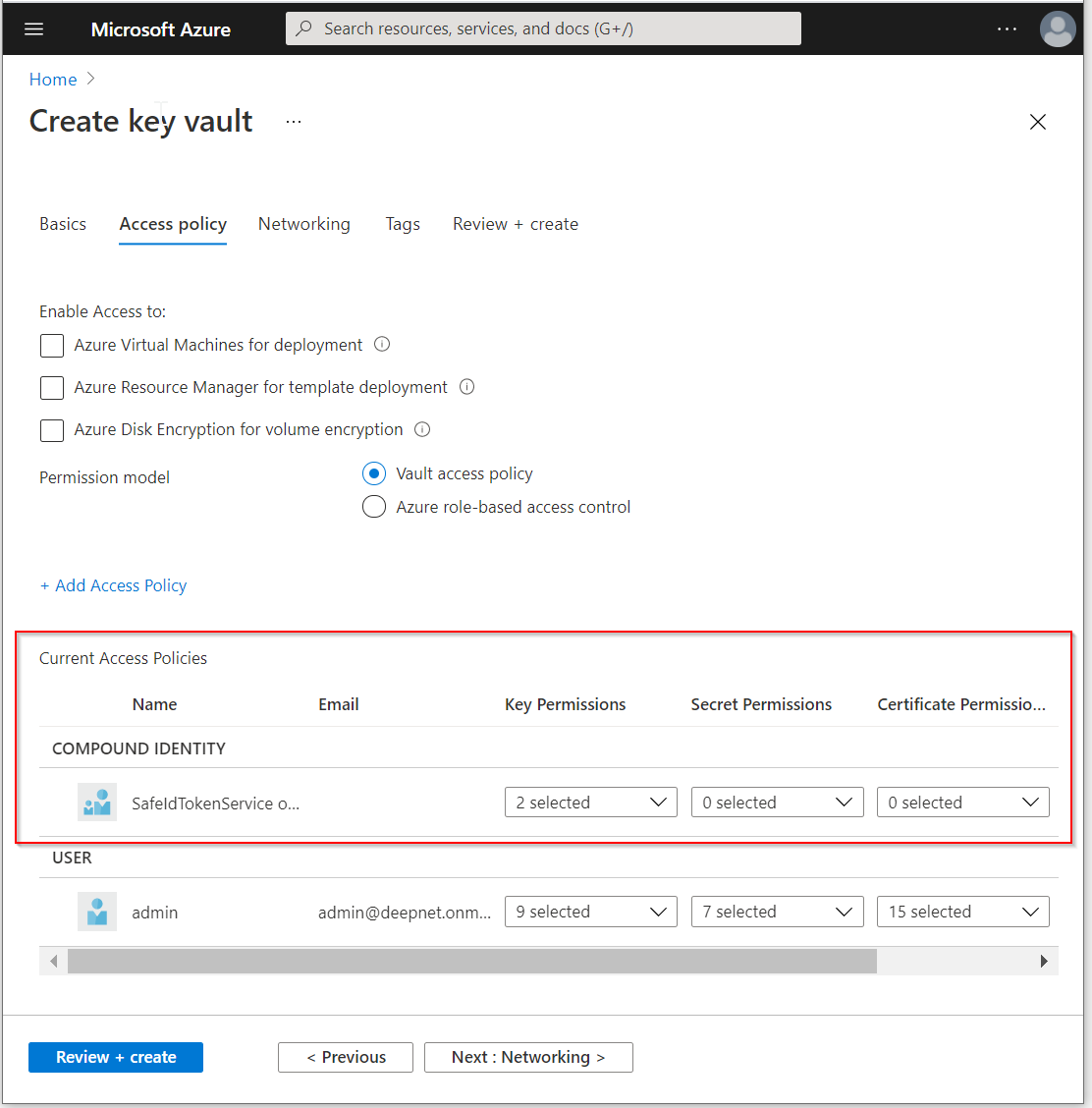
Click the "Review + create" button
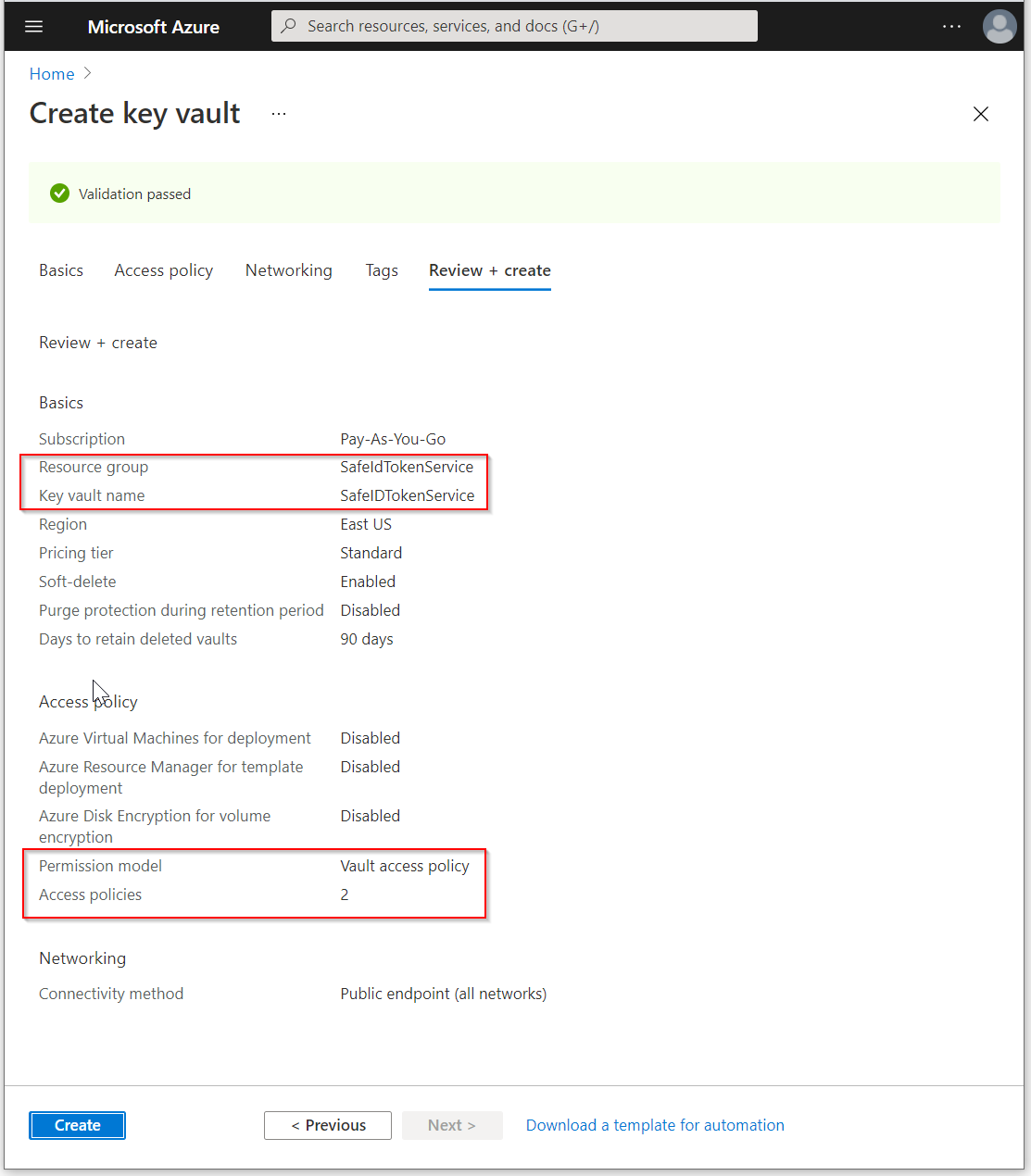
Review the settings, make sure all are correct
Finally, click the "Create" button to create a new key vault
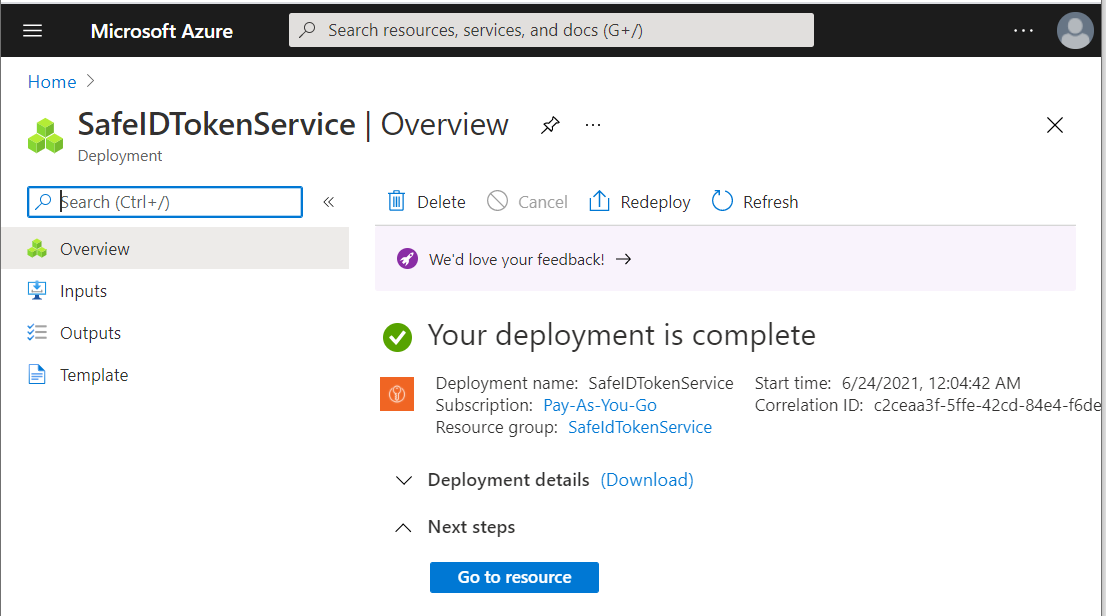
Wait until the new key vault has been successfully created.
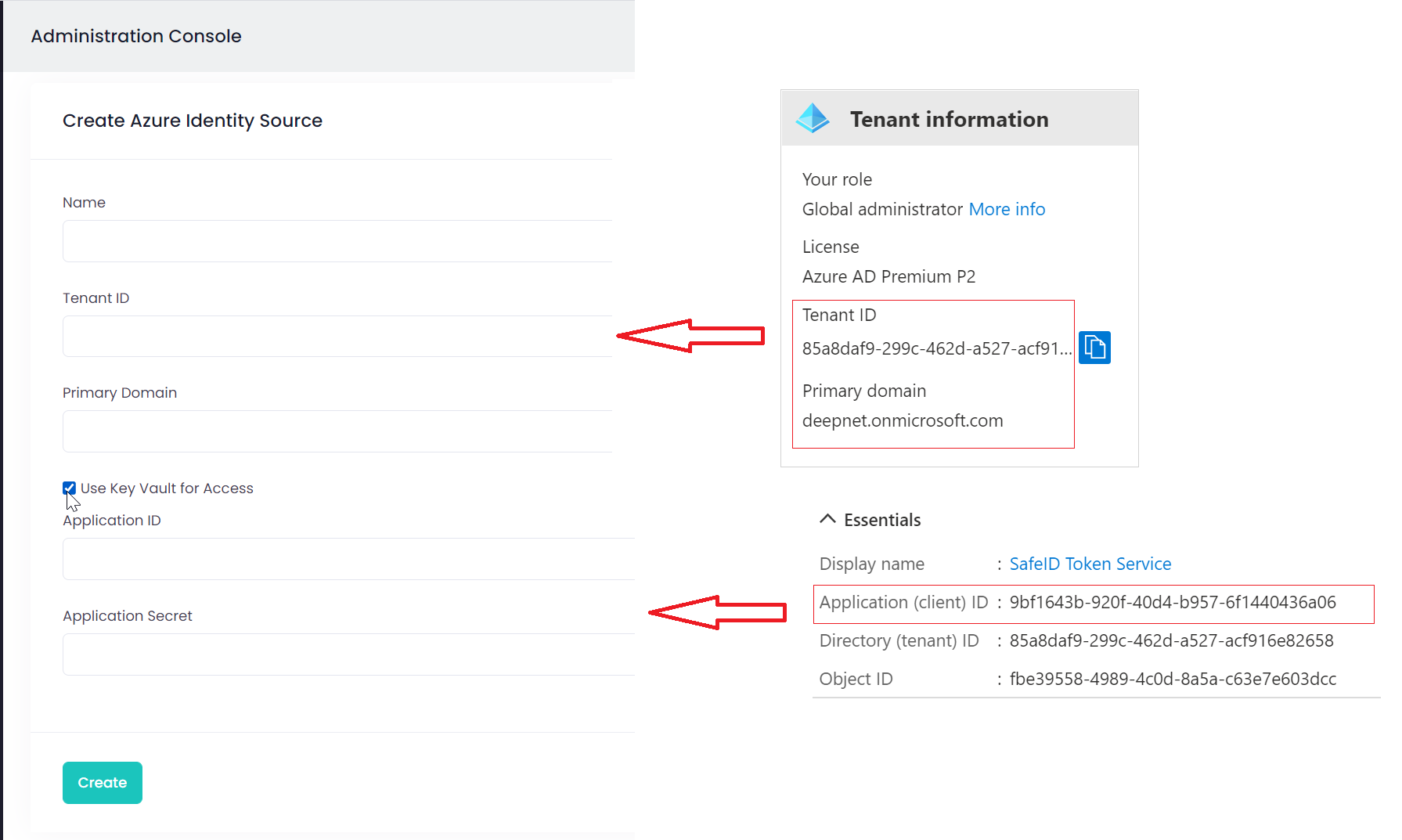
Now that the key vault has been created. We are going to save the username and passwords of the access user as secrets in the key vault.
Click "Go to resource"
Click "Secrets" on the navigation pane
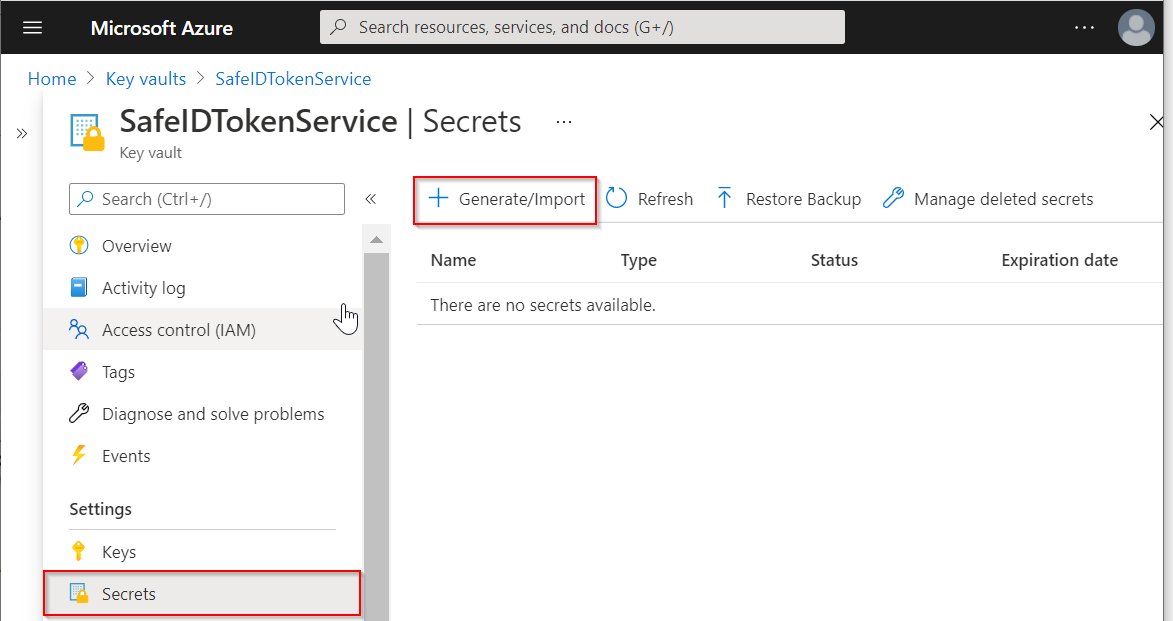
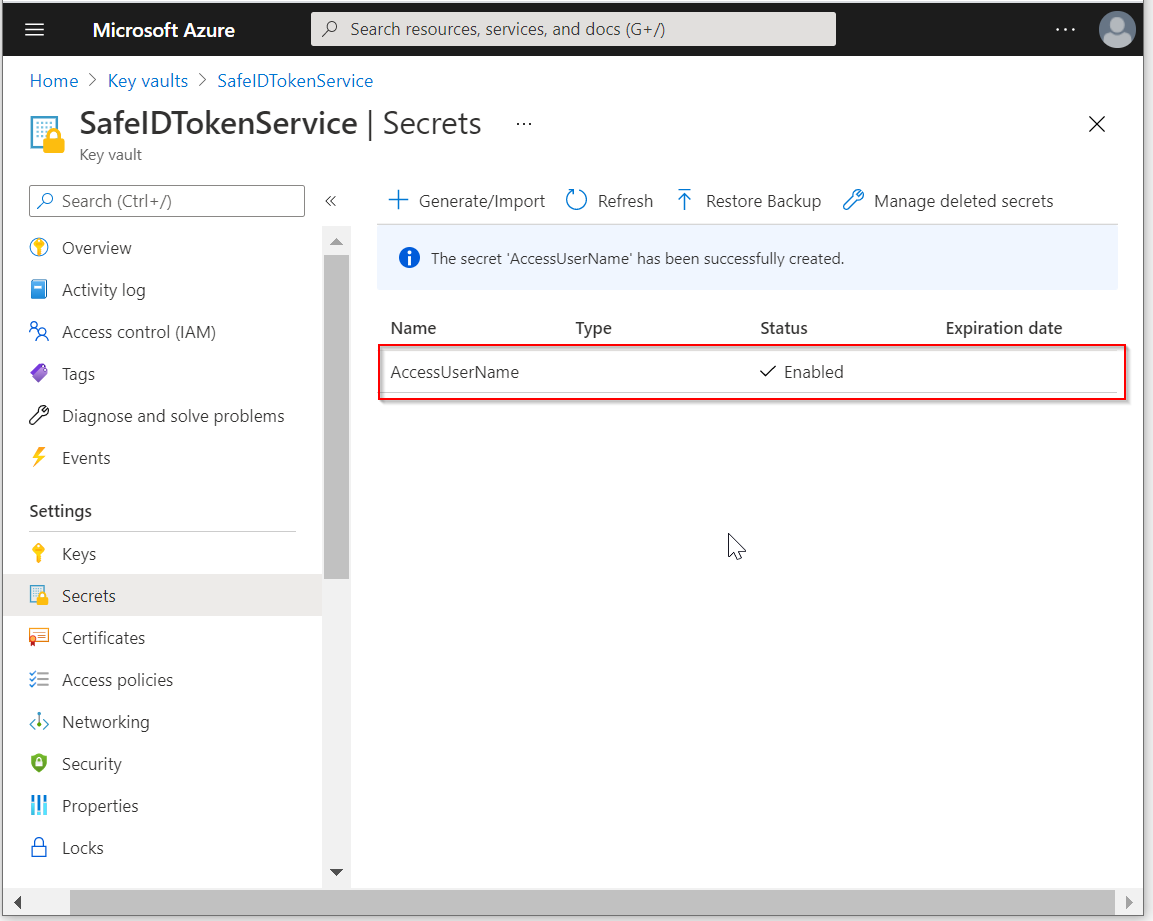
Click "Generate/Import" to create the first secret, i.e. AccessUserName
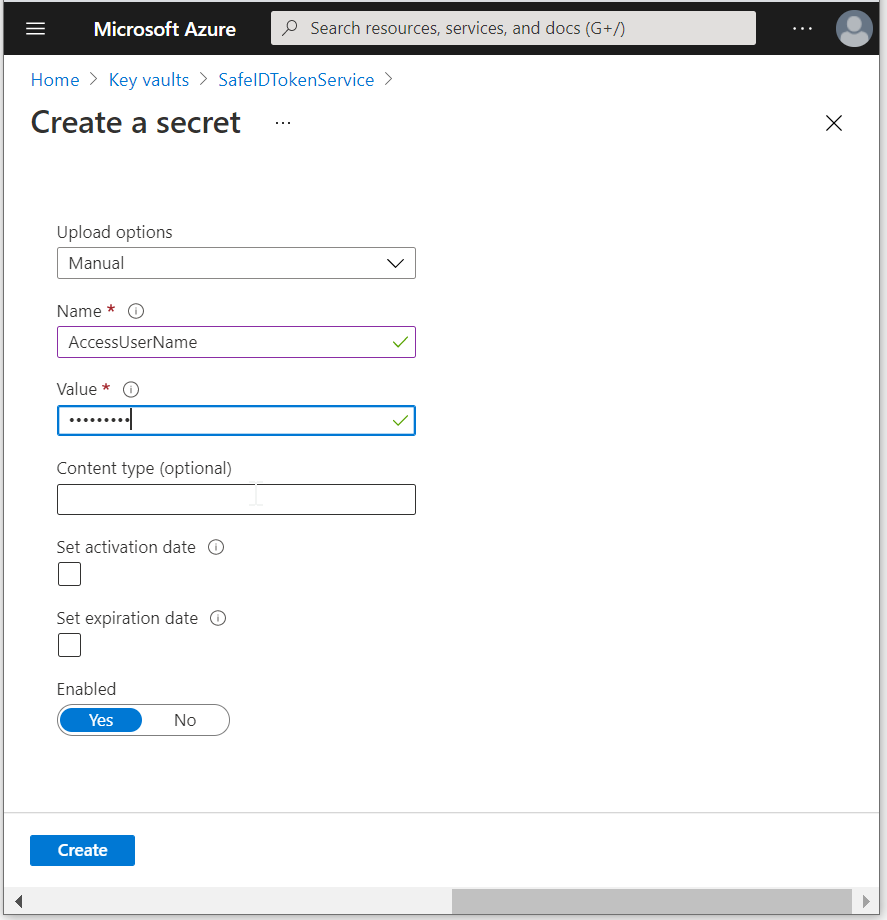
In the "Name" box, enter "AccessUserName"
In the "Value" box, enter the user name of the access user with global admin privileges
Click "Create"
Click "Generate/Import" again to create the second secret, i.e. AccessUserPassword
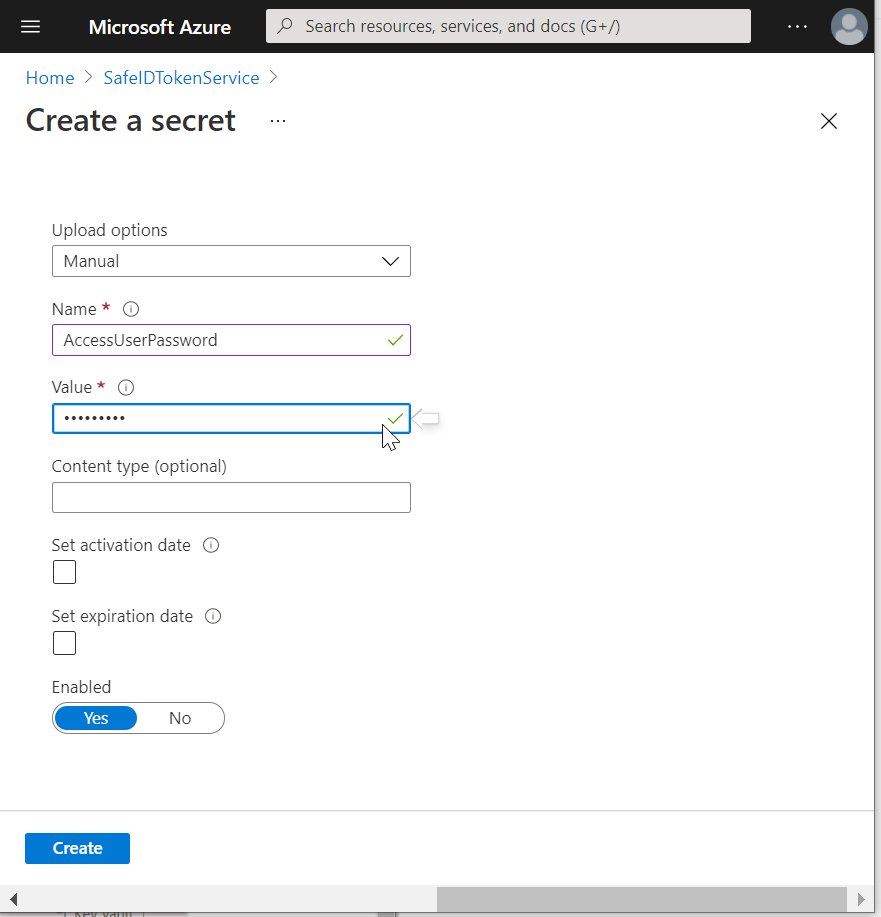
In the "Name" box, enter "AccessUserPassword"
In the "Value" box, enter the password of the access user with global admin privileges
Click "Create"
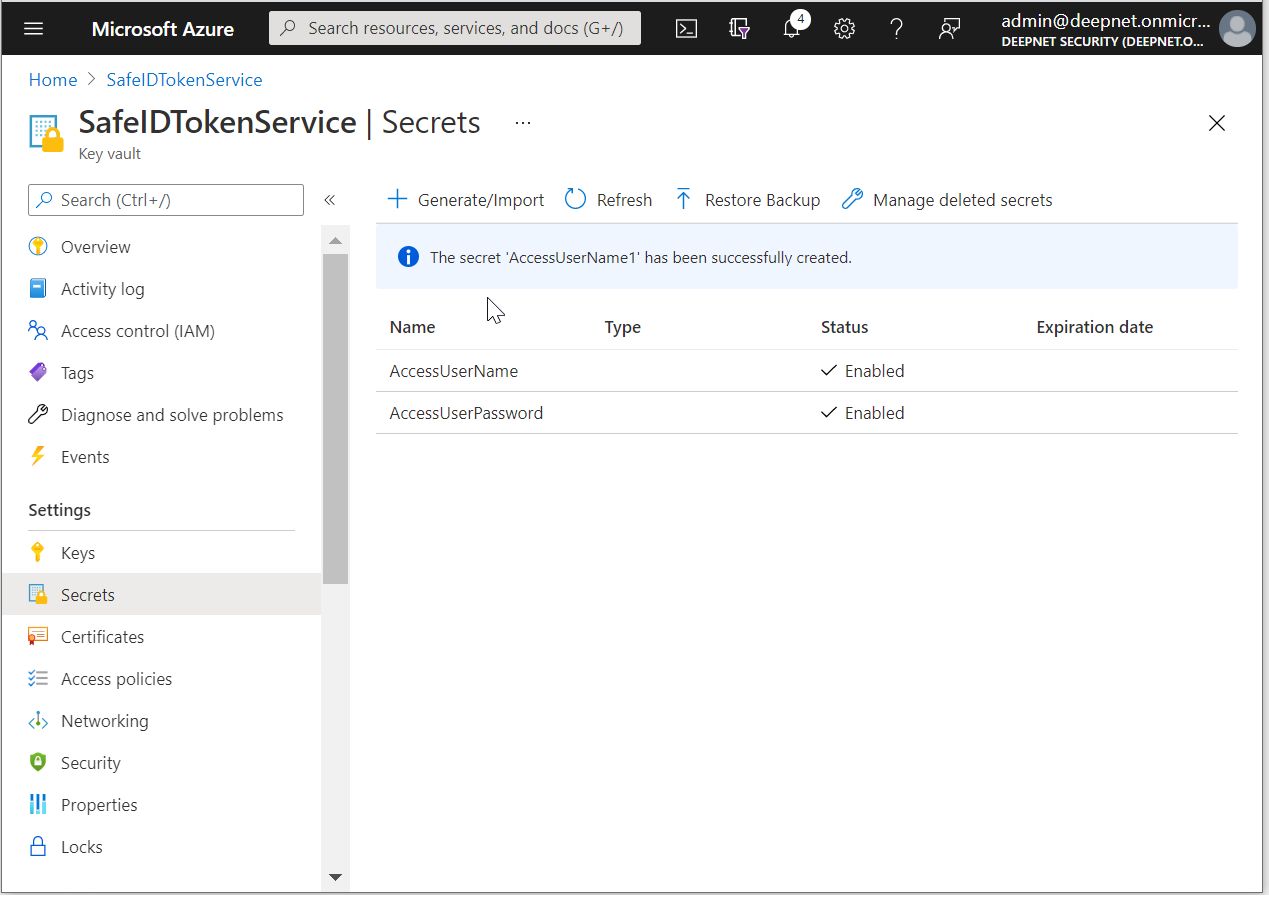
Click "Overview"
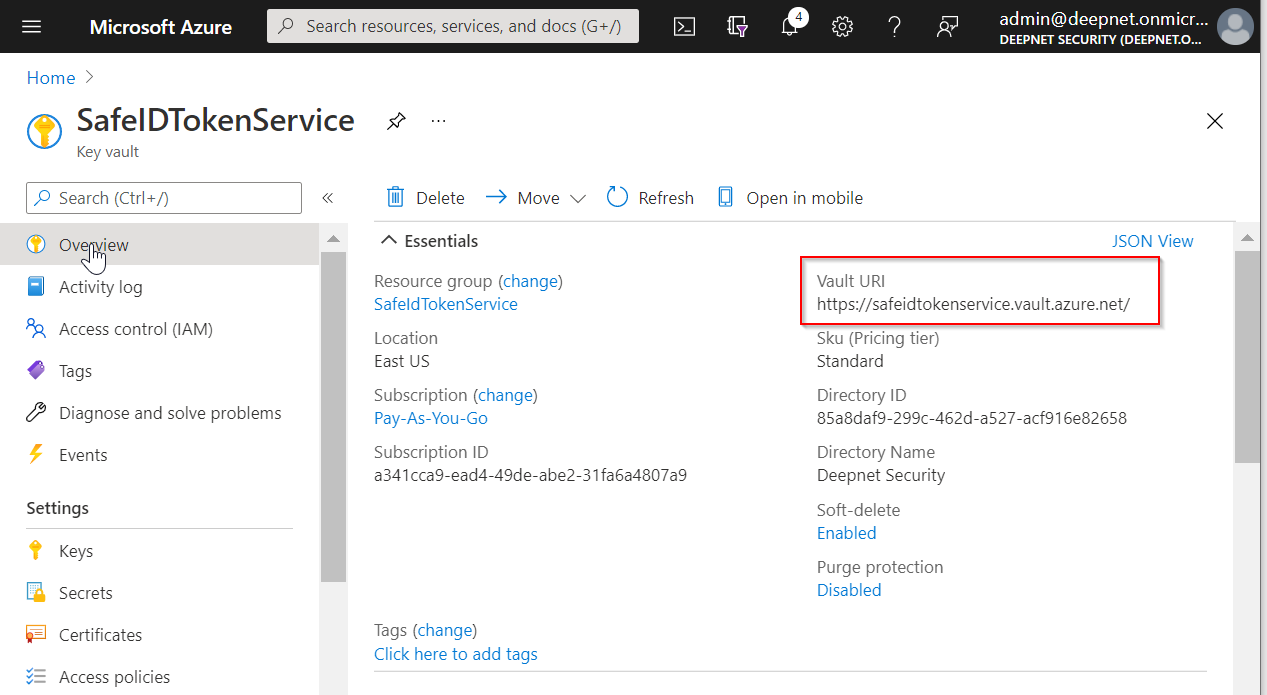
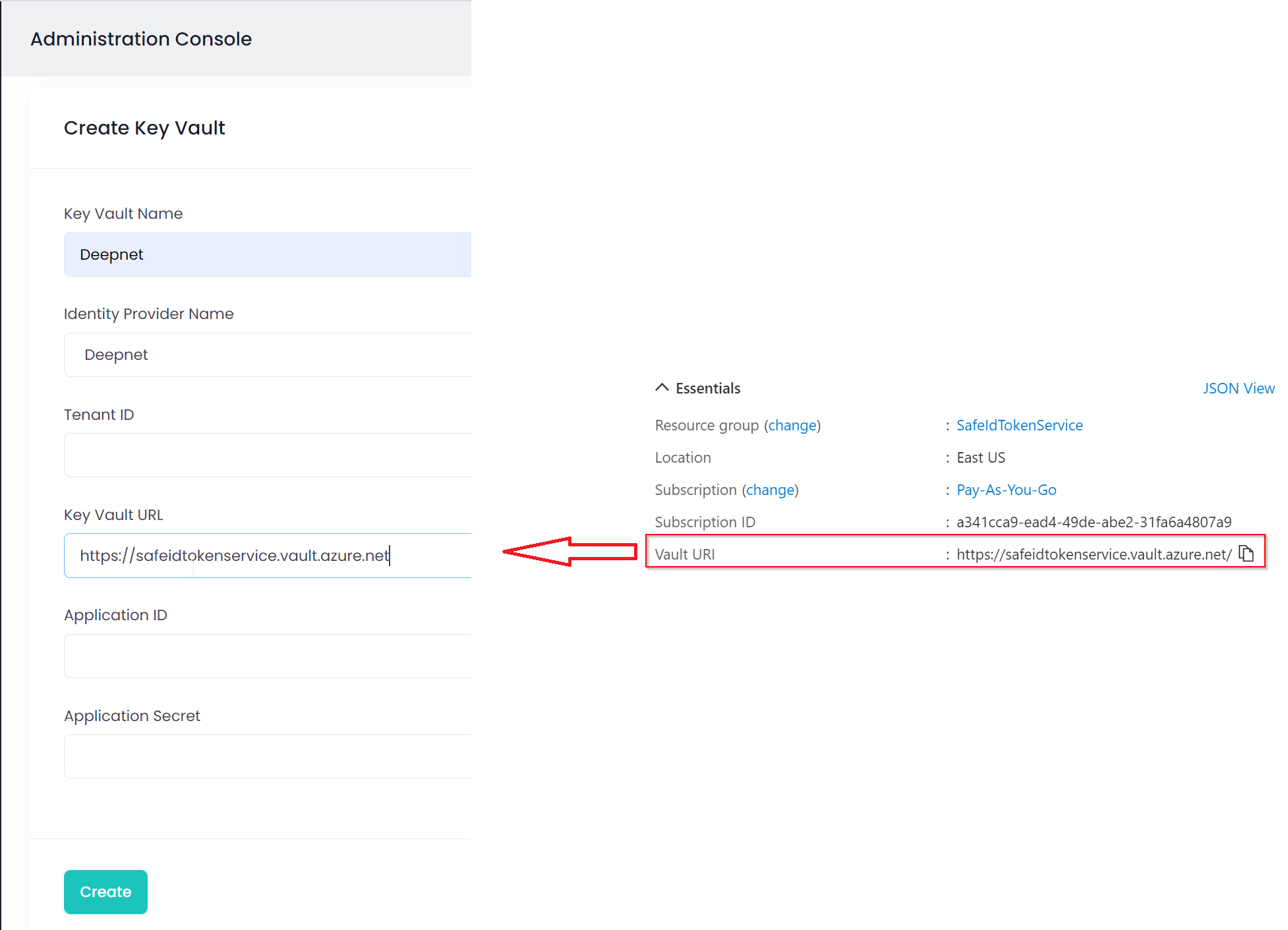
Finally, make a note of "Vault URI"