Both Azure MFA on-premises server and cloud service now support hardware tokens using time-based one time passcodes (OATH TOTP). Deepnet SafePass is a USB key that supports both FIDO and OATH OTP. It can be configured to generate time-based OTP, and used with Azure MFA.
First, administrators need to seed SafePass USB keys with TOTP tokens, then upload the token seeds onto the Azure MFA server. As the SafePass USB key does not have the display function, user will use the SafePass application to display OTP generated by the SafePass USB key.
In the Admin Tool folder, you will see a file named "tseed.csv"
This is the seed file in the format required by the Azure MFA cloud service.
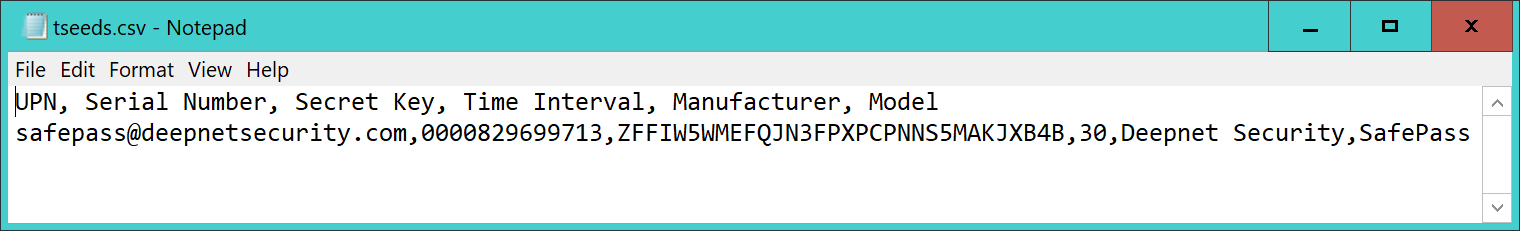
This file can be directly uploaded onto the Azure MFA cloud service.
Now, sign in to the Azure portal and navigate to Azure Active Directory, MFA Server, OATH tokens
Select "Upload" to upload the CSV file.
Depending on the size of the CSV file, it may take a few minutes to process. Click the Refresh button to get the current status. If there are any errors in the file, you will have the option to download a CSV file listing any errors for you to resolve.
Once any errors have been addressed, the administrator then can activate each key by clicking Activate for the token to be activated and entering the OTP displayed on the token.
To generate OTPs, the user will need to run the SafePass application.